Image: ThreatFabric
In July 2024, analysts at ThreatFabric Mobile Threat Intelligence observed new campaigns from Chameleon, a notorious Banking Trojan first discovered in December 2022. These recent campaigns have unveiled an unusual and sophisticated technique: masquerading as a Customer Relationship Management (CRM) app. This novel approach, particularly targeting employees in the hospitality sector, poses significant risks to businesses.
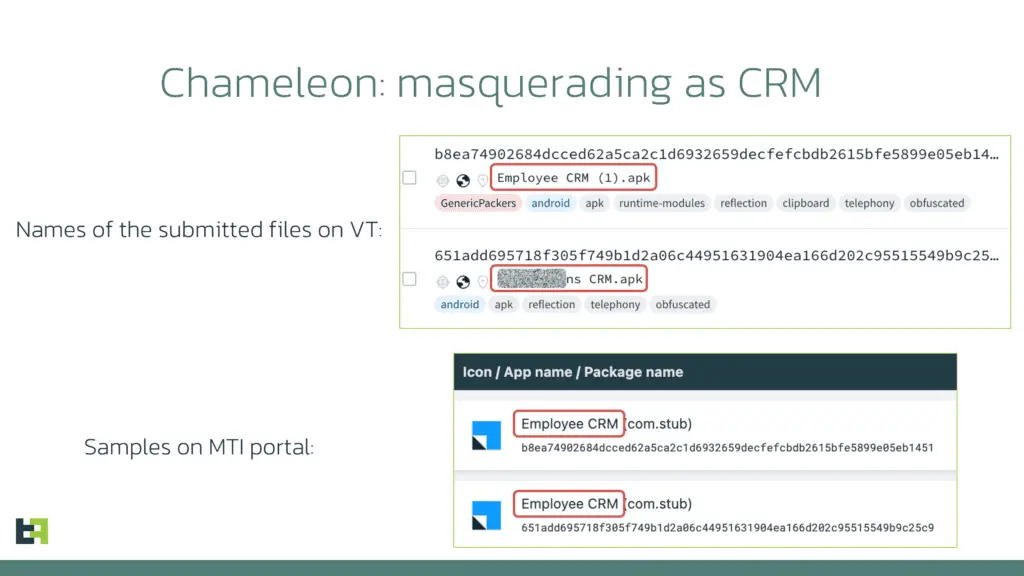
The latest campaign discovered by ThreatFabric reveals that Chameleon is now posing as a CRM app, specifically targeting a Canadian restaurant chain operating internationally. This campaign extends to regions in Europe and Canada, with indications of potential further expansion.
In the campaign, Chameleon uses a highly targeted approach. The file names uploaded to VirusTotal indicate a focus on hospitality workers, with one file named after a prominent Canadian restaurant chain. This suggests that the attackers aim to exploit employees who have access to corporate banking and CRM systems, posing a significant risk to organizational security.
