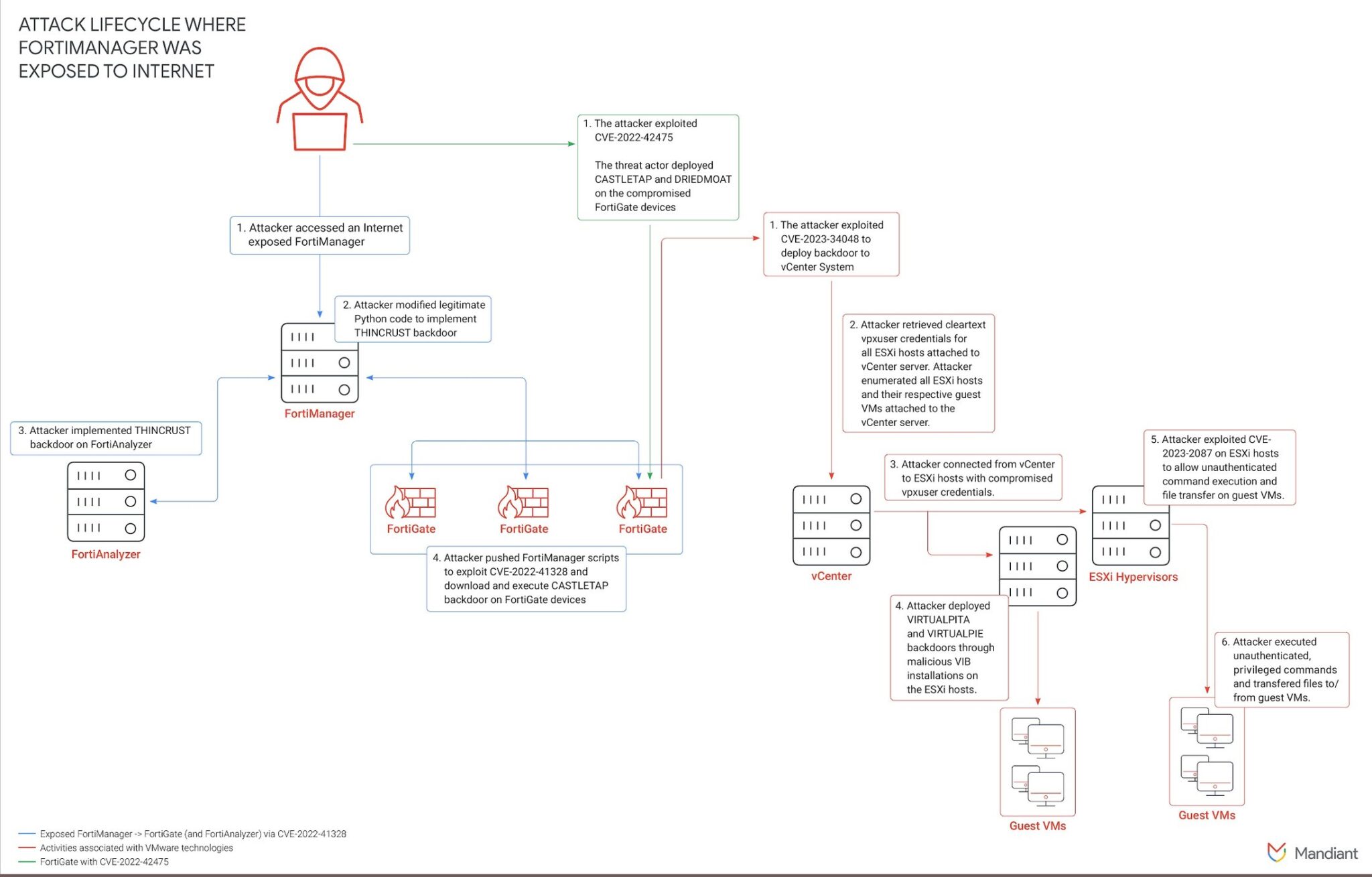
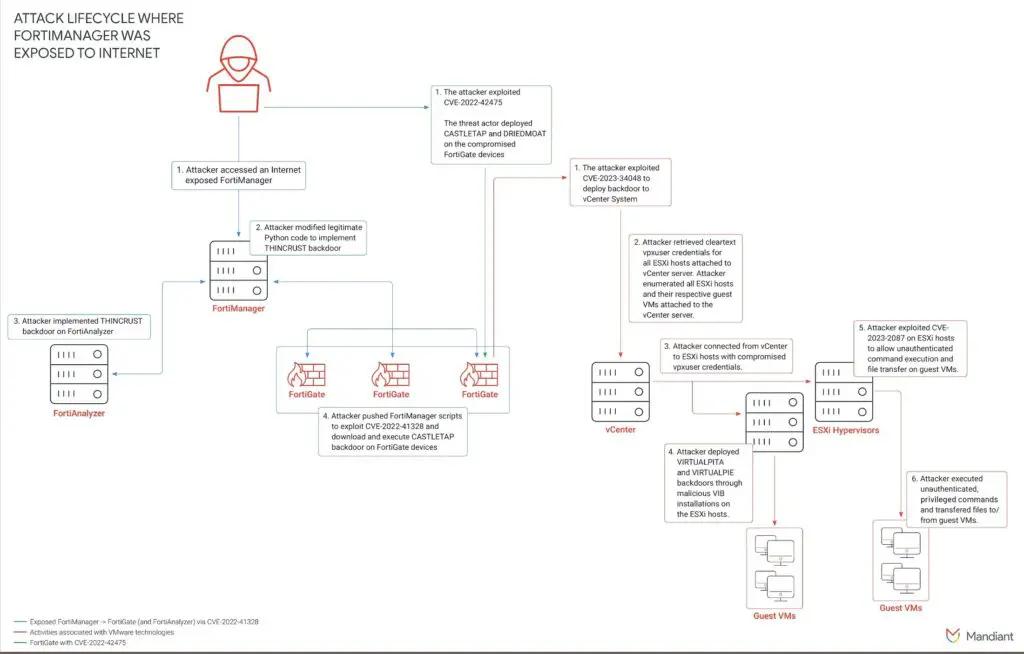
UNC3886 attack path diagram
Cybersecurity firm Mandiant has unveiled a comprehensive report detailing the extensive cyber espionage campaign of UNC3886, a suspected Chinese state-sponsored threat actor. The report exposes the group’s advanced tactics, techniques, and procedures (TTPs) utilized to compromise a wide range of high-profile targets globally.
The investigation began in September 2022, following the discovery of malware within ESXi hypervisors. Mandiant’s analysis uncovered that UNC3886 exploited a now-patched vulnerability in FortiOS, alongside a custom malware ecosystem targeting Fortinet devices. This breach facilitated unauthorized access to VMware technologies and guest virtual machines.
UNC3886’s operations are marked by their meticulous and layered persistence strategies. They ensured sustained access across network devices, hypervisors, and virtual machines, even after detection attempts. This strategy involved using publicly available rootkits like REPTILE and MEDUSA for long-term persistence, leveraging trusted third-party services for command and control (C2), and employing SSH backdoors to harvest credentials.
A significant aspect of UNC3886’s campaign involved exploiting zero-day vulnerabilities. In January 2024, Mandiant detailed the exploitation of CVE-2023-34048 in VMware vCenter, allowing unauthenticated remote command execution. Additional zero-days included:
- CVE-2022-41328 in FortiOS: Enabled backdoor deployment on FortiGate devices.
- CVE-2022-22948 in VMware vCenter: Facilitated credential extraction from vCenter’s postgresDB.
- CVE-2023-20867 in VMware Tools: Enabled unauthenticated guest operations from ESXi hosts.
