CallObfuscator
Obfuscate (hide) the PE imports from static/dynamic analysis tools.
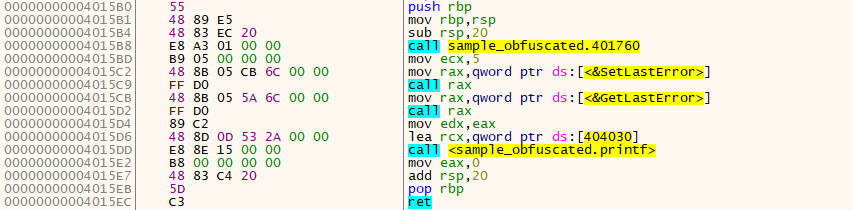
Theory
This’s pretty forward, let’s say I’ve used VirtualProtect and I want to obfuscate it with Sleep, the tool will manipulate the IAT so that the thing that points to VirtualProtect will point instead to Sleep, now at executing the file, the windows loader will load Sleep instead of VirtualProtect, and moves the execution to the entry point, from there the execution will be redirected to the shellcode, the tool put before, to find the address of VirtualProtect and use it to replace the address of Sleep which assigned before by the loader.
Impact
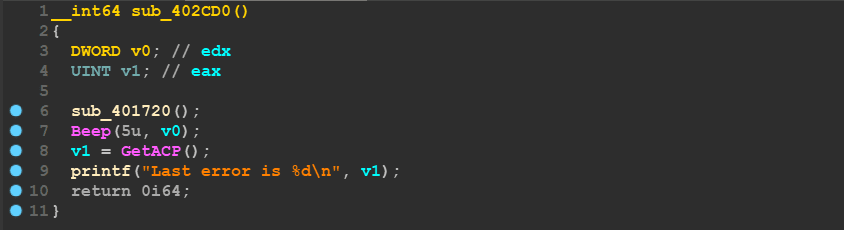
IDA HexRays Decompiler
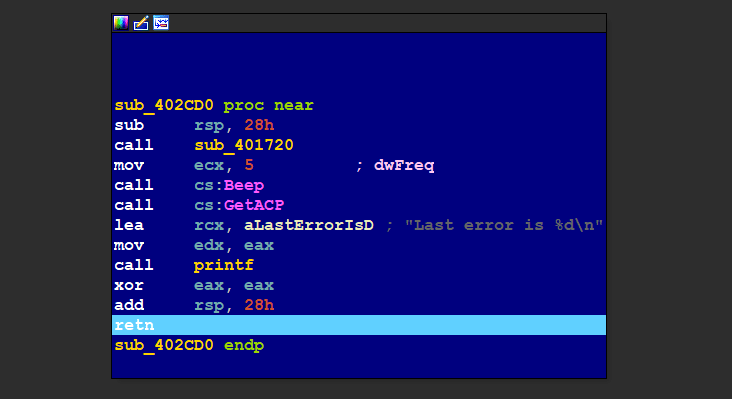
IDA Debugger
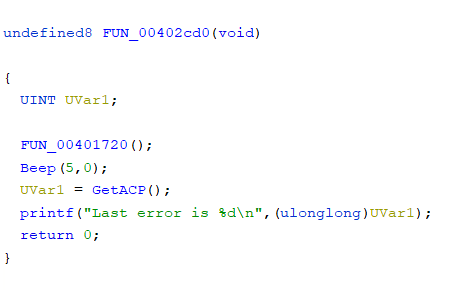
Ghidra
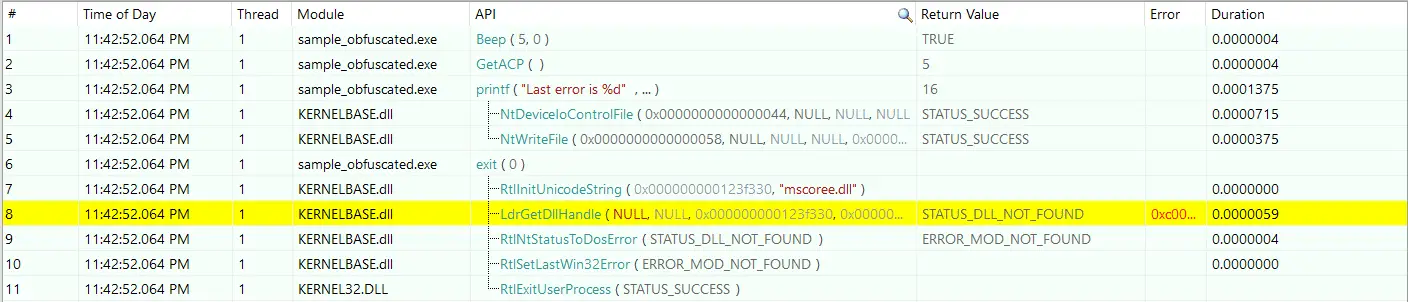
ApiMonitor
That’s because all of the static analysis tool depend on what is the api name written at IAT which can be manipulated as shown.
For ApiMonitor, because of using IAT hooking, the same problem exists.
On the other side, for tools like x64dbg the shown api names will only depend on what is actually called (not what written at the IAT).
Additional
- Dumping the obfuscated PE out from memory won’t deobfuscate it, because the manipulated IAT will be the same.
- The main purpose for this tool is to mess up with the analysis process (make it slower).
- One can obfuscate any imported symbol (by name or by ordinal) with another symbol (name or ordinal).
- The shellcode is executed as the first tls callback to process the obfuscated symbols needed by the other tls callbacks before the entry point is executed.
- The shellcode is shipped as c code, generated when the tool is compiled to facilitate editing it.
- The obfuscated symbols names are being resolved by hash not by name directly.
- The tool disables the relocations and strips any of the debug symbols.
- The tool creates a new rwx section named
.cobffor holding the shellcode and the other needed data. - It can be used multiple times on the same obfuscated PE.
- Tested only on Windows 10 x64.
- Get the source with git clone https://github.com/d35ha/CallObfuscator.
- Download binaries from the Release Section.