A new security vulnerability was found in the GRUB boot manager, CVE-2023-4001. This vulnerability, rated at a concerning 5.6 on the Common Vulnerability Scoring System (CVSS), presents a unique challenge in the realm of computer security, particularly targeting the GRUB boot manager on UEFI-based systems.
What is CVE-2023-4001?
CVE-2023-4001 is an authentication bypass flaw in GRUB (GRand Unified Bootloader). GRUB is the gatekeeper of the booting process in many UEFI-based computers, controlling what the computer does on startup. This vulnerability allows unprivileged users with physical access to bypass the robust password protection feature of GRUB, essentially leaving the door wide open for unauthorized access.

Understanding GRUB and UEFI
To appreciate the severity of this issue, we must first understand GRUB’s role in UEFI-based systems. UEFI (Unified Extensible Firmware Interface) has replaced the traditional BIOS in most modern computers, offering more features and a quicker boot time. GRUB is a critical component in this setup, responsible for launching the operating system.
The Flaw in Configuration
GRUB’s configuration, in theory, should be secure. The commands required to enable its password protection are stored in an external file, typically named “grub.cfg”. This file’s integrity is crucial, as it dictates the security of the boot process.
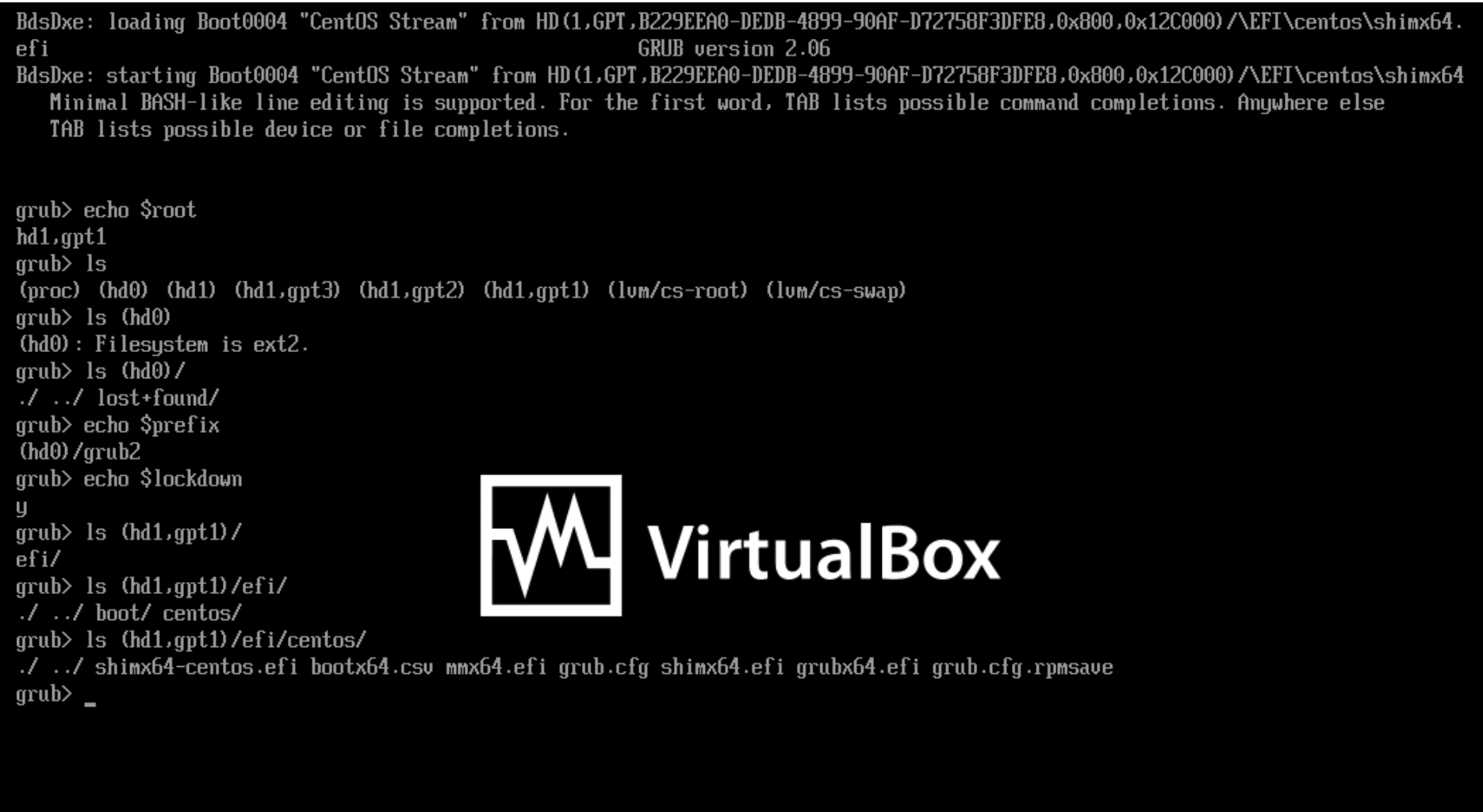
The Split Configuration Problem
On UEFI computers, the GRUB configuration is split between two files: one in the EFI System Partition and the main configuration file in the “/boot” volume. The password is stored in this main file. However, if the main configuration file is not found, GRUB defaults to spawning a shell – a backdoor waiting to be exploited.
Exploiting the Vulnerability
The exploit hinges on the GRUB’s method of locating the main configuration file using a file system UUID. If a system has two file systems with the same UUID, GRUB might pick the wrong one. By creating a fake “/boot” volume with the same UUID on a removable drive, an attacker can trick GRUB into booting from this drive, completely bypassing the password protection. Below is a video demonstrating the attack:
The Role of Physical Access
Physical access is key. An attacker with access to the computer can easily attach a USB drive with the duplicated UUID and reboot the system. This simplicity is what makes CVE-2023-4001 so dangerous.
The Response from Red Hat
Red Hat has proposed a fix that restricts the UUID scan to the block device used to launch the GRUB boot manager. This solution aims to ensure that the “/boot” volume resides on the same drive as the EFI System Partition, thereby preventing the vulnerability from being exploited.
Via: dfir