Diagram showing deployment and execution of Merlin C2 Agent
Sophos researchers have uncovered a sophisticated and long-running cyberespionage campaign, dubbed Operation Crimson Palace, targeting a high-profile government organization in Southeast Asia. This state-sponsored attack, linked to Chinese threat actors, involved multiple intrusion clusters and the deployment of novel malware variants to exfiltrate sensitive military and technical information.
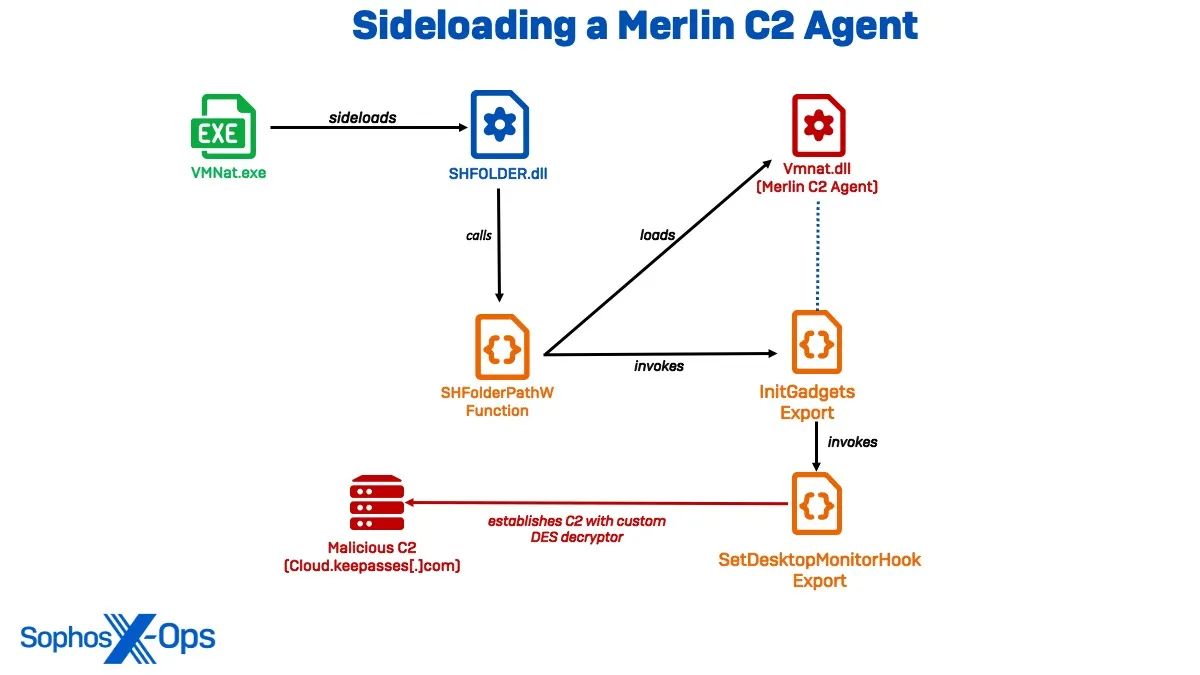
The investigation began with the detection of a DLL sideloading technique exploiting VMNat.exe, a VMware component. Sophos MDR tracked three distinct clusters of intrusion activity from March 2023 to December 2023, revealing previously unreported malware and an improved variant of the EAGERBEE malware. These clusters, identified as Cluster Alpha (STAC1248), Cluster Bravo (STAC1807), and Cluster Charlie (STAC1305), demonstrated a high level of sophistication and coordination.
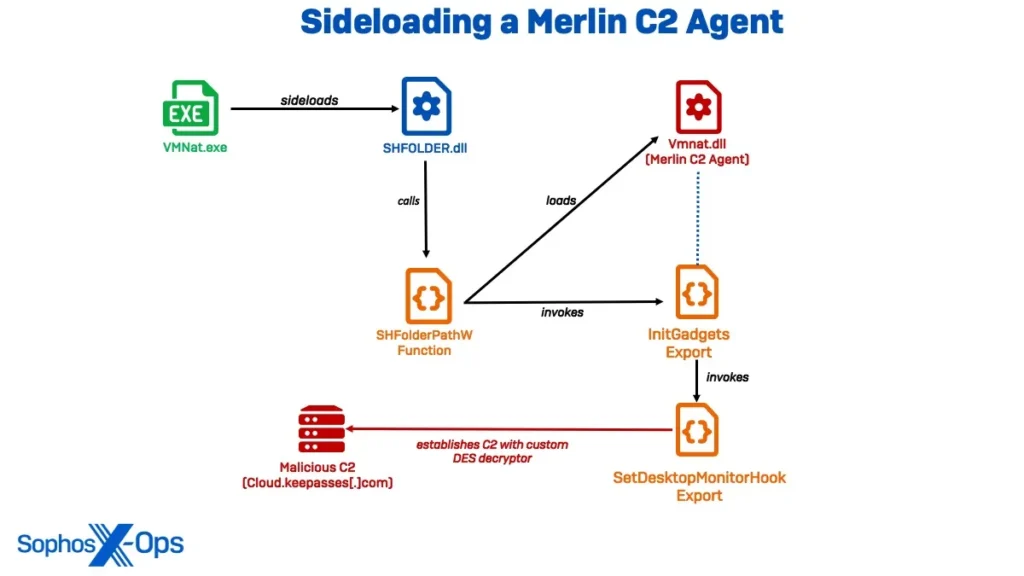
Despite limited visibility into the targeted network, evidence indicated that the threat actors had long-standing access to unmanaged assets within the network, dating back to early 2022. The attackers used tools and infrastructure associated with known Chinese threat actors, such as BackdoorDiplomacy, REF5961, Worok, TA428, Unfading Sea Haze, and APT41 subgroup Earth Longzhi. These actors focused on collecting documents of intelligence value, including military strategies related to the South China Sea.
Sophos’ investigation, conducted with high confidence, concluded that the primary objective of Crimson Palace was to maintain access for cyber espionage supporting Chinese state interests. The attackers targeted critical IT systems, conducted reconnaissance, collected sensitive military and technical information, and deployed various malware implants for command-and-control (C2) communications. The investigation suggests that these activity clusters were part of a coordinated campaign under a single organization.
Sophos has shared its findings with authorized contacts at the targeted organization, as well as government and industry partners, including Elastic Security and Trend Micro, to aid in disrupting related activities.
Organizations, especially those in the government and critical infrastructure sectors, are advised to review their security posture, implement proactive threat hunting measures, and maintain vigilance against evolving cyber threats. Collaboration between cybersecurity researchers, vendors, and government agencies is crucial to effectively combat state-sponsored cyberespionage activities.