Buffer Overflow Vulnerability Services Tester Tool
BOVSTT – Buffer Overflow Vulnerability Services Tester Tool
Program to detect the existence of remote/local stack-based buffer-overflow vulnerabilities using the standard communication protocol for each service. The application allows to customize the testing mechanism of each service through templates, these templates are simply plain text files, which accept some kind of special words (see STF section), these files are stored in the folder with a direct association between the protocol and the template and with the extension STF (Service Tester File). Currently, the application version 2.5 supports the FTP, IMAP, POP3, and SMTP protocol. To carry out this task the application allows specifying different types of parameters.
In the presence of a Buffer Overflow Vulnerability in the computer, the attacker can exceed the normal length of the number of characters to fill a domain, usually the memory address. In some cases, these excess characters can be run as “executable” code. So that an attacker can not be bound by security measures to control the attacked computer. It is one of the most common means of attack, the worm on the operating system in high-risk vulnerabilities overflow speed and large-scale propagation are using this technology. Buffer overflow attacks in theory can be used to attack any defective imperfect procedures, including anti-virus software , firewalls and other security products, as well as attacks on the banks of the attack program.
Install
Requirements
- Platform: Microsoft Windows
- IDE: DEV-C ver-4.9.9.2
- Compiler: MinGW
- Dependences: Libwsock32.a (included in Dev-C++ IDE)
Download
git clone https://github.com/iricartb/buffer-overflow-vulnerability-services-tester-tool.git
Usage
BOVSTT.exe
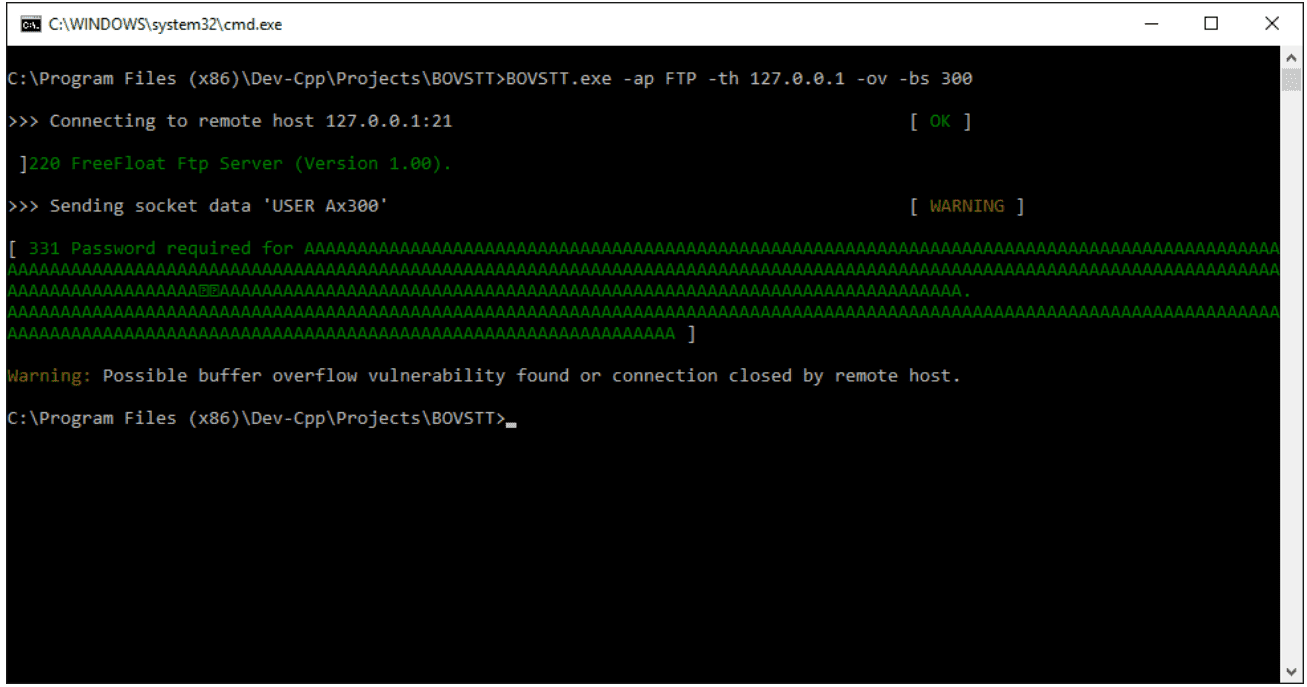
In the following screenshot, you can see how the program detects the existence of a buffer overflow
on the FTP service of the program FreeFloat FTP Server.
Source: https://github.com/iricartb/





