At DEF CON 32, a new tool named Shwmae was introduced, capable of bypassing the security of Windows Hello—a biometric authentication system developed by Microsoft. Shwmae is designed for use by individuals with privileged access to the system.
Shwmae was showcased in a presentation on how to remotely circumvent Windows Hello security, without the need for physical interaction with the user’s device. In the hands of a malicious actor, this tool enables the extraction and utilization of keys, certificates, and other protected data that would otherwise remain inaccessible.
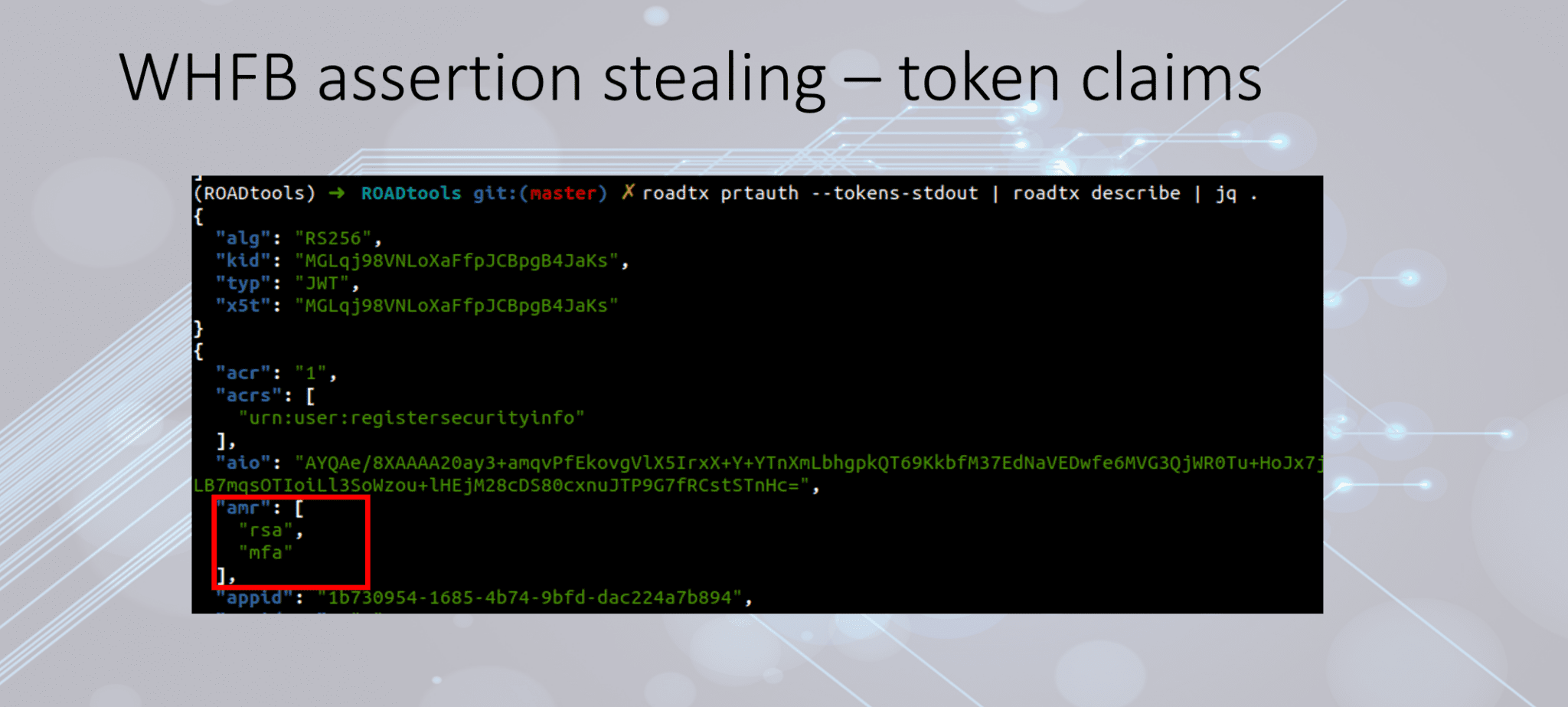
By default, the program operates in enumeration mode unless specified otherwise, providing specialized capabilities for attacking the system. This mode can also be explicitly enabled with the ‘enum’ command. In enumeration mode, the program displays a list of all available Windows Hello containers, followed by a detailed list of all registered keys and Windows Hello protection mechanisms within each container. If the computer lacks a TPM (Trusted Platform Module), the program will generate a PIN code hash, which can then be subjected to offline cracking using tools like hashcat.
