Executing OutputDebugStringW from within LSASS | Image: Orange Cyberdefense
In July 2022, Microsoft made modifications to its Protected Process Light (PPL) system aimed at mitigating a vulnerability that allowed bypassing the protection of LSASS, a critical process responsible for storing and managing user credentials in Windows.
Despite these protective measures, researchers continue to discover ways to circumvent the new barriers. One such method involves exploiting vulnerable libraries, commonly known as “Bring Your Own Vulnerable DLL” (BYOVDLL), which allows the loading of a compromised DLL into the LSASS process, thereby reintroducing the vulnerability.
A specialist from Orange Cyberdefense found a way to bypass Microsoft’s security mechanisms and execute arbitrary code within the LSASS process. The attacker focused on the CNG Key Isolation service (KeyIso) as a point of entry.
The researcher sought to load a vulnerable version of the keyiso.dll library into LSASS. To achieve this, they modified the registry settings to point to the vulnerable version of the library. However, upon attempting to start the service, the specialist encountered an error related to an unsigned file, meaning the system could not locate the digital signature for the DLL, which prevented the library from loading.
In search of a solution, the researcher turned to the file catalogs containing cryptographic hashes used to verify the authenticity of files in Windows. By installing the appropriate catalog on a test machine, the researcher confirmed that the system recognized the signature of the vulnerable library. Consequently, the compromised version of keyiso.dll was successfully loaded into the protected LSASS process.
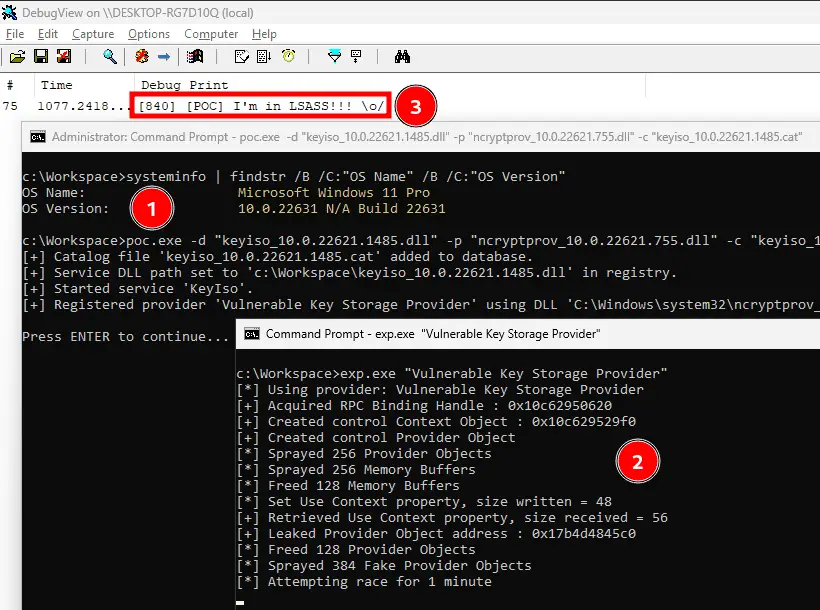
The researcher then proceeded to execute the full exploitation chain. To do so, they registered a new key provider that utilized the vulnerable version of the ncryptprov.dll library. After registration, the researcher verified that the compromised DLL was successfully loaded into the LSASS process using System Informer.
In the final stage of the study, the researcher launched an exploit that confirmed the successful execution of code within the protected LSASS process. They employed the OutputDebugStringW method to output a debug message, which appeared in the debugger, thereby confirming that the attack succeeded – arbitrary code was executed in the context of the protected process.