Image: watchtowr
The Cybersecurity and Infrastructure Security Agency (CISA) has recently added three new vulnerabilities to its Known Exploited Vulnerabilities Catalog, signaling an urgent call to action for cybersecurity professionals and system administrators. These vulnerabilities are being actively exploited in the wild, posing significant risks to organizations.
1. Edimax IP Camera Flaw Exploited to Spread Mirai Botnet (CVE-2025-1316)
A critical vulnerability (CVE-2025-1316) in Edimax IC-7100 network cameras is being leveraged by malicious actors to distribute Mirai botnet malware. This flaw, a high-severity operating system command injection vulnerability (CVSS v4 score: 9.3), allows attackers to remotely execute code on vulnerable devices through specially crafted requests.
Akamai, a web infrastructure and security company, reported that exploit attempts targeting this vulnerability date back to May 2024, despite a proof-of-concept (PoC) exploit being publicly available since June 2023. The attacks target the /camera-cgi/admin/param.cgi endpoint in Edimax devices, injecting commands into the NTP_serverName option.
Compounding the issue, attackers are reportedly using default credentials (admin:1234) to gain unauthorized access. At least two different Mirai botnet variants have been identified exploiting this vulnerability, with one incorporating anti-debugging functionality. The ultimate goal of these campaigns is to infect devices and incorporate them into a network capable of launching distributed denial-of-service (DDoS) attacks.
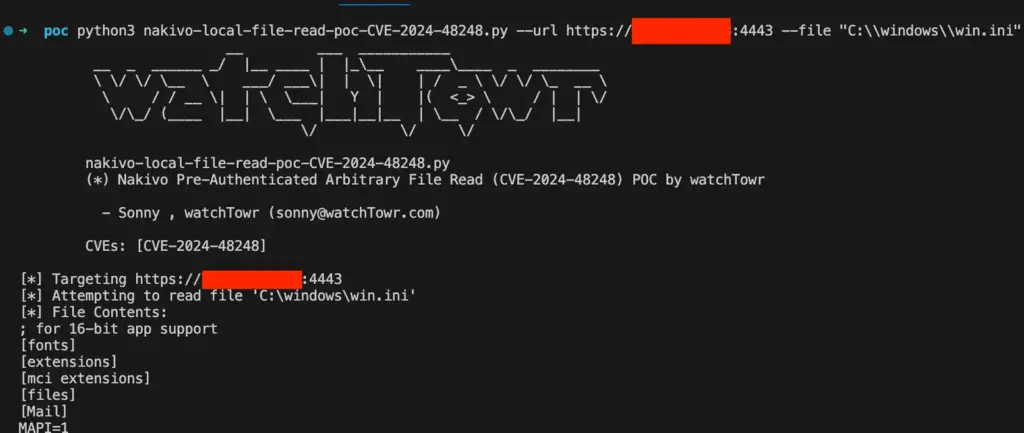
2. NAKIVO Backup and Replication Vulnerability Exposes Sensitive Data (CVE-2024-48248)
NAKIVO Backup and Replication software contains an absolute path traversal vulnerability (CVE-2024-48248) that allows attackers to read arbitrary files. This vulnerability, with a CVSS score of 8.6, was discovered by researchers at watchTowr while assessing the resilience of NAKIVO’s backup and replication products.
watchTowr security researcher “Sonny” revealed that the vulnerability was found in version 10.11.3.86570 of the product, but earlier versions were not checked. The vulnerability resides in the Director component, NAKIVO’s central management HTTP interface. Exploitation of this flaw could enable attackers to steal backups and credentials, potentially compromising entire infrastructure environments.
The implications of this vulnerability are severe, especially given the increasing focus of ransomware gangs on targeting backup and recovery solutions. NAKIVO has silently patched the vulnerability in version 11.0.0.88174. WatchTowr has also released a tool to help NAKIVO customers assess their exposure.
3. SAP NetWeaver Directory Traversal Vulnerability (CVE-2017-12637)
A directory traversal vulnerability (CVE-2017-12637) in SAP NetWeaver Application Server Java 7.5 allows remote attackers to read arbitrary files via a “..” (dot dot) in the query string. This vulnerability was exploited in the wild as early as August 2017.
Recommendations
Given the ongoing active exploitation of these vulnerabilities, CISA has mandated that Federal Civilian Executive Branch (FCEB) agencies apply the necessary patches by April 9, 2025.. It is strongly recommended that organizations:
- Apply patches immediately: Prioritize patching the identified vulnerabilities in Edimax IP cameras, NAKIVO Backup and Replication, and SAP NetWeaver Application Server Java.
- Review security configurations: Ensure default credentials are changed, and access controls are strictly enforced.
- Monitor for suspicious activity: Implement robust monitoring and intrusion detection systems to identify and respond to potential exploitation attempts.
- Assess exposure: Utilize available tools, such as the one provided by watchTowr for NAKIVO, to determine the extent of potential vulnerability within their systems.
Related Posts:
- Veeam Backup & Replication Vulnerabilities Exposed: High-Severity Flaws Put Data at Risk
- CVE-2025-1316: Edimax Network Cameras Exploited to Spread Mirai Malware
- CISA Warns of Critical Edimax IP Camera Flaw (CVE-2025-1316) with Public Exploits and No Vendor Fix
- Researchers Detail Critical PHP Flaw CVE-2024-4577 with PoC Exploit Code
- PoC Exploit Released for Ivanti Connect Secure Flaw CVE-2025-0282 Used in Attacks