Qihoo 360 - Diagram
A newly surfaced Chinese cybersecurity report claims to provide a detailed look into NSA (Equation Group) tactics, techniques, and procedures (TTPs), alleging that U.S. cyber operations—referred to as APT-C-40—were behind a 2022 cyberattack on China’s Northwestern Polytechnical University. According to the report, NSA’s elite hacking unit, Tailored Access Operations (TAO), deployed over 40 malware strains to compromise the university’s systems, exfiltrate data, and maintain long-term persistence. The report, authored by Lina L., a co-founder and hacker at XINTRA, provides a detailed analysis of the NSA’s alleged tools and methodologies, offering valuable insights into the group’s sophisticated cyberespionage capabilities.
The report, compiled from Chinese sources including Qihoo 360, Pangu Lab, and the National Computer Virus Emergency Response Center (CVERC), presents what it claims is technical evidence linking the attack to the NSA. However, the authenticity and extent of these allegations remain unverified by independent sources.
Chinese analysts claim they linked the attack to the NSA’s TAO division through a combination of forensic analysis, attack timing, infrastructure tracing, and operator mistakes.
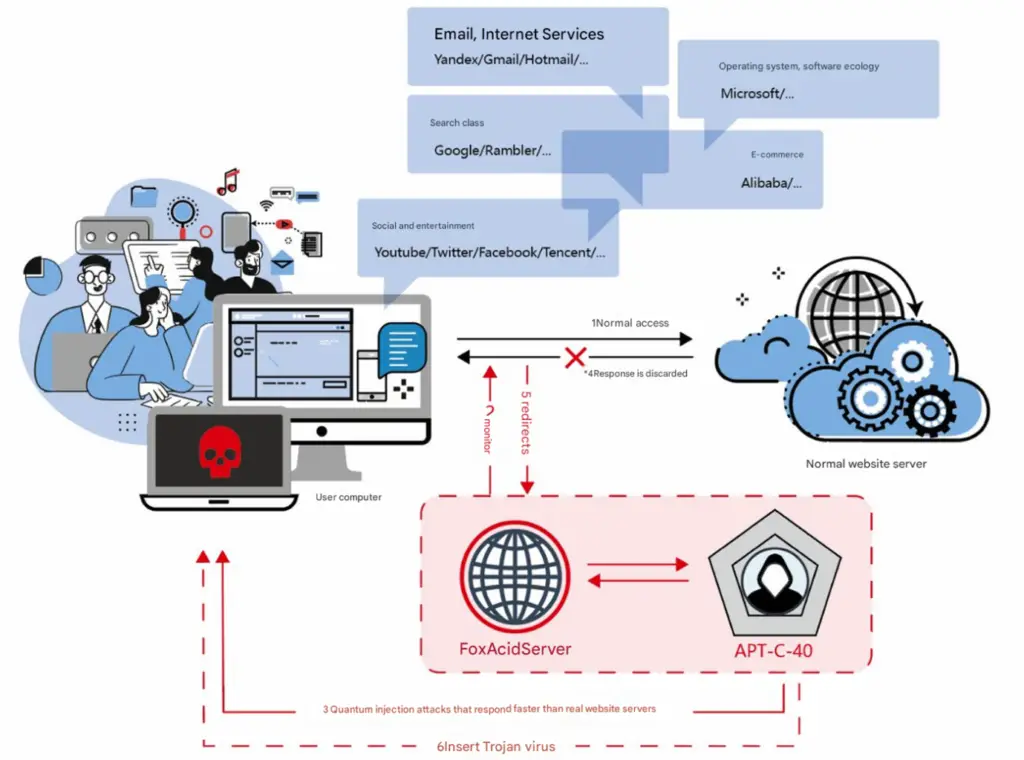
Four IP addresses used in the attack were allegedly purchased through cover companies—”Jackson Smith Consultants” and “Mueller Diversified Systems”—linked to NSA’s FoxAcid platform. NSA allegedly used a U.S.-based domain registrar to anonymize domain ownership.
One alleged NSA operator reportedly failed to modify parameters when running a PyScript tool, triggering an error message that exposed the attacker’s working directory (/etc/autoutils), a known directory for TAO network attack tools.
Attack timing analysis showed a clear correlation to U.S. working hours (Monday-Friday, 9 AM – 4 PM EST), with no activity on U.S. holidays like Memorial Day, Independence Day, or Christmas.
Analysts found 41 different malware samples in the attack. 16 tools matched those leaked in the Shadow Brokers dump of NSA hacking tools. 23 tools had a 97% similarity to other NSA-attributed malware.
According to the Chinese reports, the NSA’s APT-C-40 followed a structured attack pattern:
- Zero-days in SunOS systems were allegedly used to compromise neighboring countries’ networks.
- 54 jump servers and 5 proxy servers in 17 countries were deployed to obfuscate attack origins
- SHAVER – An automated exploitation tool designed for x86 and SPARC architectures running RPC services
- Spear phishing emails targeted university staff with fake “scientific research review” lures.
- Man-in-the-Middle (MITM) attacks redirected university users to NSA-controlled sites.
- FOXACID – A browser exploitation framework that deploys zero-day exploits when users visit Gmail, BiliBili, and other popular sites.
- SECONDDATE – A network eavesdropping tool installed on firewalls and routers to inject malware into web traffic
Once inside the university’s network, Equation Group allegedly deployed advanced backdoors to maintain access and move laterally across devices. Tools were used include:
- NOPEN – A remote-controlled malware that provided persistent access.
- FLAME SPRAY – A Windows-based stealth malware with anti-analysis features.
- CUNNING HERETICS – An encrypted C2 communication backdoor, allowing NSA to reactivate access after system cleanups
NSA allegedly hijacked software update mechanisms to deploy malware disguised as system updates. Attackers stole SSH and Rlogin credentials using DRINKING TEA, allowing deep access to edge routers and firewalls. Hackers used MAGIC SCHOOL to query and exfiltrate telecom and researcher data.
Chinese sources claim NSA operatives exfiltrated classified research data, network configurations, and personnel information using stealthy data extraction methods.
Key Tools Identified:
- OPERATION BEHIND ENEMY LINES – A suite for packaging, encrypting, and exfiltrating stolen data.
- Clown Food & Cursed Fire – NSA tools for extracting telecom and defense-related files
The reports highlight a strong emphasis on edge network devices, including routers, firewalls, and telecom gateways. These are typically overlooked in cybersecurity defenses but provide attackers with long-term stealth access.
Techniques for Evasion & Anti-Forensics:
- TOAST BREAD – A log-wiping tool that erases UTMP, WTMP, and LASTLOG files.
- Encrypted C2 Communications – All tools allegedly used end-to-end encryption to evade detection.
- Firmware Persistence – Implants like STOIC SURGEON targeted Linux, Solaris, and JunOS systems to maintain stealthy access.
The alleged NSA cyber operation against Northwestern Polytechnical University—if true—demonstrates the increasingly sophisticated tactics used in state-sponsored cyber warfare. The focus on edge devices, stealth persistence, and data exfiltration highlights key trends that cyber defenders worldwide must prepare for.
Related Posts:
- NSA can continue its surveillance will depend on Trump?
- Cyclops Blink malware launches persistent attacks on several popular ASUS routers
- Leak: NSA and US Army can capture Tor, I2P, VPNs to monitor Monero users
- Cyberattack on Pacific Islands Forum: Chinese Hackers Suspected
- CrowdStrike Data Leak Claims Spark Concern, Hacktivist Credibility Questioned