China-Linked GhostEmperor Resurfaces: Enhanced Demodex Rootkit Targets Southeast Asia
The notorious threat group GhostEmperor has resurfaced with an updated version of its sophisticated Demodex rootkit, according to a new report from Sygnia’s Incident Response team. Sygnia’s in-depth analysis uncovered a multi-stage infection chain that begins with a seemingly innocuous batch file, leading to the deployment of the Demodex rootkit on compromised systems. The latest variant incorporates several enhancements, including EDR evasion techniques and a reflective loader for executing the core implant.
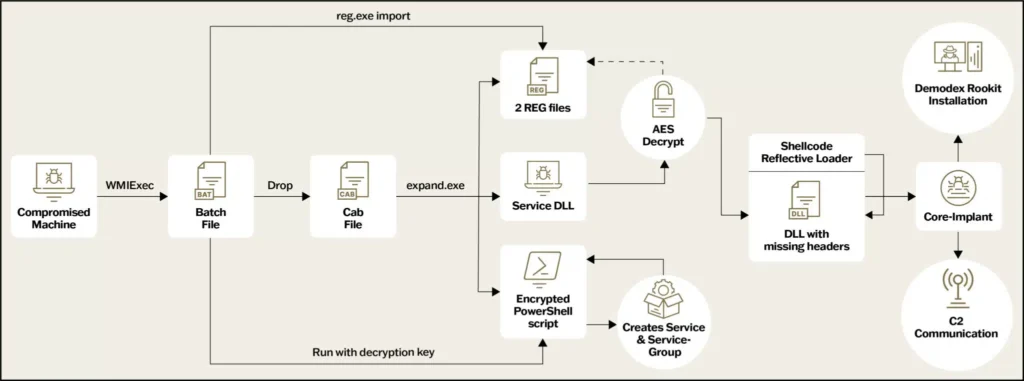
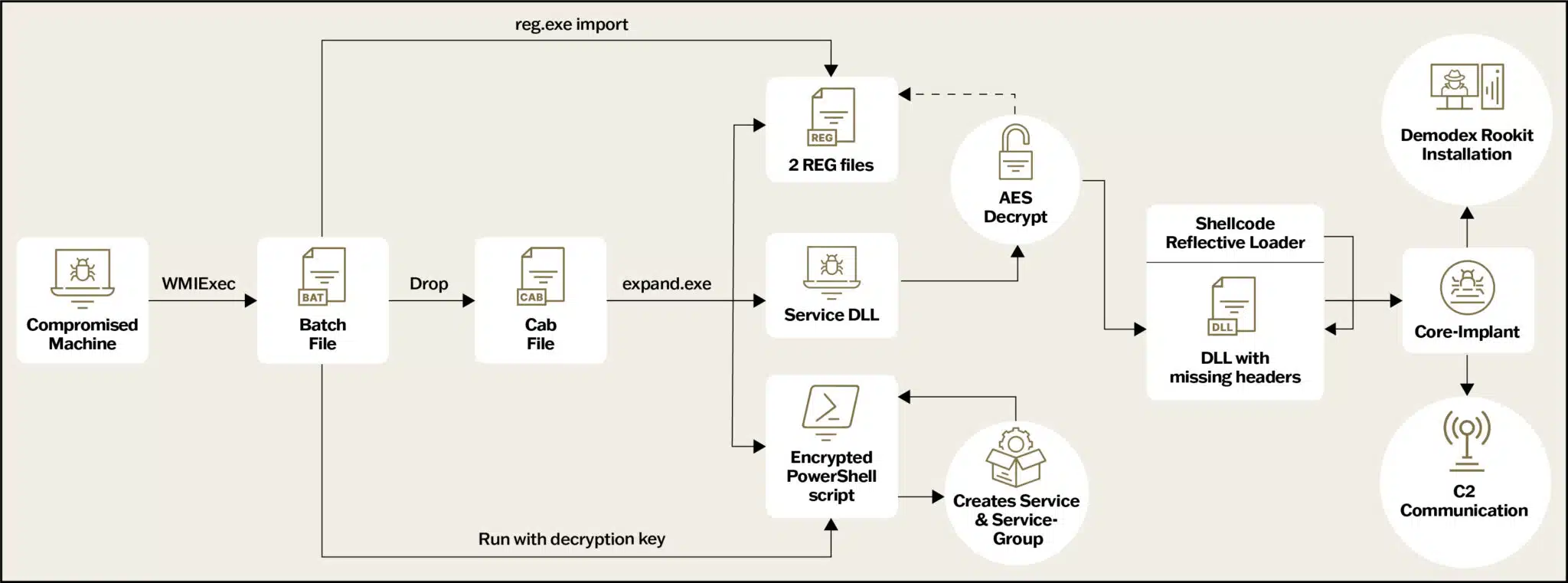
New Infection Chain Flow Graph | Image: Sygnia
The Infection Chain
Stage 1: WMIExec and Initial Compromise
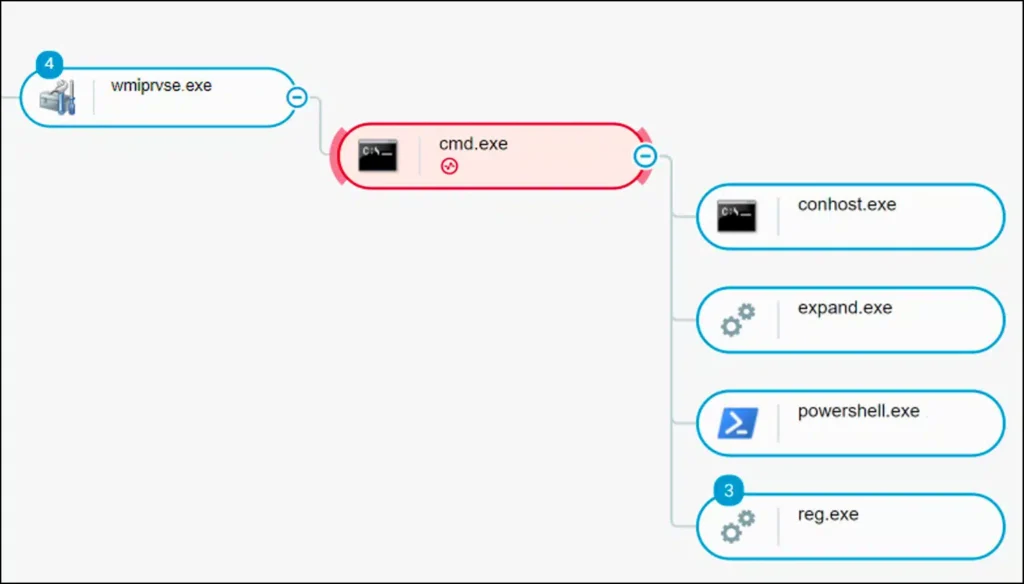
Infection Chain: Process Tree Overview | Image: Sygnia
The attack begins with the use of WMIExec, a command-line tool from the Impacket Toolkit, commonly used for executing commands on remote Windows systems. The threat actor leveraged WMIExec to run a batch file on the victim’s machine, initiating the infection chain. The batch file logs its output to a file located in the c:\windows\temp directory using a local SMB path.
Stage 2: Batch File and Malware Installation
The batch file drops a CAB file named “1.cab” to C:\Windows\Web, then uses expand.exe to extract four files: prints1m.dll (Service DLL), Service.ps1 (encrypted PowerShell script), config.REG (AES decryption key registry dump), and AesedMemoryBinX64.REG (AES-encrypted shellcode containing the Core-Implant). It imports the registry files and executes the encrypted PowerShell script, which decrypts and runs another PowerShell script, setting the stage for further infection.
Stage 3: PowerShell Script and Service Creation
The decrypted PowerShell script creates a new service named “WdiSystem” that loads the malicious Service DLL, prints1m.dll. It also creates a service group called “WdiSystemhost” to masquerade the malware’s execution as a legitimate Windows process. The script sets up the service using the New-Service PowerShell command and modifies registry keys to wire the malicious DLL to the service.
