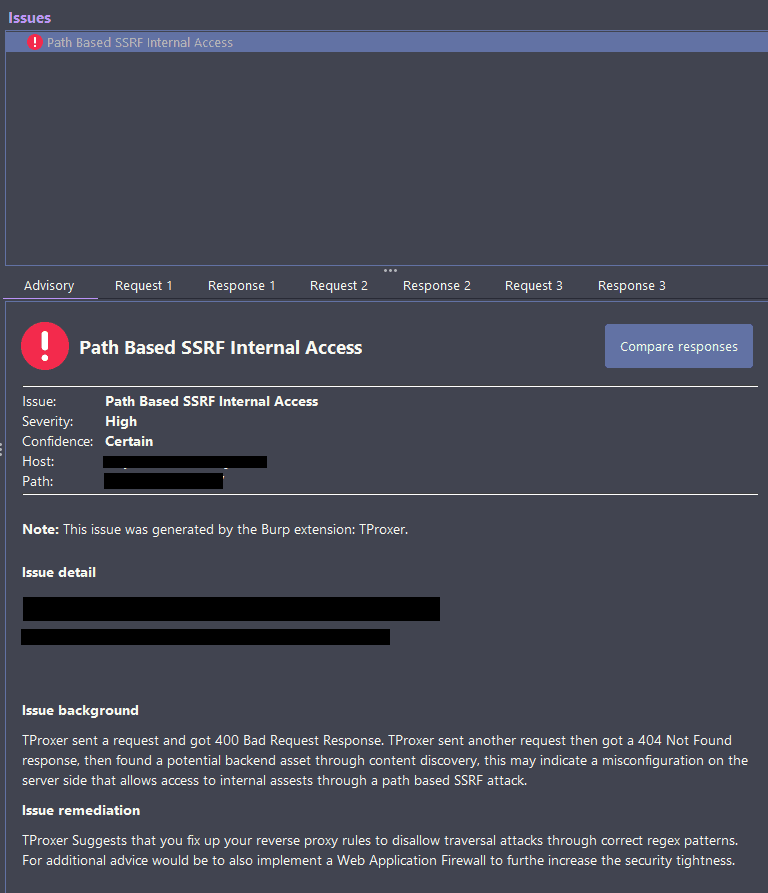
TProxer A Burp Suite extension was made to automate the process of finding reverse proxy path-based SSRF....
WebApp PenTest
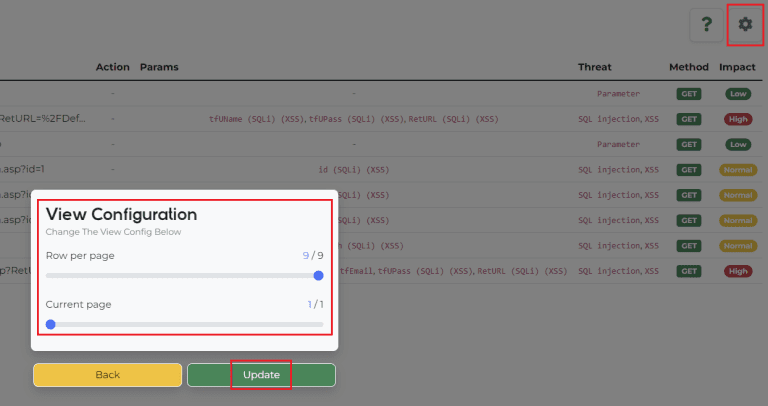
BWASP The BoB Web Application Security Project (BWASP) is an open-source, analysis tool to support for Web...
