Chomp Scan
Chomp Scan is a scripted pipeline of tools to simplify the bug bounty/penetration test reconnaissance phase, so you can focus on chomping bugs.
Scope
Chomp Scan is a Bash script that chains together the fastest and most effective tools (in my opinion/experience) for doing the long and sometimes tedious process of recon. No more looking for word lists and trying to remember when you started a scan and where the output is. Chomp Scan can focus on a list of potentially interesting subdomains, letting you save time and focus on high-value targets. It can even notify you via Notica when it’s done running!
Chomp Scan now integrates Notica, which allows you to receive a notification when the script finishes. Simply visit Notica and get a unique URL parameter, e.g. notica.us/?xxxxxxxx. Pass the parameter to Chomp Scan via the -n flag, keep the Notica page open in a browser tab on your computer or phone, and you will receive a message when Chomp Scan has finished running. No more constantly checking/forgetting to check those long running scans.
A list of interesting words is included, such as dev, test, uat, staging, etc., and domains containing those terms are flagged. This way you can focus on the interesting domains first if you wish. This list can be customized to suit your own needs, or replaced with a different file via the -X flag.
It runs in multiple modes. A new Configuration File is the recommended way to run scans, as it allows the most granular control of tools and settings. A standard CLI mode is included, which functions the same as any other CLI tool. A guided interactive mode is available, as well as a non-interactive mode, useful if you do not want to lookup parameters or worry about setting multiple arguments.
