chomtesh: automate reconnaissance tasks during penetration testing
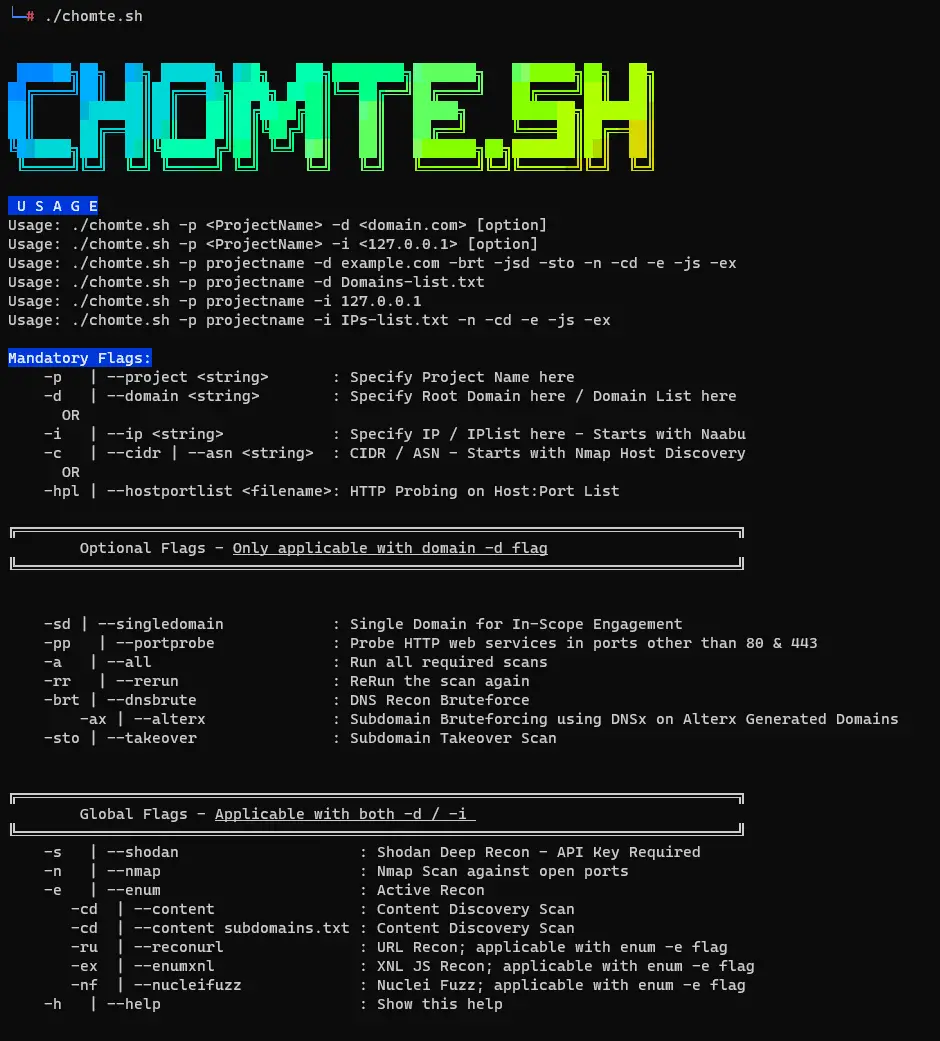
CHOMTE.SH
CHOMTE.SH is a versatile framework designed for automating reconnaissance tasks in penetration testing. It’s useful for bug bounty hunters and penetration testers in both internal and external network engagements. Its key features include subdomain gathering, DNS subdomain brute-forcing, quick port scanning, HTTP probing, service enumeration, and generating reports in various formats. Additionally, it performs content discovery, identifies common misconfigurations and vulnerabilities, conducts deep internet reconnaissance, provides command transparency, and specializes in JavaScript reconnaissance. Users can customize tool arguments by modifying the flags.conf file.

Major Features
CHOMTE.SH has the following features:
- Gather Subdomains using subfinder: This feature allows you to gather subdomains using the subfinder tool.
- DNS Subdomain Bruteforcing using dmut: This feature enables DNS subdomain bruteforcing using the dmut tool.
- Quick Port Scan using Naabu: This feature allows for quick port scanning using the Naabu tool.
- HTTP Probing using projectdiscovery HTTPX: This feature allows for HTTP probing using the projectdiscovery HTTPX tool to generate a CSV file.
- Service Enumeration using Nmap: This feature enables service enumeration using Nmap by scanning ports that are only open on the host.
- Nmap Report Format: This feature allows you to generate reports in XML, NMAP, CSV, and HTML (raw and styled) formats.
- Content Discovery Scan: Find sensitive files exposed in WebApplications
- Common Misconfigurations & Vulnerabilities of Infrastructure / WebApplications
- Internet Deep Recon: Shodan / Certificate Transperency
- Command Transperency: You will able to see commands what is running, where it is saving files…
- JavaScript Reon: Hardcoded credentials / Sensitive Keys / Passwords
- Customizable Flags: Tool arguments can be change by modifying flags.conf file





