Chalubo Malware Wreaks Havoc: Half a Million Routers Permanently Disabled
A destructive cyberattack, dubbed “The Pumpkin Eclipse” by Lumen Technologies’ Black Lotus Labs, has knocked out over 600,000 small office/home office (SOHO) routers, leaving a significant portion of an internet service provider’s (ISP) customers without internet access. The incident, which occurred over a 72-hour period in late October 2023, rendered the affected devices permanently inoperable, requiring a full hardware replacement.
This attack stands out due to its unprecedented scale and impact. It’s the first known cyberattack to necessitate the replacement of over 600,000 devices and the second recorded instance where a cyberattack caused physical damage to such a large number of devices. The affected ISP serves many rural and underserved communities, where the loss of internet access can have severe consequences for emergency services, agricultural operations, and healthcare providers.

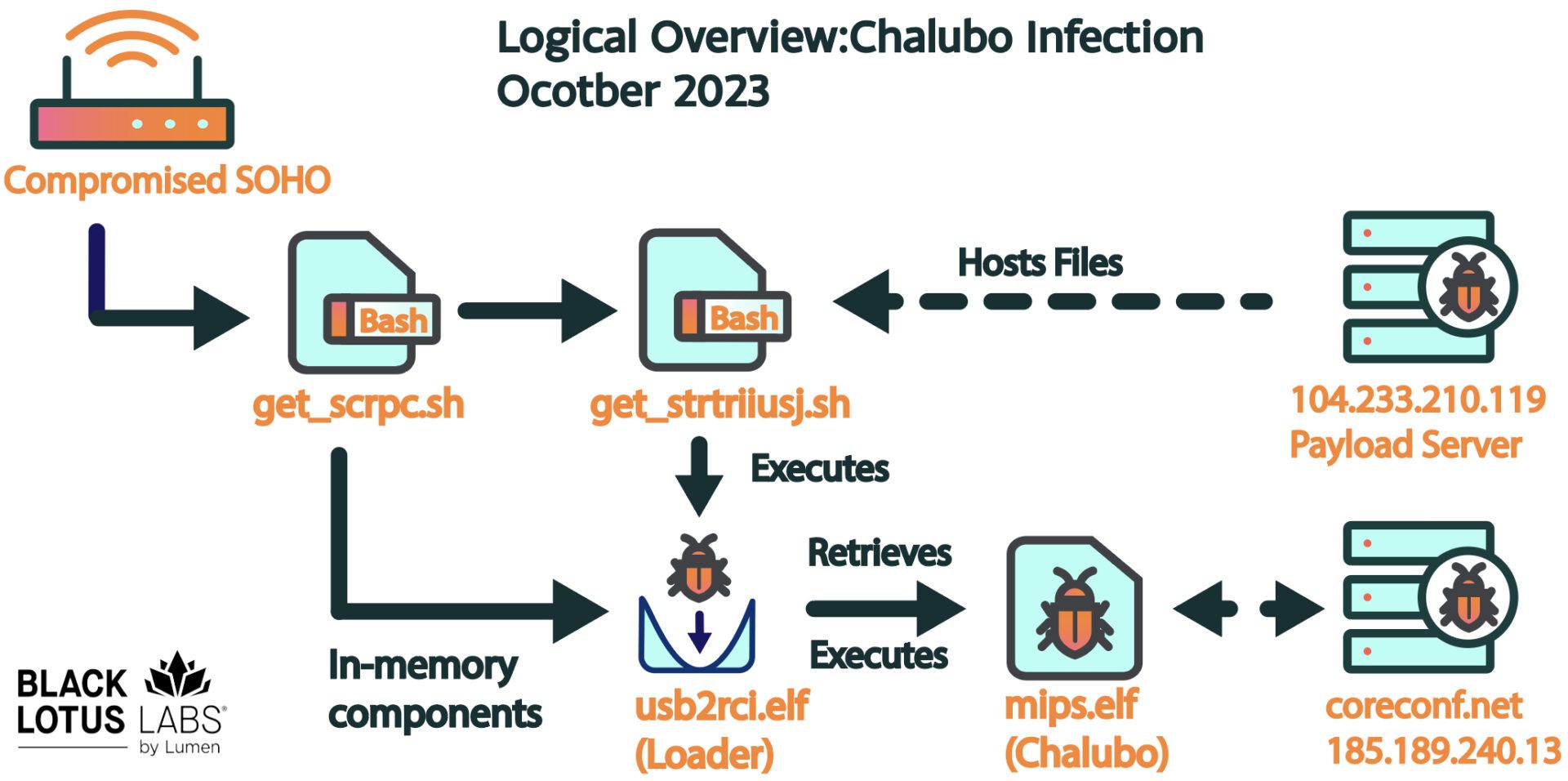
Logical Infection process with corresponding C2 nodes | Image: Black Lotus Labs
Black Lotus Labs identified the Chalubo remote access trojan (RAT) as the primary payload responsible for the attack. This commodity malware, known for its ability to execute arbitrary code and perform DDoS attacks, was likely used to deliver a destructive payload that bricked the routers. While the exact exploit used for initial access remains unclear, researchers suspect weak credentials or an exposed administrative interface may have been exploited.
The infection process began with either the exploitation of vulnerabilities or the use of compromised remote desktop protocol (RDP) credentials. The attack chain included multiple stages:
- Initial Access: Devices reached out to a payload server to retrieve a bash script named “get_scrpc,” which then checked for the presence of a malicious binary and opened iptables for connections.
- Payload Deployment: If the binary was not found, the script retrieved the malicious payload, executing and renaming it to evade detection. The Chalubo malware used ChaCha20 encryption to secure its communications and control subsequent stages.
- Persistence and Execution: The malware adjusted system settings to prevent termination and deleted itself from disk post-execution, complicating detection and analysis.
Lumen’s investigation revealed that the attack had significant ramifications, particularly for rural and underserved communities within the ISP’s service area. These areas potentially lost access to emergency services, critical farming data, and telehealth capabilities. The attack’s confinement to a single ASN, affecting specific models like the ActionTec T3200s and T3260s, and Sagemcom F5380, suggests a targeted malicious firmware update rather than a broad-based exploit.
Lumen’s global telemetry data revealed that the Chalubo malware was highly active in late 2023 and early 2024, with over 330,000 unique IP addresses communicating with known command and control servers. This suggests that while Chalubo was employed in this destructive attack, it is not exclusively designed for such purposes and has a broader global footprint.
Black Lotus Labs has integrated the indicators of compromise (IoCs) from this campaign into their threat intelligence feeds, enhancing the Lumen Connected Security portfolio. Ongoing monitoring of new infrastructure and activity related to Chalubo will provide crucial updates and defenses against future threats.