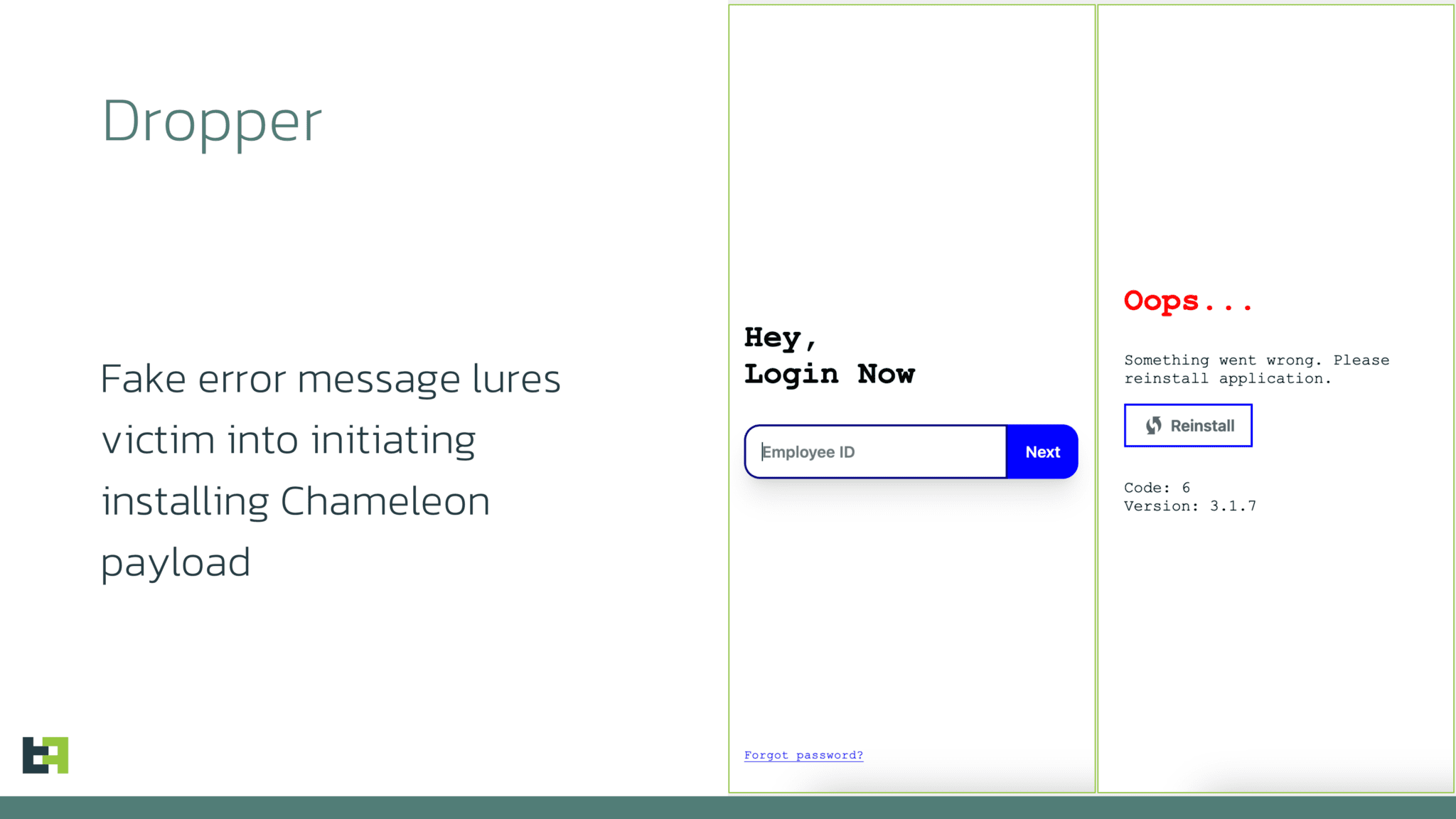
Infection Process:
- Dropper Installation: The initial stage involves a dropper capable of bypassing Android 13+ restrictions. This capability, previously predicted by ThreatFabric, has become essential for modern banking Trojans.
- Fake CRM Login Page: Once installed, the dropper displays a fake CRM login page, requesting the employee’s ID.
- Payload Installation: A message prompts the user to reinstall the application, which installs the Chameleon payload, bypassing Android’s AccessibilityService restrictions.
- Credential Harvesting: After installation, a fake website asks for employee credentials. Even though an error message is displayed post-submission, Chameleon runs in the background, collecting credentials and sensitive information via keylogging.
Cybercriminals are continuously innovating, now targeting employees of B2C businesses to gain access to business banking accounts. The convenience and proliferation of mobile banking products, especially for small and medium-sized businesses, provide fertile ground for such attacks. Financial organizations should educate their business customers about the potential impact of mobile banking malware like Chameleon and the severe consequences of such threats.
Related Posts:
- Sophos X-Ops Alerts: ‘Inhospitality’ Malspam Targets Hotels with Deceptive Tactics
- Biometric Bypass: Chameleon Banking Trojan Evolves, Android 13 Vulnerable