New Chomp Scan now includes rescope. Rescope will parse all resolved domains discovered by Chomp Scan and generate a JSON scope file that can be imported into Burp Suite. This option can be enabled by setting the ENABLE_RESCOPE variable in the configuration file or by passing the -r flag via the command line.
Note: Chomp Scan is in active development, and new/different tools will be added as I come across them. Pull requests and comments welcome!
Scanning Phases
Subdomain Discovery (3 different sized wordlists)
Screenshots (optional)
Port Scanning (optional)
- masscan and/or nmap
- nmap output styled with nmap-bootstrap-xsl
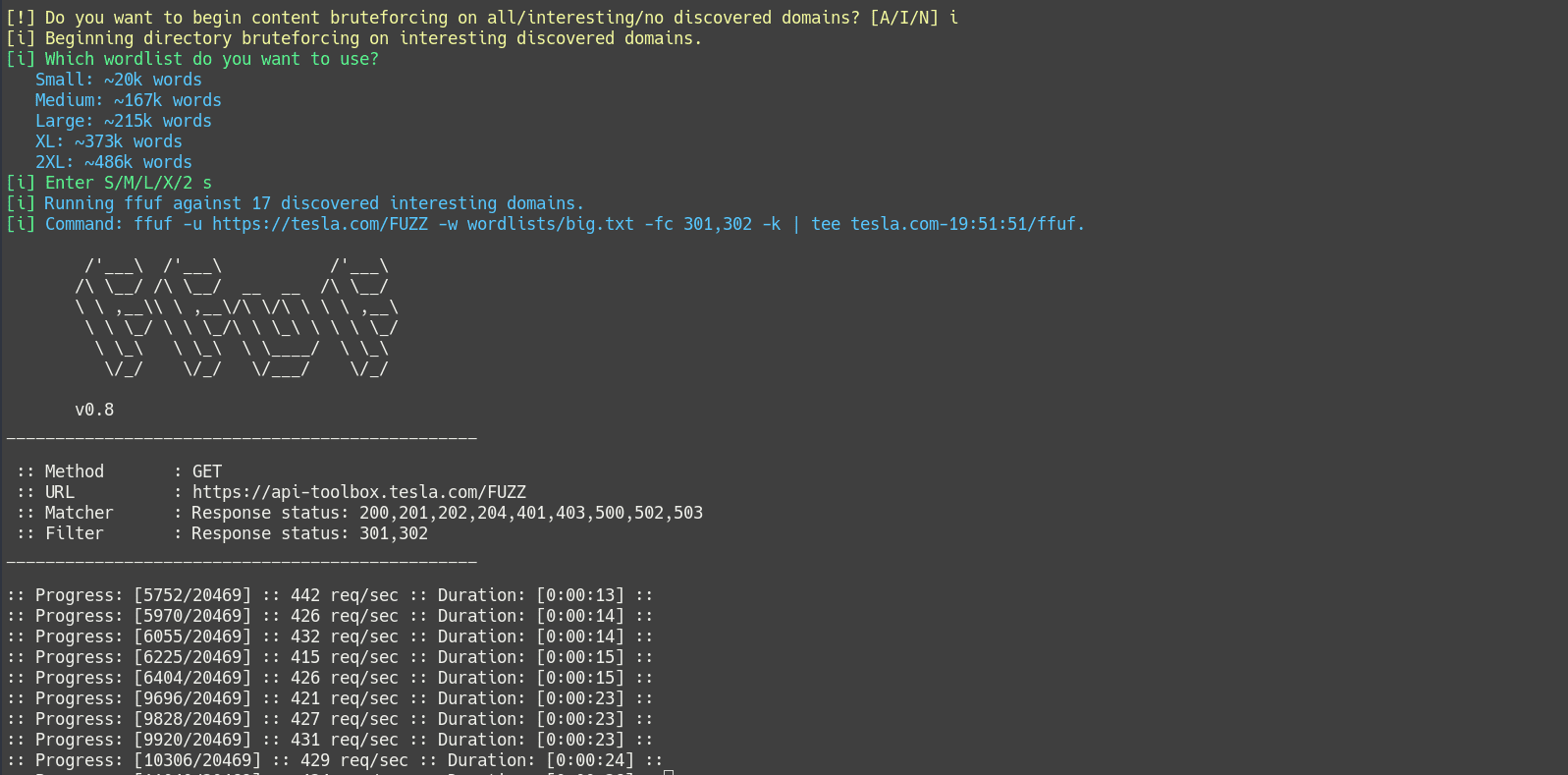 Information Gathering (optional) (4 different sized wordlists)
Information Gathering (optional) (4 different sized wordlists)
Content Discovery (optional) (4 different sized wordlists)
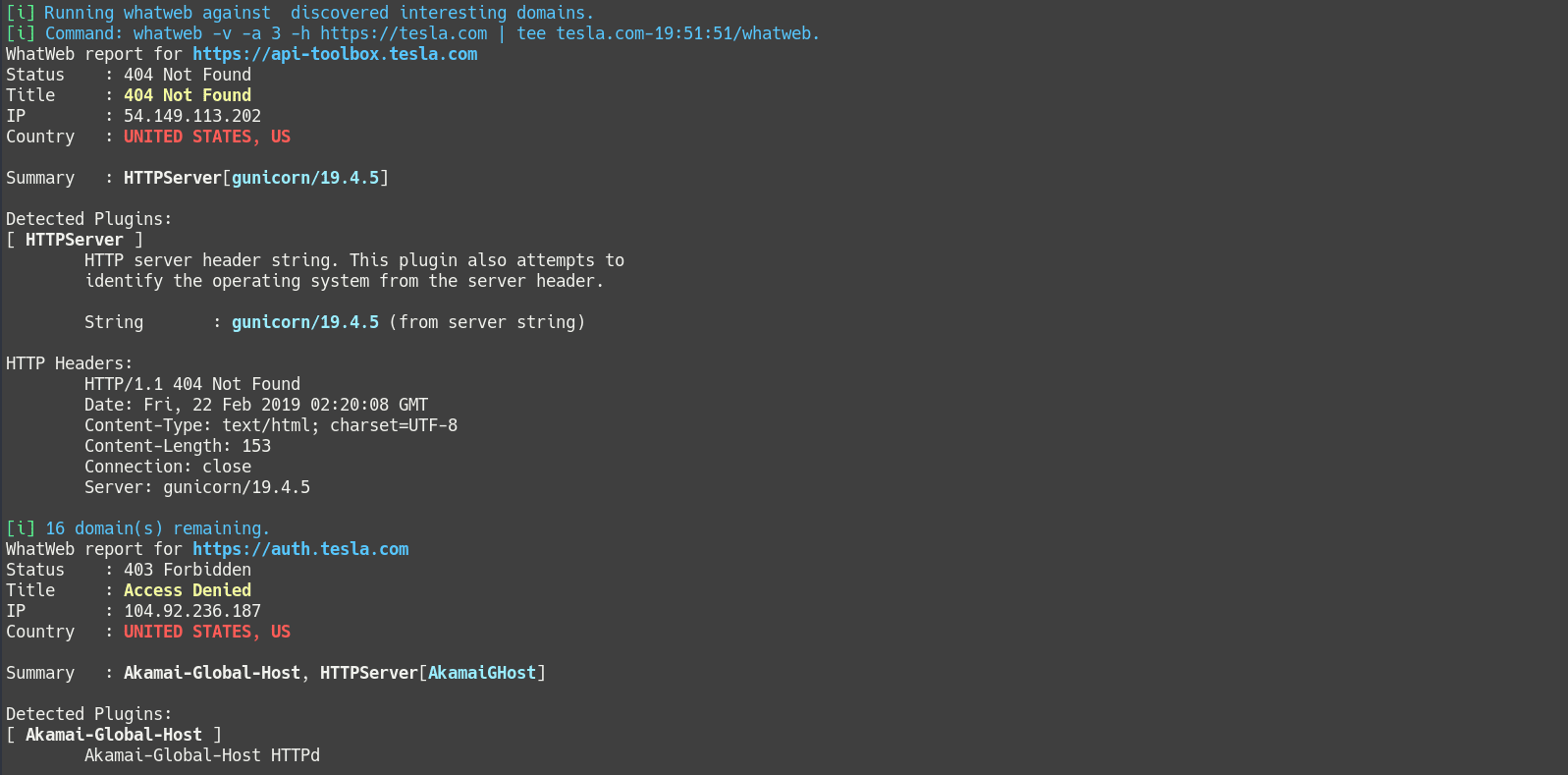 Configuration File
Configuration File
Chomp Scan now features a configuration file option that provides more granular control over which tools are run and is less cumbersome than passing a large number of CLI arguments. It is the recommended way to run Chomp Scan. It can be used by passing the -L flag. An example config file is included in this repo as a template, and complete config file details are available at the Configuration File wiki page.
Wordlists
A variety of wordlists are used, both for subdomain bruteforcing and content discovery. Daniel Miessler’s Seclists are used heavily, as well as Jason Haddix’s lists. Different wordlists can be used by passing in a custom wordlist or using one of the built-in named argument lists.
Install && Use
Copyright (C) 2019 SolomonSklash