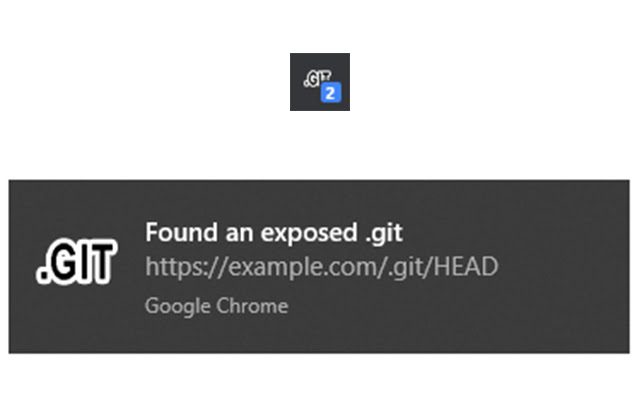
DotGit An extension for checking if .git is exposed in visited websites Features Check if a .git/.svn/.hg...
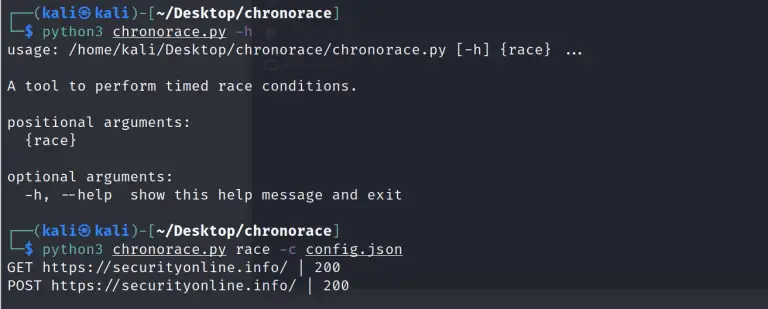
ChronoRace ChronoRace is a tool to accurately perform timed race conditions to circumvent application business logic. I’ve...
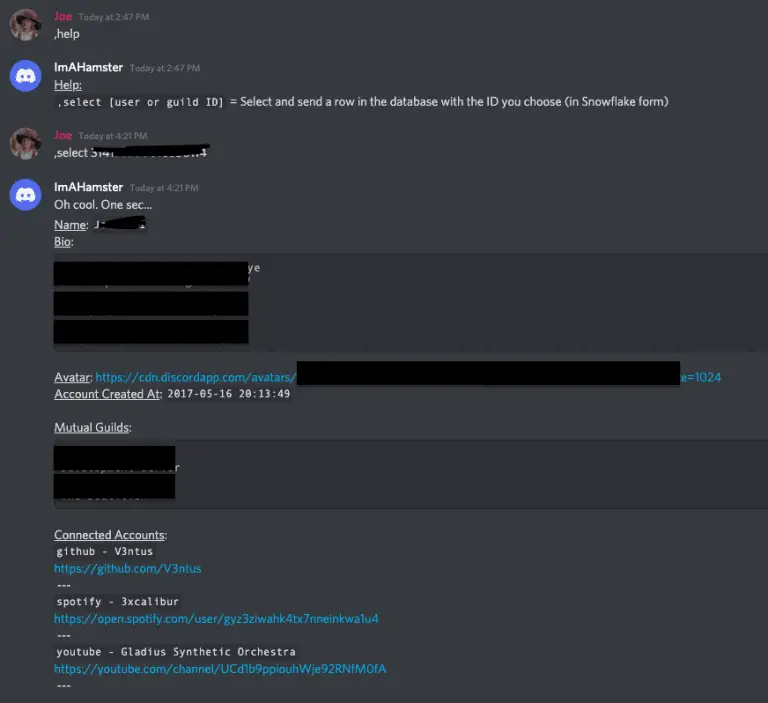
darvester PoC Discord user and guild information harvester Data logged for each user: Users’ profile created date,...
Jira-Lens Jira-Lens 🔍 is a Python Based Vulnerability Scanner for JIRA. Jira is a proprietary issue tracking...
