
Sygnia detailed a cyberattack targeting a major telecommunication company in Asia. The attack was orchestrated by a sophisticated China-nexus threat actor tracked by Sygnia as Weaver Ant. The group’s primary objective was to gain and maintain continuous access to telecommunication providers for cyber espionage and sensitive information collection.
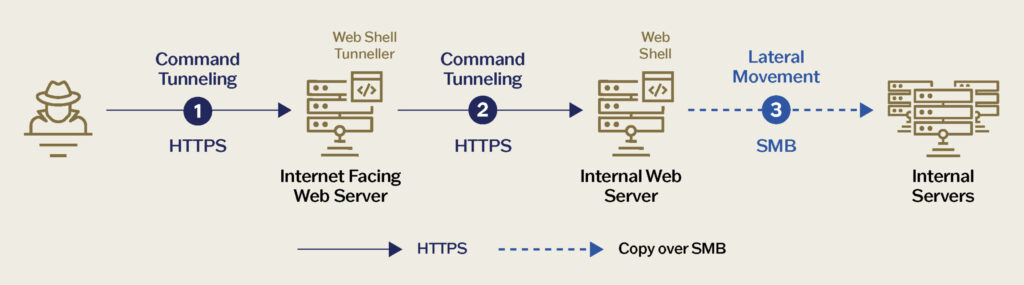
The report highlights the threat actor’s heavy reliance on web shells and web shell tunneling as their primary tools for maintaining persistence and enabling lateral movement.
Sygnia’s investigation uncovered numerous web shells, with two main types identified:
- Encrypted China Chopper: A lightweight malicious tool enabling remote access and control over compromised web servers.
- INMemory Web Shell: A web shell with no publicly available references, capable of in-memory execution of malicious modules.
The China Chopper web shell, originally developed by Chinese threat actors, is known for its small size and stealthy nature, making it ideal for persistent access, exploitation, and evading traditional security measures. In this campaign, the threat actor utilized a China Chopper web shell with AES encryption of the payload to bypass automated payload detection mechanisms.
The encrypted web shell employed two key evasion techniques:
- Keyword-based evasion: Using specific keywords as parameter names to evade WAFs.
- Payload truncation: Transmitting payloads exceeding WAF character limits to prevent complete forensic reconstruction.
The INMemory web shell further evades detection by enabling in-memory execution of malicious modules. This is achieved by decoding a hardcoded GZipped Base64 string into a Portable Executable (PE) and executing it in memory. The web shell also obfuscates code using Base64-encoded strings.
The INMemory web shell uses a portable executable (PE) named ‘eval.dll’ to execute C# code and payloads delivered via HTTP requests. This involves SHA256 hash matching, payload encoding, and execution using ‘JScriptEvaluate’ to run obfuscated, dynamically loaded code.
To investigate the persistent threat actor, Sygnia implemented stealth monitoring to avoid detection. This involved port mirroring techniques and automating the decryption and de-encapsulation of tunneled web shell traffic.
The threat actor utilized a recursive HTTP tunnel tool as a ‘second stage’ web shell for HTTP tunneling to access internal resources. This tool decoded parameters and dynamically constructed cURL commands to forward requests and maintain operational flexibility.
Weaver Ant employed web shell tunneling, using multiple web shells as ‘proxy servers’ to redirect inbound HTTP traffic for payload execution. This technique facilitated lateral movement within the compromised environment without deploying additional tools and camouflaged communication over legitimate HTTP/S traffic.
The traffic flowing through the web shell tunneling was encrypted, necessitating port mirroring to capture and decrypt the traffic. Sygnia’s team automated the decryption process to ‘peel’ each layer of encryption and obfuscation, revealing the actual commands and binaries for execution. The threat actor’s method was described as a ‘Matryoshka’ doll, with each layer concealing a more critical payload.
Weaver Ant employed various payloads, each with a distinct purpose, demonstrating the threat actor’s sophistication and stealth.
- ETW Patch & AMSI Bypass: The threat actor used defense evasion techniques, patching Event Tracing for Windows (ETW) to tamper with event logs and bypassing Antimalware Scan Interface (AMSI) protections.
- PowerShell without PowerShell: Weaver Ant executed PowerShell commands without initiating the PowerShell.exe process by leveraging the ‘System.Management.Automation.dll’ module. This allowed them to perform reconnaissance and lateral movement while evading detection.
- Lateral Movement over SMB: The threat actor used ‘Invoke-SMBClient’ to conduct reconnaissance and facilitate lateral movement, deploying web shells and harvesting credentials.
- Reconnaissance Activities: Weaver Ant performed reconnaissance using ‘Invoke-SharpView’ commands to enumerate the compromised Active Directory environment, identify high-privilege accounts and critical servers.
Weaver Ant exhibits characteristics typical of a China-nexus targeted threat group. These include:
- Target selection focused on specific industries and geographic locations aligned with China’s cyber strategy.
- Clear definition of goals.
- Wide reliance on China Chopper web shell variants.
- Malicious activities primarily within the GMT+8 time zone, during regular working days, and avoiding weekends and holidays.
- Leveraging Operational Relay Box (ORB) networks to proxy traffic and conceal their infrastructure, primarily compromised Zyxel CPE routers operated by Southeast Asian telecommunication providers.
- Malicious DLL deployment.
- Backdoor utilization previously attributed to Chinese APT groups.
Weaver Ant demonstrated exceptional persistence, maintaining activity within the compromised network for over four years, adapting their TTPs to the evolving environment. The modus operandi of Chinese-nexus intrusion sets often involves sharing tools, infrastructure, and manpower, complicating attribution efforts.
Following the eradication of identified web shells, Sygnia implemented enhanced monitoring, anticipating Weaver Ant’s attempts to regain access. This assumption proved correct, as Weaver Ant was detected attempting to resume operations, indicating their persistence and capability.
Related Posts:
- Evil Ant Ransomware Exposed: Flaw Offers Recovery Hope
- Web Shell to Ransomware: New VMware Attack Vector Exposed by Sygnia
- Ant Media Server Flaw Grants Local Users Root Access (CVE-2024-32656)
- China-Nexus Group Velvet Ant Exploits Cisco Zero-Day (CVE-2024-20399)
- Stealthy and Persistent: New Ransomware Tactics Target VMware ESXi