On June 20th, local time, Cisco officially released a security notice that fixed several different levels of security vulnerabilities, including five serious vulnerabilities.

CVE-2018-0301 (Critical)
A vulnerability in the NX-API functionality of Cisco NX-OS software may allow unauthenticated remote attackers to send malicious packets to the management interface of the affected system, resulting in a buffer overflow.
The vulnerability is due to incorrect input validation in the authentication module of the NX-API subsystem. An attacker could exploit this vulnerability by sending a well-crafted HTTP or HTTPS packet to the management interface of an affected system that has the NX-API feature enabled. The vulnerability could allow an attacker to execute arbitrary code as root. Note: The NX-API is disabled by default.
CVSS 3.0 Rating:
Base 9.8 CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H/E:X/RL:X/RC:X
Affected products and versions:
The following Cisco products are affected by this vulnerability:
- MDS 9000 Series Multilayer Switches
- Nexus 2000 Series Fabric Extenders
- Nexus 3000 Series Switches
- Nexus 3500 Platform Switches
- Nexus 5500 Platform Switches
- Nexus 5600 Platform Switches
- Nexus 6000 Series Switches
- Nexus 7000 Series Switches
- Nexus 7700 Series Switches
- Nexus 9000 Series Switches in standalone NX-OS mode
- Nexus 9500 R-Series Line Cards and Fabric Modules
The affected Cisco NX-OS software versions in the above products are detailed here.
Solution:
Upgrade to the safe version suggested in this link.
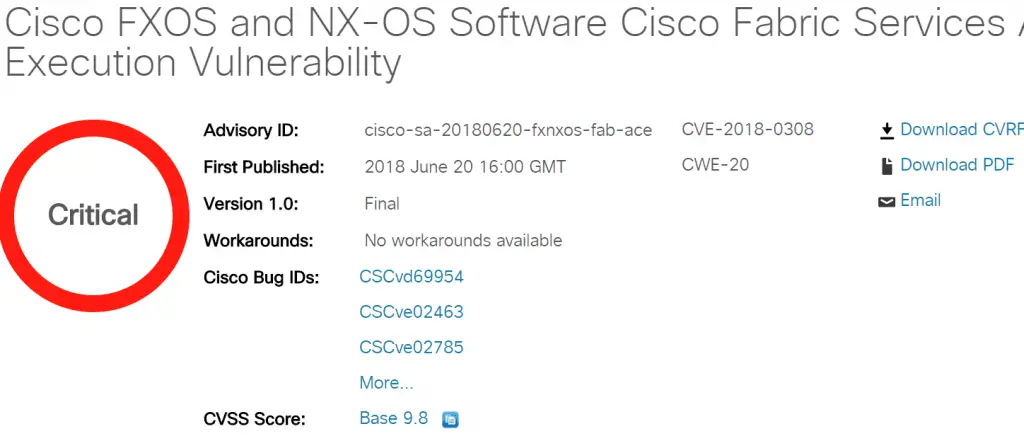
CVE-2018-0308 (Critical)
Vulnerabilities in Cisco Fabric Services (CFS) components in Cisco FXOS software and NX-OS software may allow unauthenticated remote attackers to execute arbitrary code or cause a denial of service attacks.
This vulnerability exists because the affected software does not fully validate the header values in Cisco Fabric Services packets. An attacker could exploit this vulnerability by sending specially crafted Cisco Fabric Services packets to affected devices. A successful attack may cause a buffer overflow, allowing an attacker to execute arbitrary code or cause a DoS.
CVSS 3.0 Rating:
Base 9.8 CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H/E:X/RL:X/RC:X
Affected products and versions:
The following Cisco products are affected by this vulnerability:
- Firepower 4100 Series Next-Generation Firewalls
- Firepower 9300 Security Appliance
- MDS 9000 Series Multilayer Switches
- Nexus 2000 Series Fabric Extenders
- Nexus 3000 Series Switches
- Nexus 3500 Platform Switches
- Nexus 5500 Platform Switches
- Nexus 5600 Platform Switches
- Nexus 6000 Series Switches
- Nexus 7000 Series Switches
- Nexus 7700 Series Switches
- Nexus 9000 Series Switches in standalone NX-OS mode
- Nexus 9500 R-Series Line Cards and Fabric Modules
- UCS 6100 Series Fabric Interconnects
- UCS 6200 Series Fabric Interconnects
- UCS 6300 Series Fabric Interconnects
The affected Cisco FXOS or NX-OS software versions in the above products are described in this link.
Solution:
Upgrade to the safe version suggested in this link.
CVE-2018-0304 (Critical)
Vulnerabilities in Cisco Fabric Services (CFS) components in Cisco FXOS software and NX-OS software may allow unauthenticated remote attackers to read sensitive memory content, create a denial of service conditions, or execute arbitrary code as root.
