China’s Cyber Espionage Actors Employ ORB Networks to Evade Detection
Mandiant Intelligence has revealed a concerning trend among China-linked cyber espionage groups: the use of Operational Relay Box (ORB) networks to enhance their espionage capabilities. These ORB networks, comprised of compromised virtual private servers (VPS), Internet of Things (IoT) devices, and other end-of-life smart devices, provide a robust infrastructure that obfuscates their operations and raises the cost of defense for enterprise networks.
The Mechanics of ORB Networks
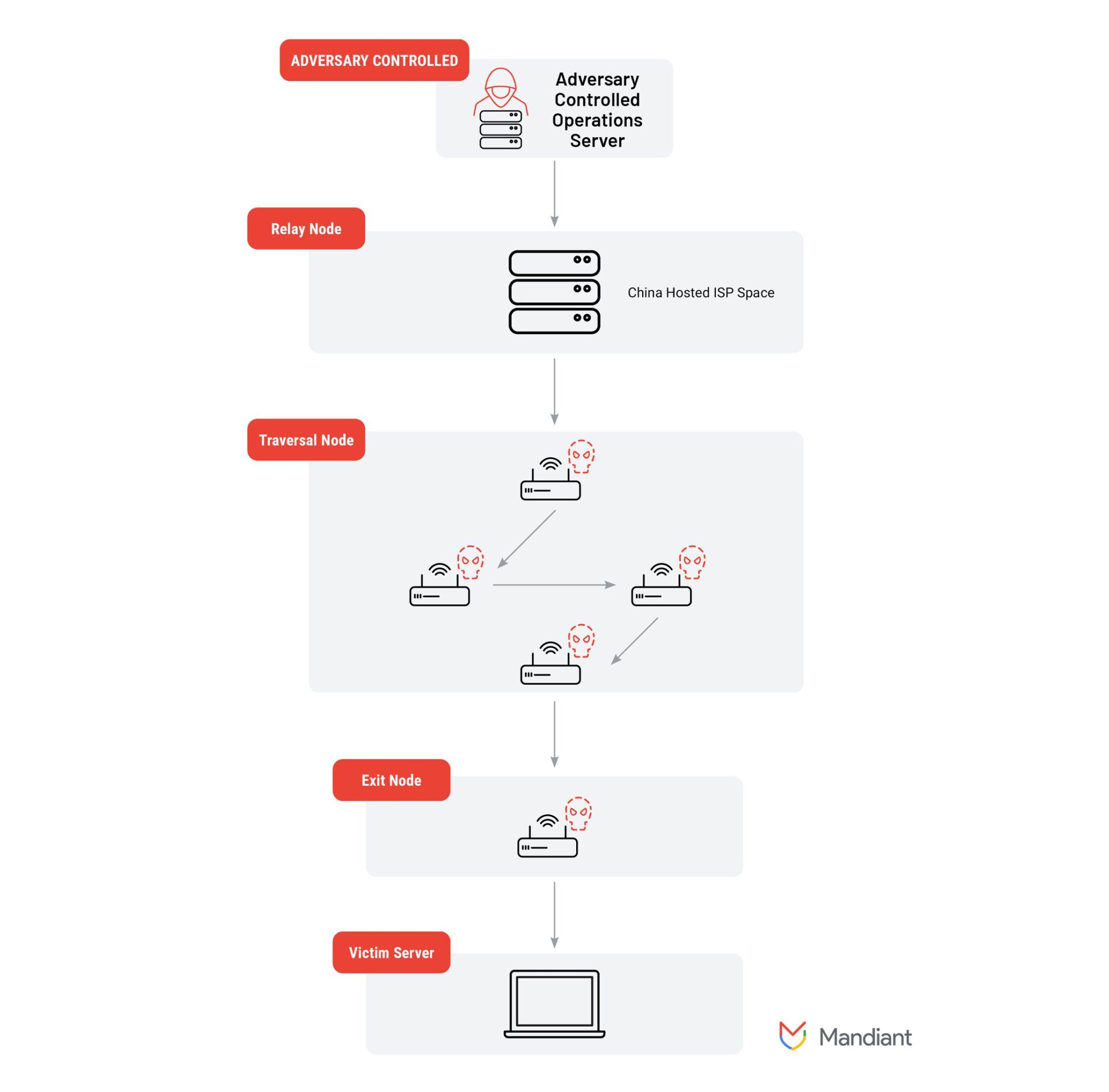
Diagram of the Universal Anatomy of an ORB network | Image: Mandiant
ORB networks function similarly to botnets, leveraging a mix of VPS nodes and compromised devices to create a constantly evolving mesh network. This structure allows cyber espionage actors to mask external traffic between their command and control (C2) infrastructure and their targets, making it significantly more challenging for defenders to detect and attribute attacks.
