Canadian Furious Beaver v0.1 releases: tool for hijacking IRPs handler in Windows drivers
Canadian Furious Beaver
Idea
Furious Beaver is a distributed tool for capturing IRPs sent to any Windows driver. It operates in 2 parts:
- the “Broker” combines both a user-land agent and a self-extractable driver (
IrpDumper.sys) that will install itself on the targeted system. Once running it will expose (depending on the compilation options) a remote named pipe (reachable from\\target.ip.address\pipe\cfb), or a TCP port listening on TCP/1337. The communication protocol was made to be simple by design (i.e. not secure) allowing any 3rd party tool to dump the driver IRPs from the same Broker easily (via simple JSON messages). - the GUI is a Windows 10 UWP app made in a
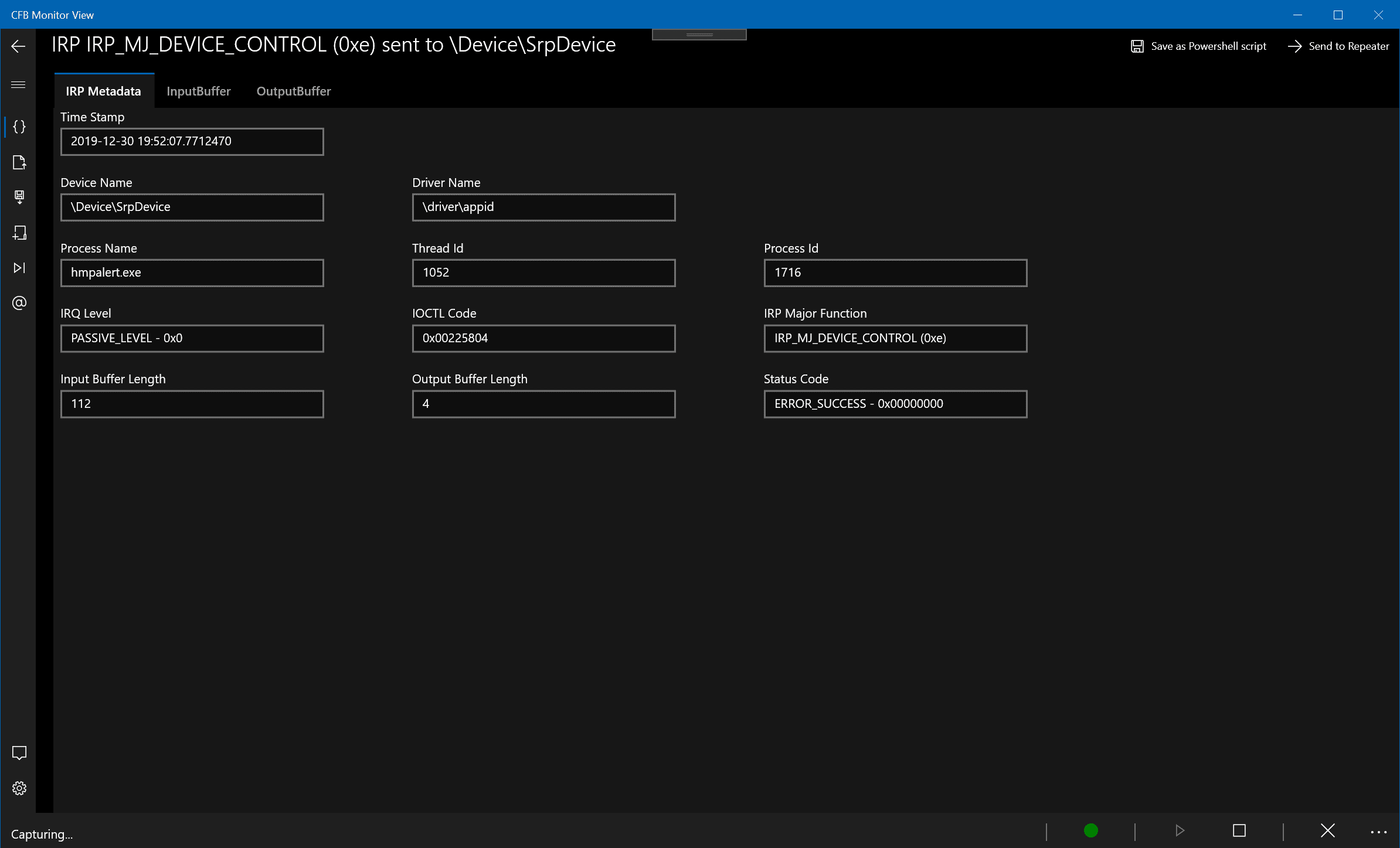
ProcMon-style: it will connect to wherever the broker is, and provide a convenient GUI for manipulating the broker (driver enumeration, hooking and IRP capturing). It also offers facilities for forging/replaying IRPs, auto-fuzzing (i.e. apply specific fuzzing policies on each IRP captured), or extract IRP in various formats (raw, as a Python script, as a PowerShell script) for further analysis. The captured data can be saved on disk in an easily parsable format (*.cfb= SQLite) for further analysis, and/or reload afterward in the GUI.
Although the GUI obviously requires a Windows 10 environment (UWP App), the Broker itself can be deployed on any Windows 7+ host (x86 or x64). The target host must have testsigning BCD policy enabled, as the self-extracting driver is not WHQL friendly.
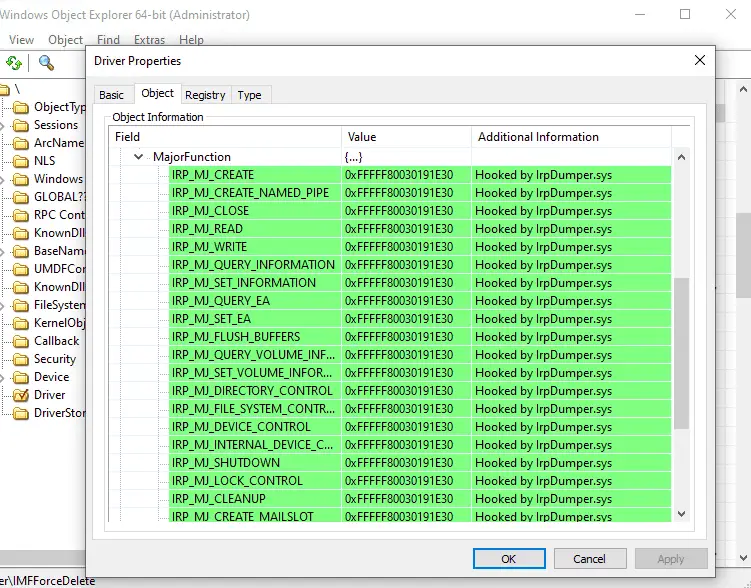
IrpDumper.sys is the driver part of the CFB Broker that will auto-extract and install when launched. The driver will be responsible for hooking the IRP Major Function table of the driver that is requested to be hooked, via an IOCTL passed from the Broker. Upon success, the IRP table of the driver will then be pointing to IrpDumper.sys interception routine, as we can easily see with a debugger or tools like WinObjEx64.
IrpDumper.sys in itself then acts a rootkit, proxy-ing all calls to the targeted driver(s). When a DeviceIoControl is sent to a hooked driver, IrpDumper will simply capture the data if any, and push a message to the user-land agent (Broker), and yield the execution back to the legitimate drivers, allowing the intended code to continue as expected. The Broker stores all this data in user-land waiting for an event to ask for them.