This vulnerability exists because the affected software does not fully validate the Cisco Fabric Services packet headers. An attacker could exploit this vulnerability by sending specially crafted Cisco Fabric Services packets to affected devices. A successful attack may allow an attacker to cause buffer overflows or buffer reads in the Cisco Fabric Services component. This may allow an attacker to read sensitive memory information, create a denial of service condition, or execute arbitrary code as root.
CVSS 3.0 Rating:
Base 9.8 CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H/E:X/RL:X/RC:X
Affected products and versions:
The following Cisco products are affected by this vulnerability:
- Firepower 4100 Series Next-Generation Firewalls
- Firepower 9300 Security Appliance
- MDS 9000 Series Multilayer Switches
- Nexus 2000 Series Fabric Extenders
- Nexus 3000 Series Switches
- Nexus 3500 Platform Switches
- Nexus 5500 Platform Switches
- Nexus 5600 Platform Switches
- Nexus 6000 Series Switches
- Nexus 7000 Series Switches
- Nexus 7700 Series Switches
- Nexus 9000 Series Switches in standalone NX-OS mode
- Nexus 9500 R-Series Line Cards and Fabric Modules
- UCS 6100 Series Fabric Interconnects
- UCS 6200 Series Fabric Interconnects
- UCS 6300 Series Fabric Interconnects
The affected Cisco FXOS or NX-OS software versions in the above products are described in this link.
Solution:
Upgrade to the safe version suggested in this link.
CVE-2018-0314 (Critical)
A vulnerability in Cisco Fabric Services (CFS) components in Cisco FXOS software and NX-OS software may allow unauthenticated remote attackers to execute arbitrary code on the affected devices.
This vulnerability exists because the affected software did not fully validate the Cisco Fabric Services packet header when processing the packet. An attacker could exploit this vulnerability by sending maliciously configured Cisco Fabric Services packets to affected devices. A successful attack may allow an attacker to cause a buffer overflow on the device, allowing the attacker to execute arbitrary code on the device.
CVSS 3.0 Rating:
Base 9.8 CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H/E:X/RL:X/RC:X
Affected versions:
The following Cisco products are affected by this vulnerability:
- Firepower 4100 Series Next-Generation Firewalls
- Firepower 9300 Security Appliance
- MDS 9000 Series Multilayer Switches
- Nexus 2000 Series Fabric Extenders
- Nexus 3000 Series Switches
- Nexus 3500 Platform Switches
- Nexus 5500 Platform Switches
- Nexus 5600 Platform Switches
- Nexus 6000 Series Switches
- Nexus 7000 Series Switches
- Nexus 7700 Series Switches
- Nexus 9000 Series Switches in standalone NX-OS mode
- Nexus 9500 R-Series Line Cards and Fabric Modules
- UCS 6100 Series Fabric Interconnects
- UCS 6200 Series Fabric Interconnects
- UCS 6300 Series Fabric Interconnects
The affected Cisco FXOS or NX-OS software versions in the above products are described in the detail.
Solution:
Upgrade to the safe version suggested in this link.
CVE-2018-0312 (Critical)
Vulnerabilities in Cisco Fabric Services (CFS) components in Cisco FXOS software and NX-OS software may allow unauthenticated remote attackers to execute arbitrary code or cause a denial of service attacks on the affected devices.
This vulnerability exists because the affected software did not fully validate the Cisco Fabric Services packet header when processing the packet. An attacker could exploit this vulnerability by sending maliciously configured Cisco Fabric Services packets to affected devices. A successful attack may allow an attacker to cause a buffer overflow on the device, allowing an attacker to execute arbitrary code or cause a denial of service on the device.
CVSS 3.0 Rating:
Base 9.8 CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H/E:X/RL:X/RC:X
Affected versions:
The following Cisco products are affected by this vulnerability:
- Firepower 4100 Series Next-Generation Firewalls
- Firepower 9300 Security Appliance
- MDS 9000 Series Multilayer Switches
- Nexus 2000 Series Fabric Extenders
- Nexus 3000 Series Switches
- Nexus 3500 Platform Switches
- Nexus 5500 Platform Switches
- Nexus 5600 Platform Switches
- Nexus 6000 Series Switches
- Nexus 7000 Series Switches
- Nexus 7700 Series Switches
- Nexus 9000 Series Switches in standalone NX-OS mode
- Nexus 9500 R-Series Line Cards and Fabric Modules
- UCS 6100 Series Fabric Interconnects
- UCS 6200 Series Fabric Interconnects
- UCS 6300 Series Fabric Interconnects
The affected Cisco FXOS or NX-OS software versions in the above products are described in the detail.
Solution:
Upgrade to the safe version suggested in this link.