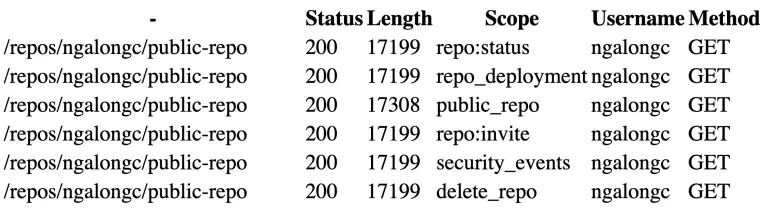
OpenAPI Security Scanner Authorization security issues in modern web applications could not be easily picked up by...
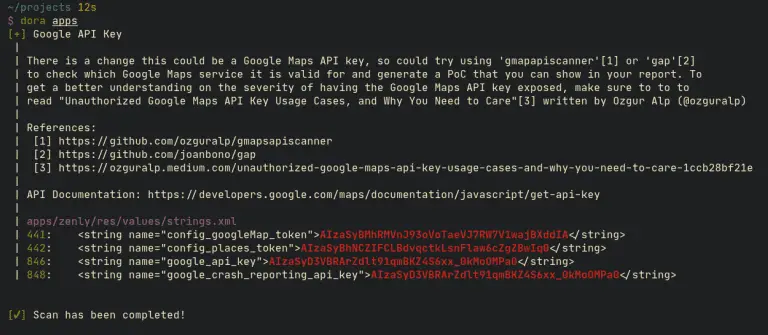
dora Find exposed API keys based on RegEx and get exploitation methods for some of the keys...
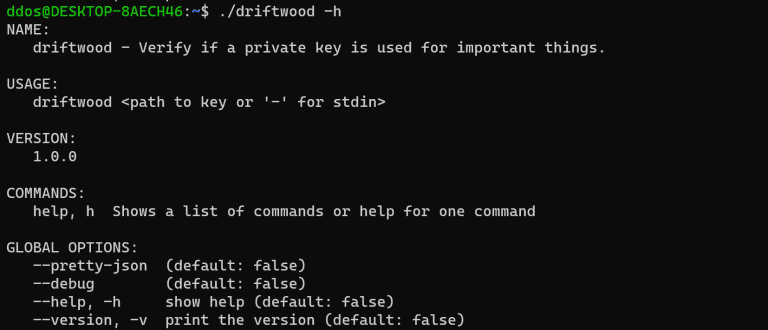
Driftwood Driftwood is a tool that can enable you to look up whether a private key is...
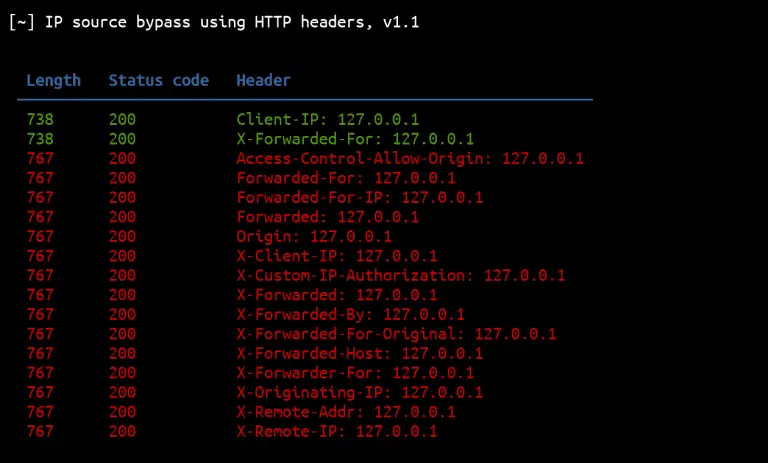
ipsourcebypass This Python script can be used to bypass IP source restrictions using HTTP headers. Features 17...