Key Characteristics of ORB Networks

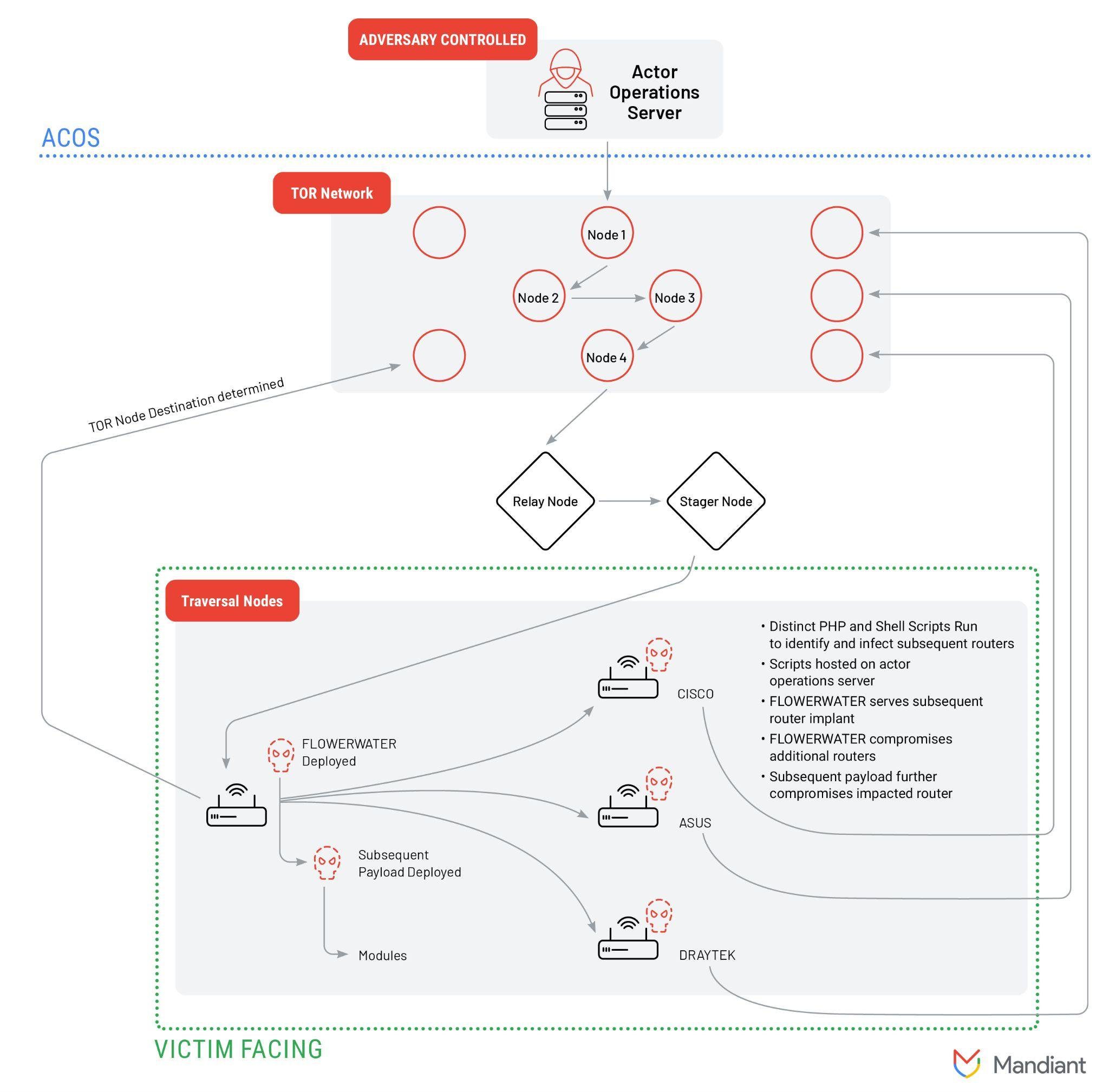
ORB2 / FLORAHOX network diagram | Image: Mandiant
- Disguising Traffic: By utilizing mesh networks, these actors can disguise traffic between C2 infrastructure and victim environments, including edge devices vulnerable to zero-day exploits.
- Expanding Reach: ORB networks can grow by integrating malware-targeted routers and other compromised devices, increasing the volume of traffic relayed within these networks.
- Short-Lived Infrastructure: The lifespan of an IP address within an ORB network can be as short as 31 days, with frequent cycling of infrastructure to evade detection and attribution.
Impact on Network Defense
Mandiant assesses with moderate confidence that the use of ORB networks is a strategic move to complicate defense efforts and shift the advantage towards espionage operators. Traditional methods of blocking adversary infrastructure based on indicators of compromise (IOCs) are becoming less effective as ORB networks evolve.
Paradigm Shift for Defenders
To contend with ORB networks, enterprise defenders must shift from treating adversary infrastructure as static IOCs to viewing them as dynamic entities akin to Advanced Persistent Threat (APT) groups. This involves tracking the behavior and evolution of ORB networks to better anticipate and mitigate attacks.
The Anatomy of an ORB Network
ORB networks consist of several key components:
- Adversary Controlled Operations Server (ACOS): Administers nodes within the ORB network.
- Relay Nodes: Typically leased VPS nodes used to relay traffic through the network.
