
In a recent report from Leandro Fróes, Senior Threat Research Engineer at Netskope, a new infection chain linked to the Bumblebee loader has been uncovered. First discovered by Google’s Threat Analysis Group in March 2022, Bumblebee is notorious for its ability to deliver other dangerous payloads such as Cobalt Strike and ransomware, making it a key tool in cybercriminals’ arsenal.
The latest findings mark the first known Bumblebee campaign since Operation Endgame, a massive takedown effort by Europol in May 2024 aimed at disrupting major malware botnets like Bumblebee, IcedID, and Pikabot. Despite this disruption, Bumblebee has returned with a new infection chain. “These activities might indicate the resurfacing of Bumblebee in the threat landscape,” the report stated, highlighting concerns among researchers.
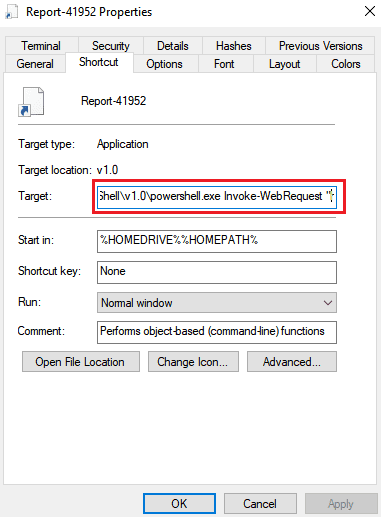
The infection typically begins with a phishing email containing a ZIP file. Once the victim extracts and executes the file, which is disguised as a legitimate LNK file named “Report-41952.lnk,” the malware infection process begins. The LNK file downloads a Microsoft Installer (MSI) file from a remote server, which then installs and executes the Bumblebee payload entirely in memory. By executing in memory, Bumblebee avoids the need to write the malicious DLL to disk, making detection much more difficult.
Using MSI files to deliver malware has become a common technique among cybercriminals. As Fróes explains, “The analyzed samples are disguised as Nvidia and Midjourney installers. They are used to load and execute the final payload all in memory, without even having to drop the payload to disk,” a method that significantly increases the malware’s stealth.
What sets this latest Bumblebee campaign apart is its advanced evasion techniques. Previous versions of Bumblebee relied on LOLBins (Living-off-the-Land Binaries) such as rundll32.exe and regsvr32.exe to load malicious DLLs. While effective, these methods created new processes that could trigger alerts for defenders. In contrast, this new campaign uses a more stealthy approach. Instead of creating new processes, Bumblebee loads the malicious DLL directly into the memory of the msiexec.exe process by exploiting the SelfReg table of the MSI file. This allows the malware to execute its payload without creating suspicious new processes.
Once the installation starts, the DLL is loaded into the msiexec process’s address space, and the malware’s payload is unpacked and executed. This approach leaves little trace behind, complicating the detection and analysis process for security teams.
The unpacked Bumblebee payload carries some familiar characteristics, such as a hardcoded RC4 key used to decrypt its configuration. In the samples analyzed by Netskope, the key was the string “NEW_BLACK”, which decrypted the configuration for port 443 and identified the campaign ID as “msi” and “lnk001.
As Fróes concludes, “From an attacker perspective, the downside of these approaches is that once any of those tools execute, a new process is created, opening the opportunity for defenders to flag unusual events.” Bumblebee’s stealthier approach indicates that cybercriminals are continuously refining their methods, and organizations need to be prepared for new threats on the horizon.
Related Posts:
- Cyber Alert: Bumblebee Malware Targets US Organizations
- Intel OEM Private Key Leak: A Blow to UEFI Secure Boot Security
- CVE-2024-36877 in MSI Motherboards Opens Door to Code Execution Attacks, PoC Published
- Researchers Detail CVE-2024-38014 0-Day Vulnerability in Windows MSI Installers Exploited in the Wild