CISA Adds Microsoft Streaming Service CVE-2023-29360 Flaw to KEV Catalog! PoC Published
On February 29th, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) added a recently patched security flaw (CVE-2023-29360) in Microsoft Streaming Service to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation.
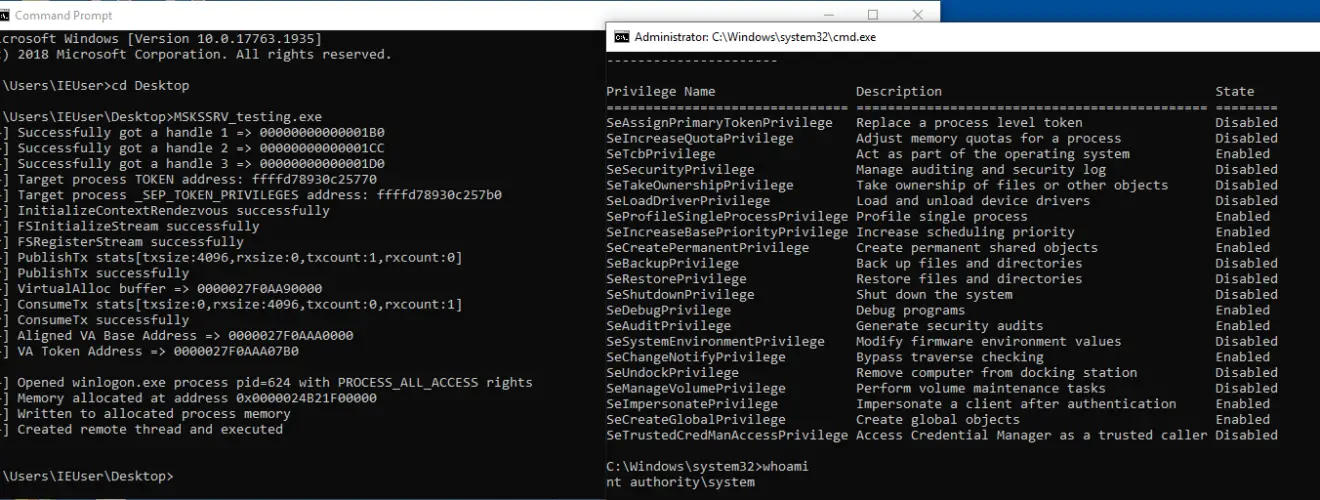
A Wolf in Sheep’s Clothing: The ‘mskssrv’ Driver
At the heart of CVE-2023-29360 lies a seemingly mundane component of Microsoft 365 – the Microsoft Streaming Service. This service, a cornerstone for video sharing, is seamlessly intertwined with other familiar apps in the Microsoft suite. What’s less innocuous is the ‘mskssrv’ driver, where the trouble lurks.
The danger stems from an untrusted pointer being misused for reference. Imagine your computer mistaking a stranger’s address for your own… that’s the kind of risky situation created by this pointer problem. It provides a gateway for privilege escalation, meaning a crafty attacker could worm their way into obtaining full ‘SYSTEM’ privileges. This level of access is akin to hacking an administrator account, granting hackers unfettered control over the vulnerable system.
Risk Assessment: It’s Not Looking Good
Evaluated under the CVSSv3.1, this vulnerability has been assigned a base score of 8.4. Microsoft has categorized its severity as ‘Important‘, the second-highest level of urgency in a four-tier system, and addressed it in their June 2023 security update. Public disclosure and the existence of easily accessible proof-of-concept (PoC) codes have further armed malicious actors, effectively giving them blueprints to exploit this weakness.
Protecting Yourself: Agencies Mobilize, So Should You
Recognizing the severity, CISA has mandated that FCEB agencies patch the vulnerability by March 21, 2024. However, this doesn’t just apply to federal agencies. Here’s what everyone needs to do:
- Stay In the Know: Regularly check for security updates from Microsoft and apply them immediately. Updates are the lifeblood of protection against such flaws.
- Proactive Defense: Employ reputable antivirus and endpoint protection software with the latest threat definitions. A good security suite will have mechanisms to detect and often prevent exploits related to this vulnerability.
- Be Vigilant: Exercise extra caution with links, emails, and suspicious activity. Avoid opening attachments you weren’t expecting or clicking links from unknown sources.