Stage 4: Prints1m.dll – Service DLL Operations
The prints1m.dll dynamically loads necessary functions via the Process Environment Block and decrypts configuration data using a custom scheme. This data includes initial sleep time, shellcode location registry paths, and required module and function names. The service sets up an anti-hooking technique to evade detection and spawns a new thread to execute the next stage, repeatedly attempting decryption and execution until successful.
EDR Evasion and Advanced Techniques
The malware sets a mitigation policy named “ProcessSignaturePolicy” to prevent non-Microsoft signed DLLs from loading, thereby evading antivirus and EDR solutions. This limits the effectiveness of user-mode hooking and helps circumvent security analysis tools.
Stage 5: Shellcode and Reflective Loader
The Service DLL reads encrypted registry keys set by the batch file, decrypts the shellcode using AES, and uses a reflective loader to execute the core-implant DLL. The loader allocates memory, parses custom PE headers, relocates code and data sections, resolves the import table, and executes the Core-Implant.
Core-Implant: Command and Control
The Core-Implant manages C2 communication and installs the Demodex kernel rootkit. The threat actor bypassed Driver Signature Enforcement using the Cheat Engine’s signed driver, dbk64.sys, to execute shellcode in kernel space, enabling the loading of the Demodex driver.
Implications and Concerns
The return of GhostEmperor with an enhanced Demodex rootkit signifies a persistent and evolving threat landscape. The group’s ability to adapt its tactics and techniques to evade detection underscores the need for robust cybersecurity defenses.
The use of legitimate tools and techniques makes it increasingly difficult to identify and mitigate such threats. Organizations must remain vigilant, implement layered security measures, and stay updated on the latest threat intelligence to protect their systems and data.