- Traversal Nodes: The primary volume of nodes, either provisioned or non-provisioned, that relay traffic across the network.
- Exit/Staging Nodes: Actor-controlled nodes used to exit the ORB network and communicate with target environments.
- Victim Server: The targeted infrastructure communicating with the ORB network.
Examples of Active ORB Networks
- ORB3 / SPACEHOP: A provisioned network used by multiple China-linked APTs, including APT5 and APT15. This network has been active since at least 2019 and is known for facilitating network reconnaissance and vulnerability exploitation.
- FLORAHOX: A hybrid network comprising compromised routers, IoT devices, and leased VPS servers. This network is utilized by various China-nexus threat actors, including APT31 and Zirconium.
The Defender’s Dilemma
The widespread adoption of ORB networks by China-linked espionage actors introduces new complexities for defenders:
- Temporality: Identifying current infrastructure within ORB networks.
- Multiplicity of Adversaries: Determining which adversaries are using specific ORB networks.
- Ephemerality: Understanding the transient nature of ORB network infrastructure and its changing characteristics.
Conclusion
The rise of ORB networks represents a significant evolution in cyber espionage tactics, requiring enterprise defenders to adapt their strategies. By treating ORB networks as dynamic entities with distinct tactics, techniques, and procedures (TTPs), defenders can better anticipate and mitigate the threats posed by these sophisticated networks. Mandiant is committed to providing the tools and intelligence necessary for defenders to meet this challenge and protect their networks from evolving cyber threats.





