Cybersecurity researchers from CloudSEK recently unearthed a malevolent campaign targeting India’s digital payment system, UPI, orchestrated by Chinese fraudsters via counterfeit instant loan applications. Thousands of users have already fallen prey to these swindlers.
Such fraudulent applications allure potential victims with promises of substantial loans and lenient repayment terms. However, once they’ve secured their commissions, these fraudsters vanish, taking with them users’ personal data.
A primary challenge in detecting these deceitful activities is the fraudsters’ utilization of Chinese payment gateways and Indian “money mules.” This significantly hampers transaction transparency and complicates investigations.

The spurious applications, which users willingly install on their smartphones under the guise of “loan processing,” demand an excessive number of permissions, such as access to contacts, photos, and other sensitive information. Yet, the majority of victims found nothing amiss.
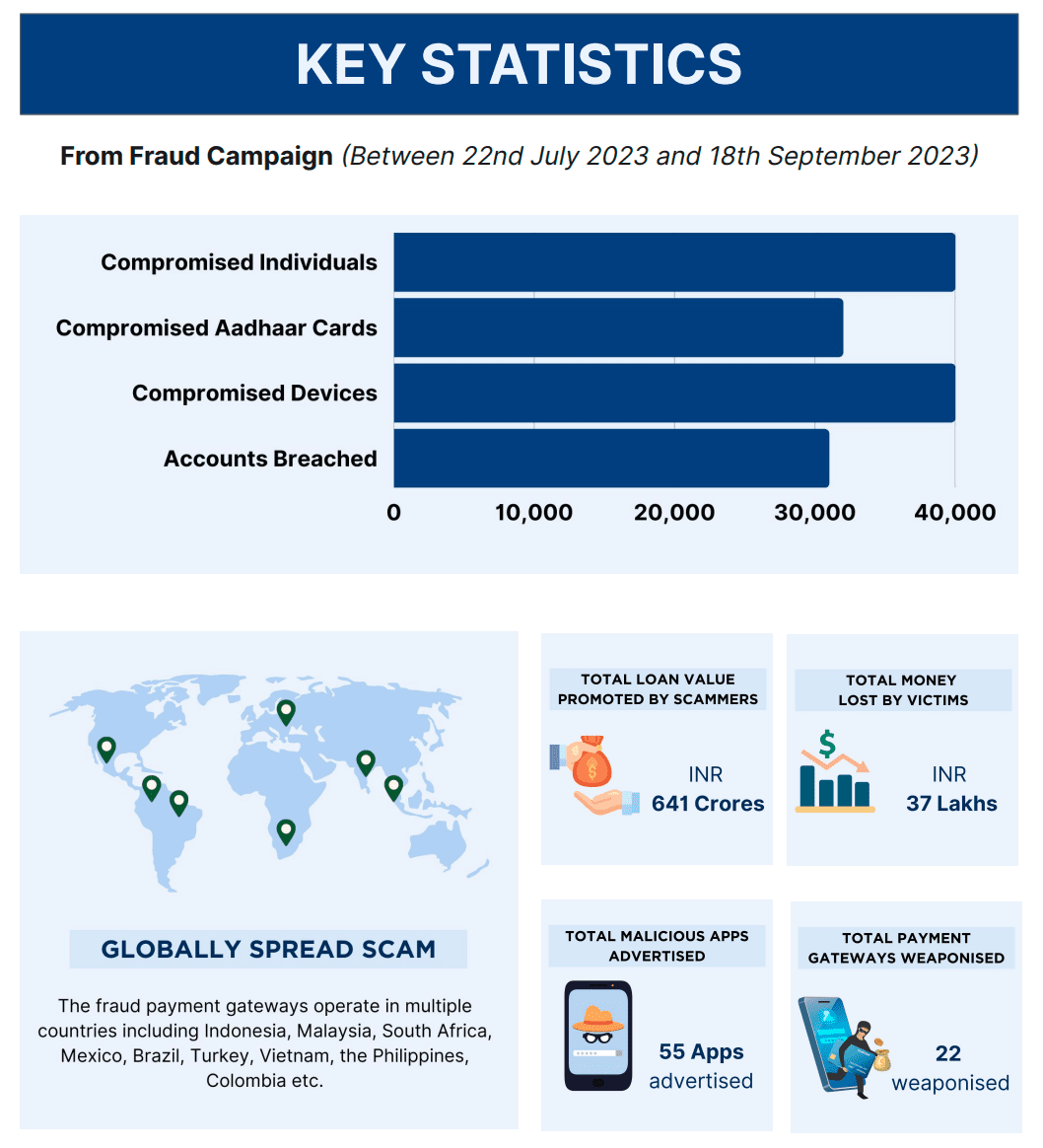
According to CloudSEK data, this deceptive campaign spanned from July 22 to September 18, 2023. The aftermath revealed a compromise of approximately 30,000 Aadhaar cards and bank accounts, 40,000 mobile devices, and a theft exceeding 37 million Indian rupees.
Meanwhile, the campaign’s victims were not limited to India. Malicious activities were also detected in Indonesia, Malaysia, South Africa, Mexico, Brazil, Turkey, Vietnam, the Philippines, and Colombia, suggesting the fraudsters might potentially expand their operations, possibly targeting CIS nations.
A senior security analyst at CloudSEK highlighted that fraudsters frequently resort to Chinese payment gateways due to their relative ease of use and limited regulation.
Combatting such threats necessitates enhanced collaboration between banks and other agencies, a synergy often elusive in its desired form. As experts emphasize, primary attention in thwarting such fraud should focus on fortifying UPI’s security and implementing supplementary protective measures for users.