Biometric protectors associated with facial recognition or fingerprints are decrypted automatically, rendering them particularly vulnerable to attacks. However, other protectors, such as PIN and Recovery, require additional efforts to decrypt, making Shwmae especially dangerous in the hands of a skilled adversary.
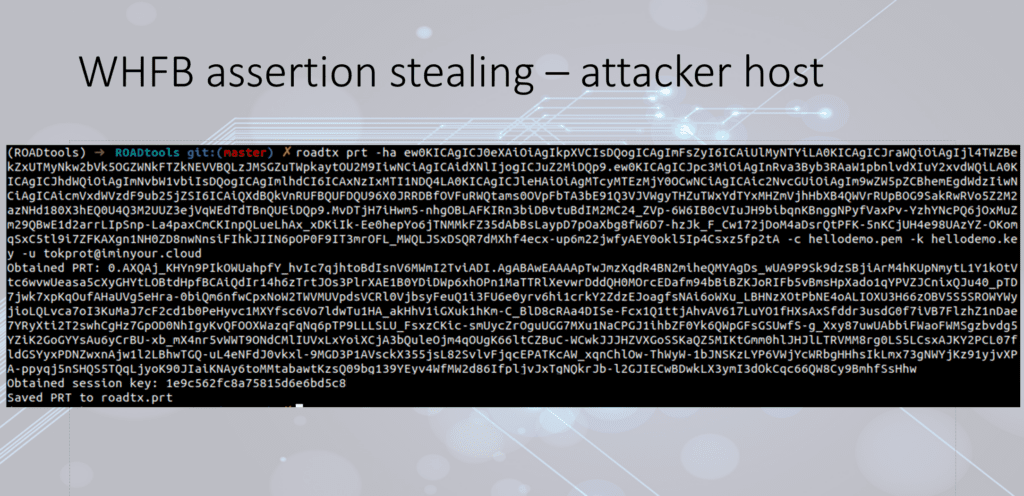
Another significant feature of Shwmae is its ability to work with PRT (Primary Refresh Token). The tool can generate and refresh PRTs using the keys registered in Windows Hello. If Cloud Trust authentication is enabled within the target organization, the tool can decrypt the Cloud TGT (Ticket Granting Ticket), allowing the attacker to authenticate on the corporate network with user privileges, thereby opening up vast opportunities for further attacks on internal resources.
In WebAuthn mode, Shwmae allows the creation of a web server to intercept and proxy WebAuthn requests from the attacker’s host. A malicious actor could install a web server on a compromised device to receive requests from an attacking browser and use the compromised credentials to log in via Passkey authentication. This function is particularly dangerous as it enables the attacker to use another person’s credentials without requiring physical access to the victim’s device.
The Dump mode allows the extraction of private keys protected by Windows Hello, but only in cases where they are stored in software rather than at the hardware level. The leakage of such keys could lead to a loss of control over accounts and data, posing a serious security threat.
Lastly, but by no means least, is the Sign mode, which allows an attacker to sign any data using the selected Windows Hello key. This scenario permits the creation of fraudulent digital signatures, making this mode potentially dangerous for misuse in various contexts.
Shwmae is an open-source tool and is available on Github.
Related Posts:
- Critical Vulnerability in Windows Hello for Business Discovered by Researcher
- Hackers Exploit Fingerprint Sensor Vulnerabilities to Bypass Windows Hello
- Windows 10 facial recognition feature exist vulnerablity that can use a photo to unlock the computer