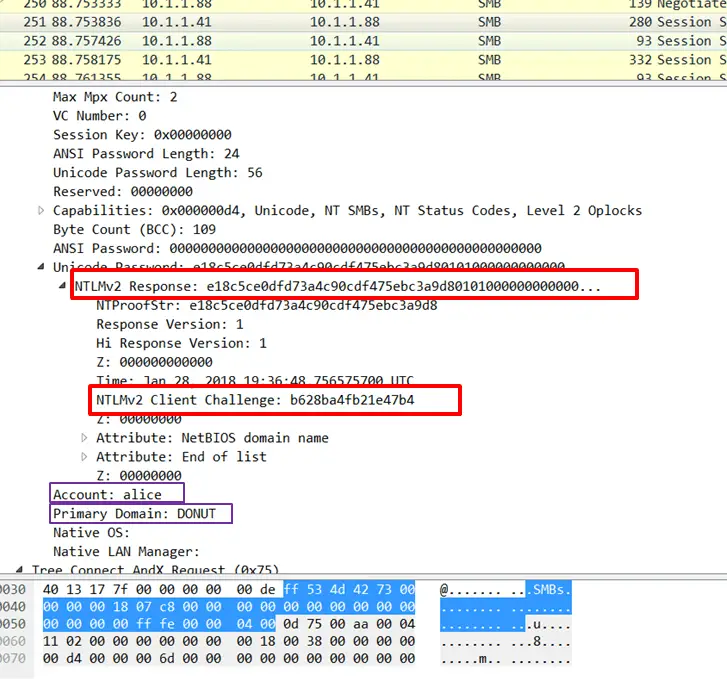
CheckPoint researchers recently reported that PDF files can be exploited by malicious attackers to steal Windows credentials (NTLM hashes) simply by opening files without user interaction. The specification feature of PDF can remotely load content for GoToE and GoToR. If a user opens an attacker’s specially crafted PDF document, it automatically sends a request to the remote malicious SMB server.
Because all SMB requests include an NTLM hash for authentication, the remote SMB server logs the relevant hash values and uses a tool to crack and obtain the password. Experts said that almost all PDF readers may be subject to such attacks. FoxIT has not yet responded to this, and Adobe stated that it does not plan to repair the adjustment. Microsoft issued ADV170014 repair recommendations to guide users to turn off NTLM SSO authentication in Windows operating systems.

Proof of Concept
The /AA entry is an optional entry defining actions to be performed when a page is opened (/O entry) or closed (/C entry). The /O (/C) entry holds an action dictionary. The action dictionary consists of 3 required entries: /S, /F, and /D:
- /S entry: Describes the type of action to be performed. The GoTo action changes the view to a specified destination within the document. The action types GoToR, (Go To Remote) and GoToE (Go To Embedded), both vulnerable, jump to destinations in another PDF file.
- /F entry: Exists in GoToR and GoToE, and has slightly different meanings for each. In both cases it describes the location of the other PDF. Its type is file specification.
- /D entry: Describes the location to go to within the document.
By injecting a malicious entry (using the fields described above together with his SMB server details via the “/F” key), an attacker can entice arbitrary targets to open the crafted PDF file which then automatically leaks their NTLM hash, challenge, user, host name and domain details.
Source, Image: checkpoint