bore v0.5 releases: modern, simple TCP tunnel in Rust
bore
A modern, simple TCP tunnel in Rust that exposes local ports to a remote server, bypassing standard NAT connection firewalls. That’s all it does: no more and no less.

# On your local machine
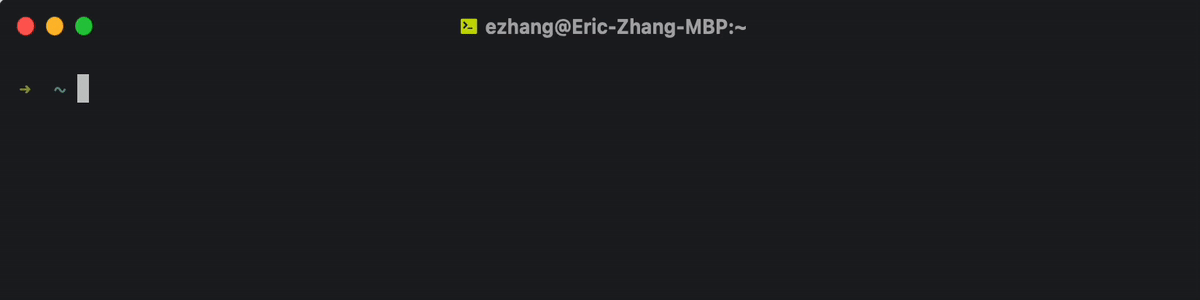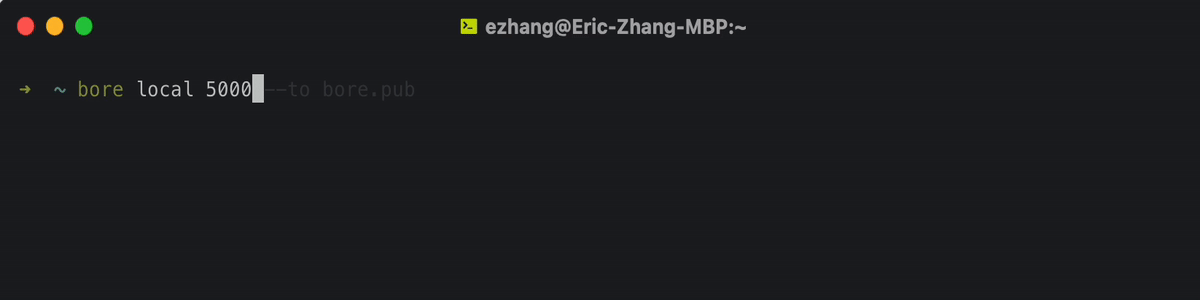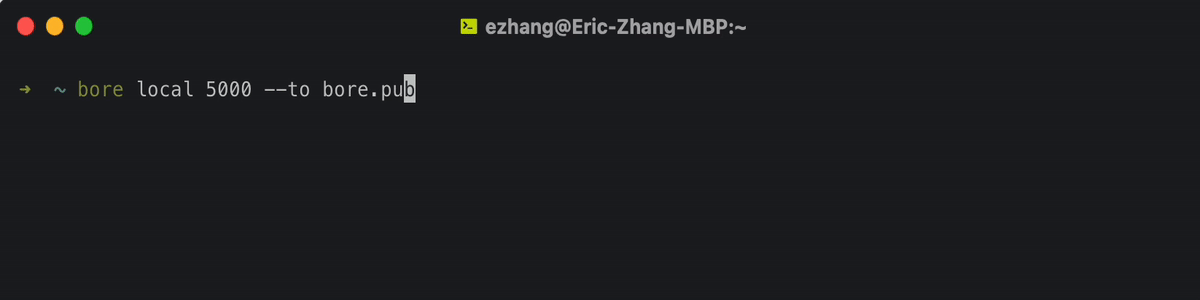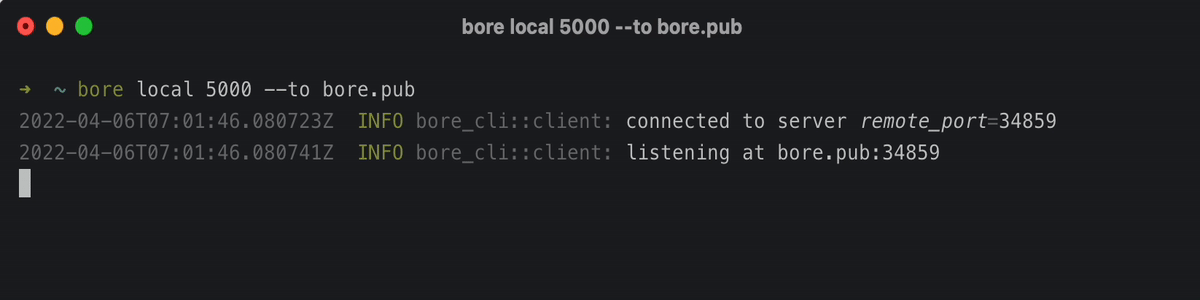
bore local 8000 –to bore.pub
This will expose your local port at localhost:8000 to the public internet at bore.pub:<PORT>, where the port number is assigned randomly.
Similar to localtunnel and ngrok, except bore is intended to be a highly efficient, unopinionated tool for forwarding TCP traffic that is simple to install and easy to self-host, with no frills attached.
(bore totals less than 400 lines of safe, async Rust code and is trivial to set up — just run a single binary for the client and server.)
Protocol
There is an implicit control port at 7835, used for creating new connections on demand. At initialization, the client sends a “Hello” message to the server on the TCP control port, asking to proxy a selected remote port. The server then responds with an acknowledgment and begins listening for external TCP connections.
Whenever the server obtains a connection on the remote port, it generates a secure UUID for that connection and sends it back to the client. The client then opens a separate TCP stream to the server and sends an “Accept” message containing the UUID on that stream. The server then proxies the two connections between each other.
For correctness reasons and to avoid memory leaks, incoming connections are only stored by the server for up to 10 seconds before being discarded if the client does not accept them.
Authentication
On a custom deployment of bore server, you can optionally require a secret to prevent the server from being used by others. The protocol requires clients to verify possession of the secret on each TCP connection by answering random challenges in the form of HMAC codes. (This secret is only used for the initial handshake, and no further traffic is encrypted by default.)
Changelog v0.5
This version changes the behavior of bore in relation to the --min-port option. Now, when a minimum port is specified, any user that connects to bore by default (port: 0) will pick a random port that respects the value of the option. Previously the min port was only used as validation when the user connected with an explicitly specified --port variable, and the OS was queried for a free port instead.
This also lets us add a --max-port option, which was requested by multiple people.
Install & Use
Copyright (c) 2022 Eric Zhang