Cloudflare tunneling client
AhnLab Security Emergency response Center (ASEC) has published a report detailing a significant shift in the tactics employed by the Bondnet threat actor. Traditionally associated with cryptocurrency mining operations, Bondnet has been observed leveraging compromised machines with high computational capabilities as clandestine command and control (C2) servers.

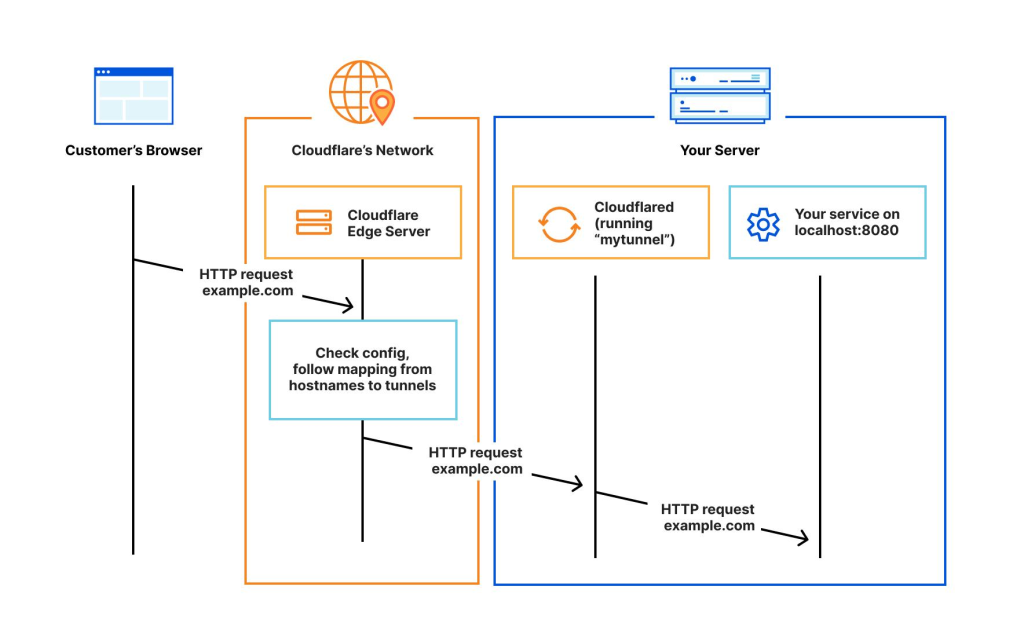
This novel approach, first identified in 2023, demonstrates the group’s increasing technical sophistication and adaptability. ASEC’s analysis reveals that Bondnet modifies an open-source proxy program, FRP, to establish reverse Remote Desktop Protocol (RDP) connections on these compromised systems. This process is facilitated through the use of proxy servers and Cloudflare tunneling, ultimately linking the targeted machine to Bondnet’s C2 domain.
While ASEC was unable to fully observe the conversion process due to environmental constraints on the affected system, the available evidence strongly suggests a deliberate attempt to establish a botnet C2 infrastructure. This conclusion is supported by the execution of Cloudflare tunneling and HTTP File Server (HFS) programs on the compromised machine, the distinctive user interface (UI) similarities between the HFS program and the Bondnet C2, and the observation of new and restored malicious files on the C2 following an initial failed attempt.
ASEC’s findings also indicate that Bondnet is specifically targeting systems with specific language settings (Russian, Korean, English, or Japanese) and substantial computational resources, likely prioritizing those that can best serve as robust C2 servers.
This revelation underscores the evolving nature of cyber threats and the continued importance of robust cybersecurity measures. Bondnet’s adaptation of its tactics highlights the need for organizations and individuals to remain vigilant and proactive in protecting their systems and data from increasingly sophisticated attacks.