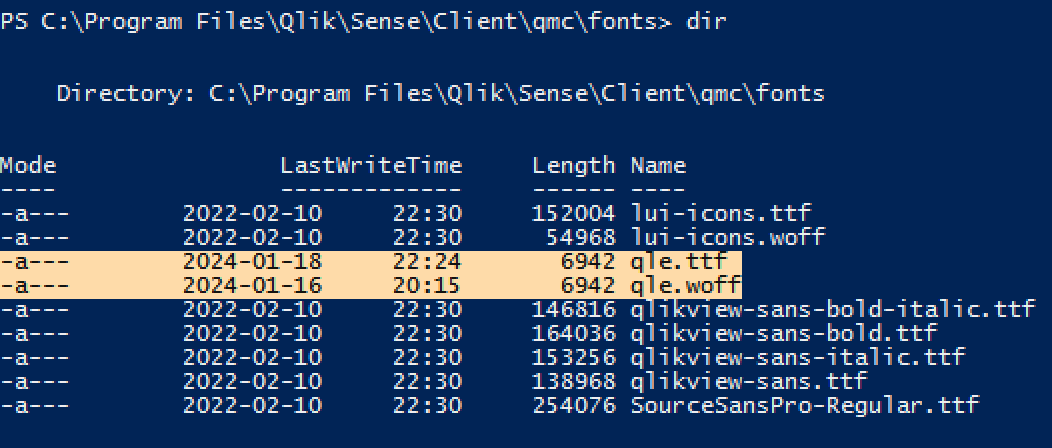
Directory listing with exploitation artefacts left by Cactus ransomware group
A public-private partnership in the Netherlands has revealed critical information about a dangerous ransomware group dubbed Cactus that has been actively targeting Qlik Sense servers, a popular business intelligence tool. Through the combined expertise of the Melissa partnership, which includes security experts from NCC Group’s Fox-IT, investigators discovered a pattern in the methods used by Cactus and a way to identify vulnerable or compromised systems around the world.
Qlik Sense: The Target of Choice for Cactus
The modus operandi of the Cactus group involves the exploitation of specific vulnerabilities within Qlik Sense, notably CVE-2023-41266 and CVE-2023-41265, known as ZeroQlik, and potentially CVE-2023-48365 or DoubleQlik. These vulnerabilities allow unauthorized initial access via misleading tactics that complicate detection and response, demonstrating the group’s psychological acumen in masking their intrusion methods.
Global Threat: Collaborative Response Effort
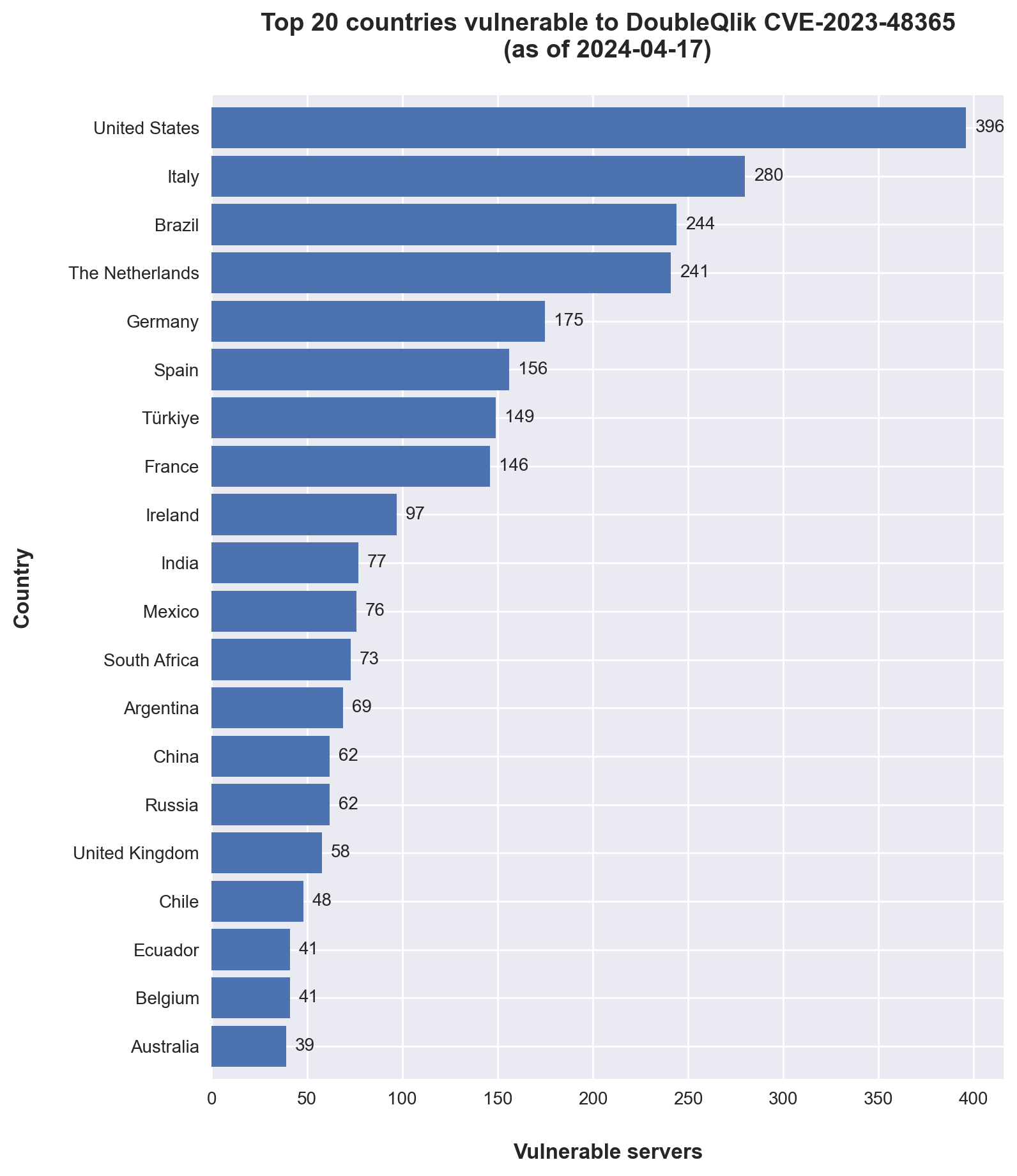
Based on an initial global scan conducted on April 17, 2024, experts identified a staggering 5,205 Qlik Sense servers worldwide, with over 3,000 of them still vulnerable to the exploits used by Cactus. The Dutch Institute for Vulnerability Disclosure (DIVD), the National Cyber Security Center (NCSC), and the Digital Trust Center (DTC) have joined forces to notify at-risk organizations, providing crucial information to help mitigate attacks.
The threat has a wide geographical spread, affecting hundreds of servers across the United States, Italy, Brazil, the Netherlands, and Germany. In the Netherlands alone, while most of the 241 vulnerable systems seemed secure, six were unfortunately compromised, illustrating the pervasive nature of this cybersecurity threat.
What Makes the Cactus Group Distinct

Distinguishing this ransomware group from others is their tendency to redirect the output of executed commands into a True Type font file, qle.ttf. This file, located within accessible directories, serves as a clear indicator of compromise. Scans have revealed approximately 122 servers worldwide that contain this tell-tale file, suggesting potential compromises.
Call to Action
Organizations using Qlik Sense are urged to take immediate action. Here’s what you need to do:
- Check Qlik Version: Identify your current Qlik Sense version immediately.
- Patch or Upgrade: Apply the latest available security patches [1, 2] if your version is supported. If your Qlik installation is no longer supported, consider upgrading or replacing it as soon as possible.
- Limit Access: Restrict direct exposure of your Qlik Sense server to the internet. Implement IP whitelisting or, preferably, use secure remote access solutions.
- Seek Expert Help: If you believe your system may have been vulnerable, it’s crucial to engage cybersecurity specialists to conduct a thorough investigation and determine if a breach has occurred.