ChopChopGo: Rapidly Search and Hunt through Linux Forensics Artifacts
ChopChopGo
ChopChopGo inspired by Chainsaw utilizes Sigma rules for forensics artifact recovery, enabling rapid and comprehensive analysis of logs and other artifacts to identify potential security incidents and threats on Linux.
Features
- 🎯 Hunt for threats using Sigma detection rules and custom ChopChopGo detection rules
- ⚡ Lightning fast, written in go
- 🪶 Clean and lightweight execution and output formats without unnecessary bloat
- 💻 Runs on Linux
Use

Example
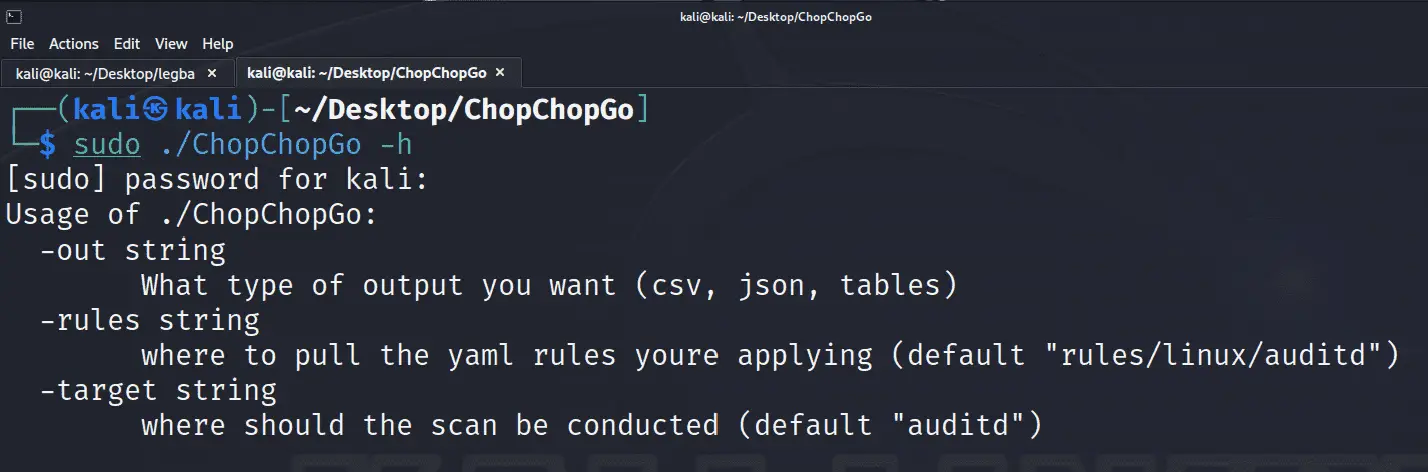
./ChopChopGo # Defaults to searching through auditd
./ChopChopGo -target syslog -rules ./rules/linux/builtin/syslog/ # This searches through syslog with the official sigma rules
./ChopChopGo -target journald -rules ./rules/linux/builtin/ # This searches through journald with specified rules
Alternative Output Formats
You may wish to use ChopChopGo in an automated fashion. The CSV and JSON output options are useful for this purpose. With both of these options, the header and progress statistics are not printed on the console.
Each option can be specified using the -out parameter.
CSV
./ChopChopGo -target sylog -rules ./rules/linux/builtin/syslog/ -out csv # This searches through syslog with the official sigma rules, then outputs the data in CSV format
JSON
./ChopChopGo -target syslog -rules ./rules/linux/builtin/syslog/ -out json # This searches through syslog with the official sigma rules, then outputs the data as JSON
Install
Copyright (C) 2023 M00NLIG7