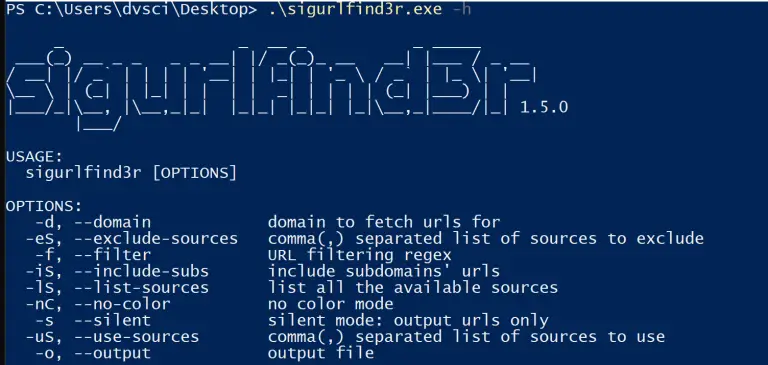
sigurlfind3r A passive reconnaissance tool for known URLs discovery – it gathers a list of URLs passively...
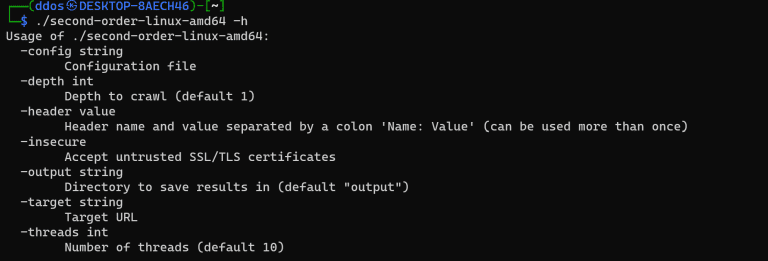
Second Order Scans web applications for second-order subdomain takeover by crawling the app, and collecting URLs (and...
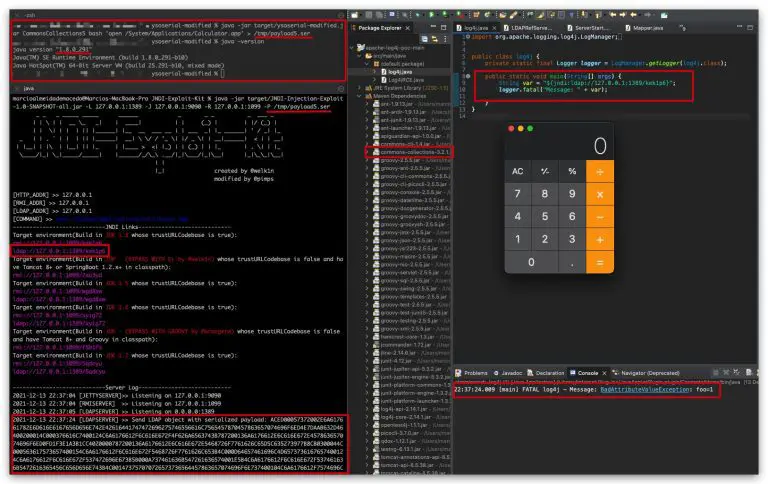
JNDI Exploit Kit This is a forked modified version of the great exploitation tool created by @welk1n....
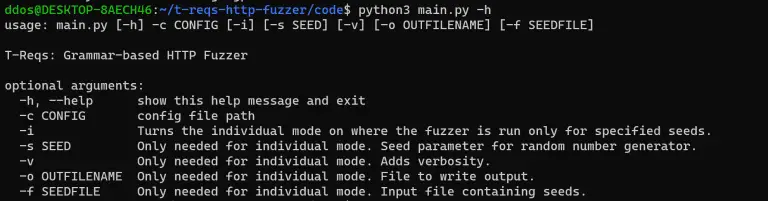
T-Reqs HTTP Fuzzer T-Reqs (Two Requests) is a grammar-based HTTP Fuzzer written as a part of the paper titled “T-Reqs:...
Damn Vulnerable NodeJS Application ADDED BUGS Prototype Pollution No SQL Injection Cross-site Scripting Broken Access Control Broken...