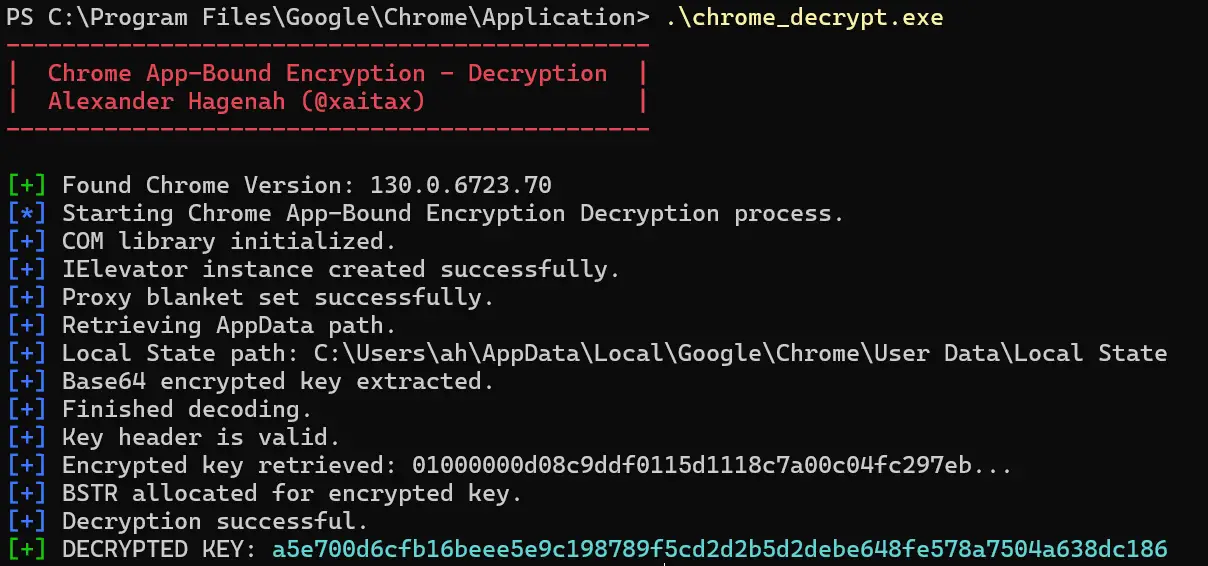
A newly released open-source tool has successfully decrypted keys protected by Chrome’s App-Bound Encryption, raising concerns about the long-term efficacy of this security feature.
Google Chrome’s App-Bound Encryption (ABE), introduced in version 127, aimed to bolster user security by linking decryption capabilities to specific applications. This prevented malicious programs from accessing sensitive data like cookies, passwords, and payment information.
Developed by Alexander Hagenah, this tool exploits Chrome’s internal COM-based IElevator service to retrieve and decrypt App-Bound encrypted keys stored within the browser’s Local State file. This revelation comes on the heels of reports that several infostealer malware strains, including Meduza, WhiteSnake, Lumma, Vidar, and StealC, had already developed their own methods to circumvent ABE.
While Google’s intention with ABE was to “increase the cost of data theft to attackers and also make their actions far noisier on the system,” Hagenah’s tool potentially undermines these efforts. By making the decryption process readily accessible, it could empower less sophisticated threat actors to pilfer user data.
As Harris, a Chrome security team member, acknowledged, “As the malware landscape continually evolves we are keen to continue engaging with others in the security community on improving detections and strengthening operating system protections, such as stronger app isolation primitives, for any bypasses.”
The release of this open-source tool underscores the need for continuous innovation and collaboration between browser developers and the security community. It remains to be seen how Google will respond to this latest challenge and whether further enhancements to ABE or alternative security measures will be necessary to safeguard user information.
Related Posts:
- Infostealers Overcome Chrome’s App-Bound Encryption, Threatening User Data Security
- Google Chrome Strengthens Cookie Security on Windows with App-Bound Encryption
- Bitdefender released GandCrab Ransomware decryption tool
- Mozilla releases emergency update to fix two exploited zero-day vulnerabilities in Firefox
