Blue Pigeon: Bluetooth-based Data Exfiltration and Proxy Tool for Red Teamers
Blue Pigeon: Bluetooth-based Data Exfiltration and Proxy Tool for Red Teamers
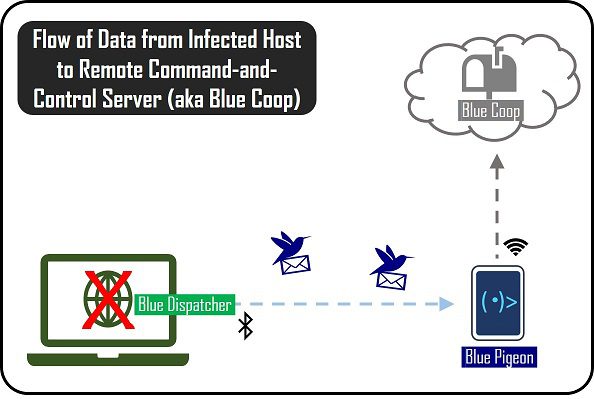
Blue Pigeon is a Bluetooth-based data exfiltration and proxy tool to enable communication between a remote Command and Control (C2) server and a compromised host.
Inspired by the Rock Dove‘s ability to carry messages back to its home, Blue Pigeon mimics the homing behaviour and delivers messages/payloads between the agent (compromised host) and its nest (mobile application and subsequently proxied to C2 server).
It is developed as an Android application for the Red Teamer to deploy within the vicinity of the compromised host and is particularly useful for Red Team operations where communications over traditional channels (i.e., web, e-mail, DNS) are not available.
Expanding on the “Exfiltration over Alternative Protocol” technique (ID: T1048) under the Exfiltration tactic of the MITRE AT&CK framework, Blue Pigeon provides a novel way of establishing Command and Control and performing data exfiltration as an Action on Objective of the Cyber Kill Chain by utilizing Bluetooth File Sharing as the exfiltration medium.
Establishing Command and Control and performing data exfiltration are key phases in the Cyber Kill Chain, but they often come with their complications and severe implications if done wrongly. In a Red Team operation, a misfired attempt could leave permanent traces in the network activity logs and raise alarm to the detection mechanisms.
In some of our Red Teaming exercises, we found ourselves in need of a way to exfiltrate data and communicate with the compromised host without having to go through the traditional channels (i.e., web, email, DNS).
With few solutions available to address this need we explored various exfiltration ideas based on wireless/radio-comms vectors. As a result, Blue Pigeon was created to expand our Red Team toolset.
How does Blue Pigeon work?
Blue Pigeon runs as a foreground service within an Android mobile phone. When the Red Teamer/Malicious Insider deploys the phone into proximity to the compromised host (infected with Blue Dispatcher payload), it will be able to serve as an exfiltration point and command relay proxy to a remote C2 server (a.k.a Blue Coop).
Install & Use
Copyright (C) 2021 @mahchiahui, @jingloon and @cloudkanghao