UNC3886’s primary choice for maintaining access was the REPTILE rootkit, a Linux loadable kernel module (LKM) providing backdoor access and stealth capabilities. REPTILE’s components were customized for unique deployment on compromised endpoints, indicating the threat actor’s long-term use and development.
The MEDUSA rootkit, exploiting dynamic linker hijacking via LD_PRELOAD, logged user credentials and executed commands. MEDUSA’s deployment, though less frequent, suggests an experimental alternative to REPTILE.
UNC3886 deployed malware like MOPSLED and RIFLESPINE, leveraging services like GitHub and Google Drive for C2 communications. MOPSLED, a modular backdoor, and RIFLESPINE, a cross-platform backdoor, were used for initial access and file transfers.
UNC3886 extensively collected and utilized valid credentials for lateral movement across guest virtual machines. Techniques included deploying backdoored SSH clients and daemons, which intercepted and logged credentials.
Mandiant plans to release further details on VMCI-based backdoors like VIRTUALSHINE, VIRTUALPIE, and VIRTUALSPHERE in a future blog post. These backdoors facilitate command execution through VMware VMCI sockets.
For effective defense, Mandiant recommends organizations follow the security guidelines provided in VMware and Fortinet advisories. Additionally, Mandiant has published detection and hardening guidelines for ESXi hypervisors and the techniques used by UNC3886. Indicators of compromise (IOCs) are available for prioritization within Google SecOps Enterprise+ rule packs and Mandiant Advantage.
UNC3886’s activities underscore the importance of vigilant cybersecurity practices and timely patching of known vulnerabilities to safeguard critical systems from advanced persistent threats.