
Calibre, the popular cross-platform e-book management software, has three significant security vulnerabilities. These vulnerabilities, identified by researchers from STAR Labs SG Pte. Ltd., could potentially expose millions of users to various cyber threats.
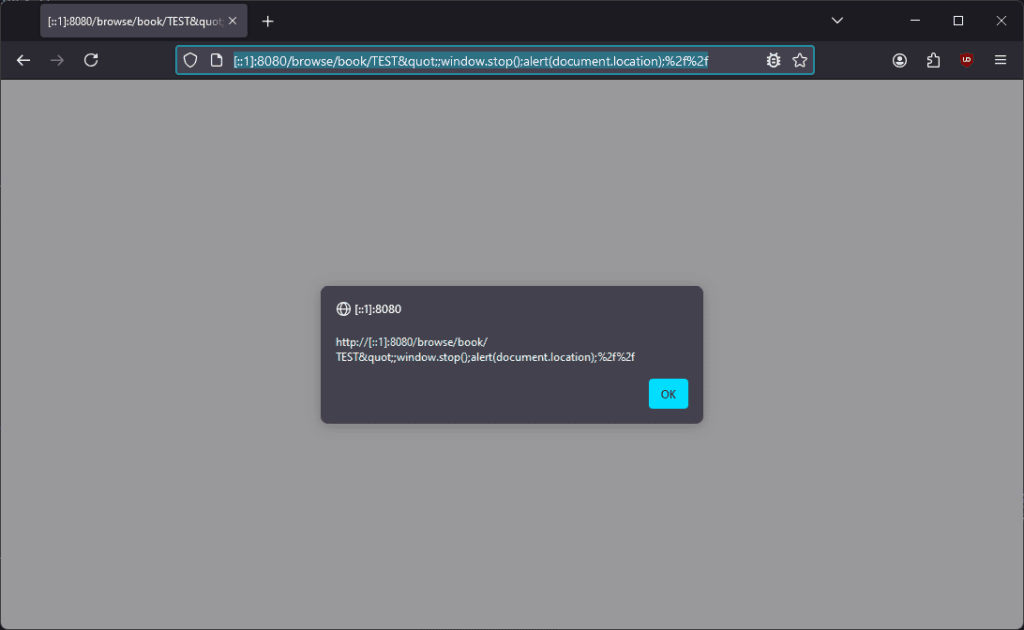
The first vulnerability, tracked as CVE-2024-7008 (CVSS 5.3), enables attackers to inject malicious JavaScript code into the Calibre content server. This could allow threat actors to manipulate unsuspecting users into performing actions on their behalf, including unauthorized modifications to the server or exfiltration of sensitive information. To mitigate this flaw, ensure that user input is properly validated before being used to generate HTML content. Specifically, book IDs should be strictly numeric, so it is crucial to validate that the input consists solely of digits before incorporating it into the HTML structure.

The second flaw, CVE-2024-6781 (CVSS 7.5), permits unauthenticated attackers, or those with certain privileges, to read arbitrary files stored on the vulnerable server. This could lead to the exposure of private documents, user data, or other confidential information. Sanitize all user-supplied input thoroughly to prevent path traversal attacks.

The most critical vulnerability, CVE-2024-6782 (CVSS 9.8), gives attackers the ability to remotely execute arbitrary code on affected systems. This grants them significant control over compromised devices, potentially allowing them to install additional malware, steal data, or even launch attacks on other connected systems. To mitigate this flaw, strictly enforce access controls on publicly accessible endpoints. If code execution is an intended feature, the server should not be exposed to the public internet, or access should be tightly restricted to highly privileged users only.
These vulnerabilities primarily impact the Calibre content server feature, a popular tool for sharing eBook libraries online. While the exact number of affected users remains unclear, the widespread adoption of Calibre, particularly among avid readers, academic researchers, and literary enthusiasts, amplifies the potential impact of these flaws.
Users are strongly advised to upgrade their software to the latest version immediately to mitigate the risks associated with these security issues. Additionally, enabling basic authentication on the content server can provide an extra layer of protection against unauthorized access.
Related Posts:
- WordPress Releases Urgent Security Patch – Update Immediately!
- Microsoft says our most popular server product runs on Linux