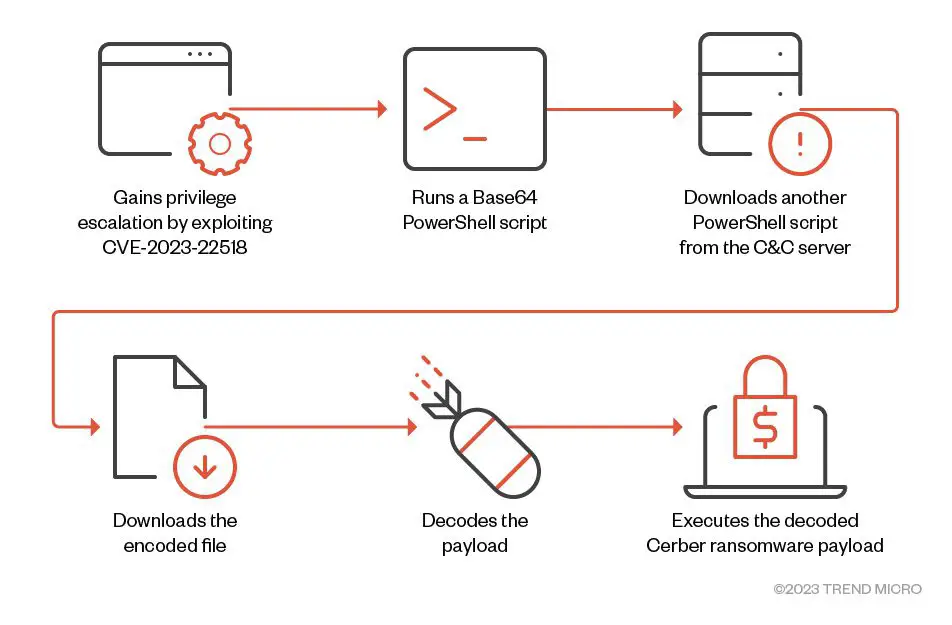
Overview of the delivery method used by Cerber
Cerber ransomware, once a major player in the ransomware landscape, has returned after a period of inactivity, and it’s now exploiting a new vulnerability in Atlassian Confluence to deploy its payload.
In October 2023, Atlassian published an advisory on CVE-2023-22518, an Improper authorization vulnerability affecting the Confluence Data Center and Server. The vulnerability allows unauthorized users to reset and create a Confluence instance administrator account, allowing them to perform all admin privileges available to these accounts.
On November 2, 2023, a proof-of-concept (PoC) for CVE-2023-22518 was leaked to the public. Shortly thereafter, Trend Micro researchers observed Cerber ransomware exploiting the vulnerability to deploy its payload.

The Cerber attack chain begins with the threat actor gaining access to a vulnerable Confluence server via CVE-2023-22518. Once they have access, they execute an encoded PowerShell command to download and execute a remote payload.
The PowerShell script then connects to a command-and-control (C&C) server and downloads a malicious text file. The text file contains decimal-encoded values, which reveal the Cerber ransomware payload after it is decrypted.
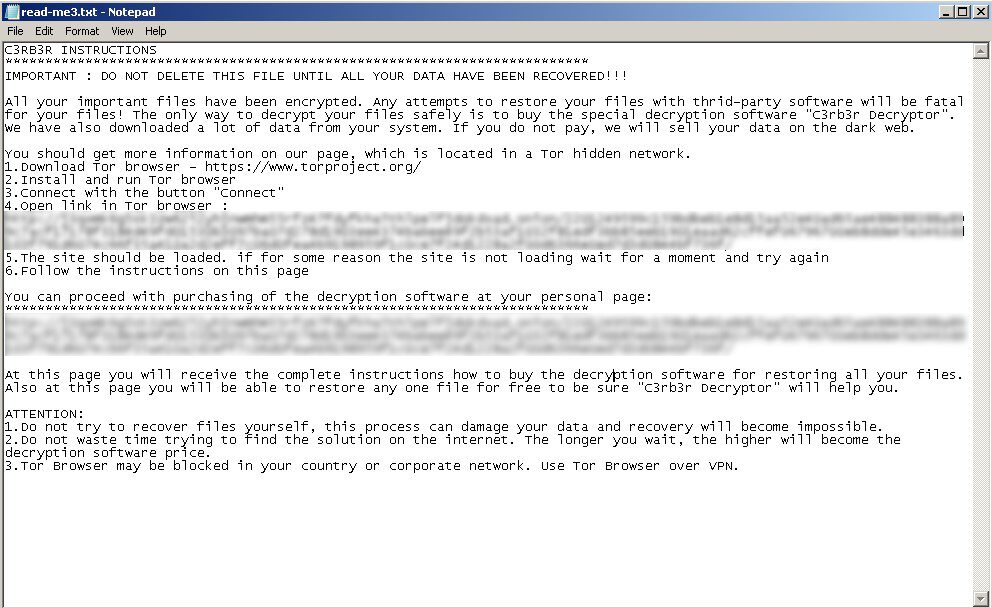
The PowerShell script then executes the decoded Cerber payload, which encrypts the files in the system and appends the extension “.L0CK3D”. The ransomware also drops a ransom note with the filename “read-me3.txt” in all directories.
Trend Micro researchers also observed multiple Linux bash files being downloaded from the same IP address that deploys the Cerber ransomware. This suggests that Cerber is now developing variants for Linux systems as well.
Comparing the characteristics of older Cerber ransomware samples to the new one, Trend Micro researchers were able to confirm that the ransomware exploiting CVE-2023-22518 is indeed Cerber. The payment site is very similar to the old payment site, with the same text used for the payment site interface.
However, there are some differences between previous Cerber variants and the one seen in this incident. The ransom note for the older Cerber samples were in HTML format, with the appended string being “.locked”. In the new sample, the ransom note is in text format and appends the string “.L0CK3D” to the encrypted files.
The return of Cerber ransomware is a reminder that even old malware families can still be a threat. Organizations should patch their systems as soon as possible to mitigate the risk of exploitation. Additionally, they should implement security controls such as multi-factor authentication and network segmentation to help protect their systems from ransomware attacks.