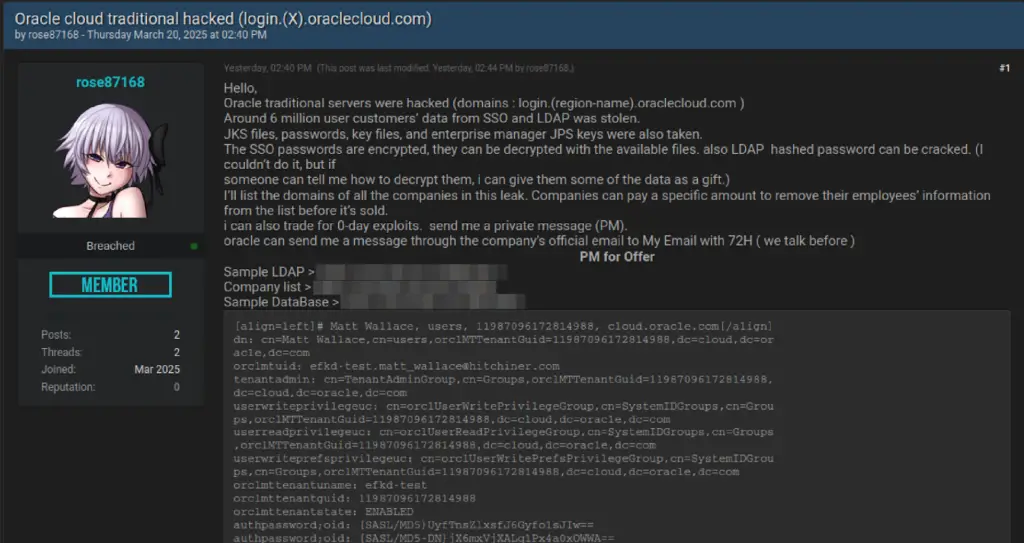
Threat actor listing 6M records exfiltrated from Oracle Cloud | Image: CloudSEK
A hacker recently posted on the BreachForums forum, claiming to have stolen customer security keys and other sensitive data from Oracle Cloud. The individual asserted that the data was obtained by exploiting a vulnerability to breach one of Oracle Cloud’s Single Sign-On (SSO) login servers.
Anticipating Oracle’s denial, the hacker reportedly planted evidence during the March attack. Specifically, a text file was created on Oracle’s login server under the domain login.us2.oraclecloud.com, and a snapshot of this file was captured using the Internet Archive’s Wayback Machine as proof.
The existence of such a snapshot suggests that the hacker did indeed gain access to Oracle’s login server—an act that would not be possible without compromising the system in some form. Despite this, Oracle stated after an internal investigation that no security breach had occurred on its platform, that the login credentials shared by the hacker were not applicable to Oracle Cloud, and that no customer had suffered a data compromise or intrusion.
Notably, the hacker was selling data that included Oracle Cloud customers’ email addresses, allegedly stolen from the EM2 and US2 login servers. As is customary, samples of the data were provided as proof.
The Wayback Machine snapshot revealed that, as of February 2025, the US2 Oracle Cloud server was running a variant of Oracle Fusion Middleware 11G.
Cybersecurity firm CloudSEK assessed that the server was likely left unpatched against CVE-2021-35587 – a known vulnerability in Oracle Access Manager within Fusion Middleware, which also involves the OpenSSO proxy component.
Prior to making the data public, the hacker reportedly demanded a ransom of $200 million from Oracle—a demand that was evidently refused. The stolen data allegedly includes security certificates and keys, encrypted SSO and LDAP passwords, JPS keys from Oracle Enterprise Manager, and additional extracted information.
The compromised database is said to contain approximately six million records, stored in Java KeyStore format. The actual number of affected users may be in the thousands, though Oracle has yet to release an official breakdown.
The hacker further claimed that while the SSO passwords are encrypted, they can be decrypted using existing files. Additionally, the hashed LDAP passwords are theoretically crackable, although the hacker admitted to being unable to do so personally and offered incentives to anyone who could assist in decrypting them.
Related Posts:
- S. Department of Justice seizes the hacker forum BreachForums’ domain
- Administrator of BreachForums pleads guilty and faces up to 30 years in prison
- CISA Sounds the Alarm on Actively Exploited Apple and Oracle Zero-Days
- Hackers target Oracle WebLogic Servers after the release of PoC code
- Oracle’s January 2025 Critical Patch Update: Addressing 320 Security Vulnerabilities