AiTM workflow | Image credit: Volexity
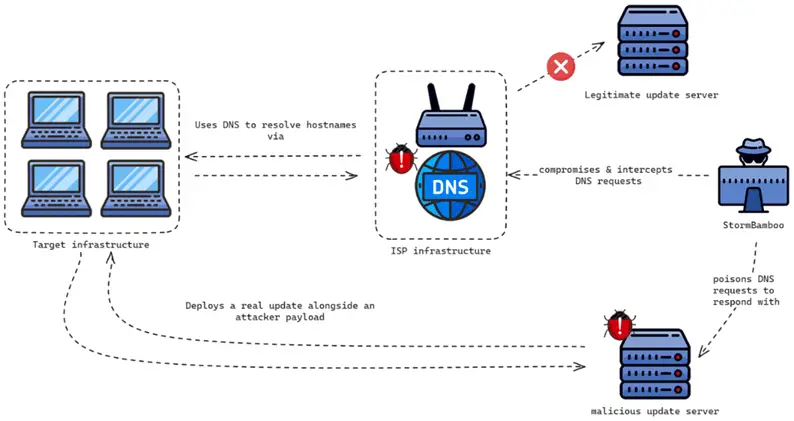
According to a new report from Volexity, in mid-2023, the Chinese group StormBamboo (aka Evasive Panda) infiltrated an ISP’s systems to disseminate malicious software updates among the company’s clients.
In the identified campaign, Evasive Panda targeted an international non-governmental organization (NGO) in mainland China using MgBot. This backdoor was spread through updates to the legitimate Tencent QQ application.
The malicious updates were the result of a DNS spoofing attack at the ISP level. StormBamboo injected malware via the HTTP automatic update mechanism and altered responses for hosts. The DNS records were modified to point to the attackers’ server in Hong Kong. These hosts were subsequently used as command-and-control (C2) servers.
The attack is relatively straightforward: vulnerable update mechanisms are used to deliver MgBot (Windows) or MACMA (MacOS) depending on the operating system in use. Volexity reported the attack to the ISP, which conducted an investigation and rebooted various key devices, after which the campaign ceased immediately.
In one instance, a malicious Google Chrome extension was installed on a macOS device, altering the Secure Preferences file. The extension purportedly aimed to load a page in Internet Explorer compatibility mode, but its primary goal was to steal browser cookies and send them to the attacker’s Google Drive account.
In another recent case, attackers exploited vulnerable automatic update mechanisms in the victim’s software, allowing them to distribute malware without any user interaction. A legitimate application requested updates via HTTP and received a forged configuration file with a URL for downloading a malicious installer. For example, the 5KPlayer application automatically checked for a new version of the “YoutubeDL” component at each startup, and Evasive Panda replaced the configuration file, pointing to the attackers’ server with a modified update.
Evasive Panda has been engaged in cyber espionage since 2012, using backdoors like MgBot (POCOSTICK) and Nightdoor (NetMM, Suzafk) to steal confidential information. The group has recently been linked to the macOS malware known as MACMA, which has been observed in the wild since 2021.
Related Posts:
- PANDA Banker Malware Attacks Bank Institutions, Cryptocurrency Trading Platforms, and Social Media
- Stealthy New Golang Trojan Exploits Fake Certificates for Evasive Communication
- China-Linked Mustang Panda Targets Vietnamese Entities in Cyber Espionage Campaign