The Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent warning about three actively exploited security vulnerabilities affecting a wide range of software, including Microsoft Windows, Mozilla Firefox, and SolarWinds Web Help Desk. These flaws have been added to CISA’s Known Exploited Vulnerabilities (KEV) catalog, signaling the critical need for immediate patching.
Windows Kernel Vulnerability Tied to Iranian APT
The first vulnerability, CVE-2024-30088, is a Windows Kernel Elevation of Privilege flaw that allows attackers to escalate their privileges to SYSTEM level. Discovered in the Windows kernel, this vulnerability is triggered by a race condition that attackers can exploit, giving them full control over a system. Although CISA has not linked this flaw to a specific campaign, Trend Micro researchers have pointed out that the OilRig threat actor—an Iranian-based group—has been using this exploit to target Microsoft Exchange servers for credential theft and privilege escalation
CVE-2024-30088 was patched by Microsoft in June 2024, but the ongoing exploitation in the wild necessitates immediate action for organizations using unpatched systems. The vulnerability has a CVSS score of 7.0, and systems running unpatched versions of Windows are at risk of being fully compromised by attackers exploiting this flaw.
Firefox Zero-Day Under Active Attack
Mozilla has confirmed reports of active exploitation of CVE-2024-9680, a critical use-after-free vulnerability in Firefox’s animation timelines. This flaw enables attackers to achieve code execution in the content process, potentially leading to arbitrary code execution and system compromise. The vulnerability affects Firefox, Firefox ESR, and Thunderbird across multiple versions.
SolarWinds Web Help Desk Exposes Sensitive Data
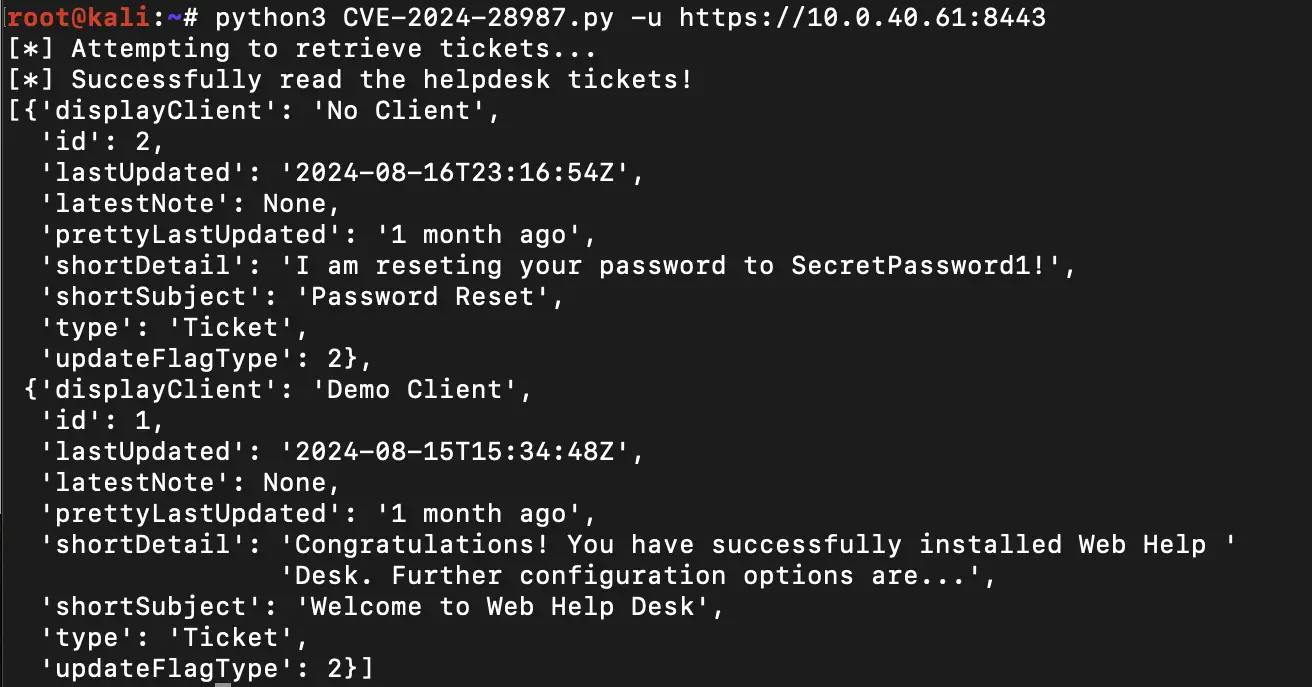
CVE-2024-28987 impacts SolarWinds Web Help Desk (WHD) software. This flaw, discovered by Zach Hanley from Horizon3.ai, involves hardcoded credentials within the Web Help Desk application. Attackers can remotely access the system without authentication, allowing them to modify help desk tickets and access sensitive data. With a CVSS score of 9.1, this vulnerability is extremely severe, as it can expose sensitive data, such as passwords from reset requests and shared service account credentials. SolarWinds users are urged to update to version 12.8.3 Hotfix 2 to patch this vulnerability. The fix requires prior installation of Web Help Desk 12.8.3.1813 or 12.8.3 HF1.
Urgent Action Required
CISA has mandated that all Federal Civilian Executive Branch (FCEB) agencies patch these vulnerabilities by November 5, 2024. However, all users and organizations are strongly urged to apply the available updates immediately.
Related Posts:
- SolarWinds Web Help Desk Hit by Critical Vulnerability (CVE-2024-28987)
- Earth Simnavaz Exploits Windows Kernel Flaw CVE-2024-30088 in Attacks on Critical Infrastructure
- PoC Exploit Release for Windows Kernel-Mode Driver Elevation of Privilege Flaw (CVE-2024-35250)
- SolarWinds Patches Multiple Critical Vulnerabilities in Access Rights Manager
- CVE-2024-28986 (CVSS 9.8): SolarWinds Web Help Desk Users Must Patch Now!