Cisco Talos experts are actively monitoring several malicious campaigns utilizing NetSupport RAT for persistent infections. These campaigns evade detection through obfuscation and regular updates.
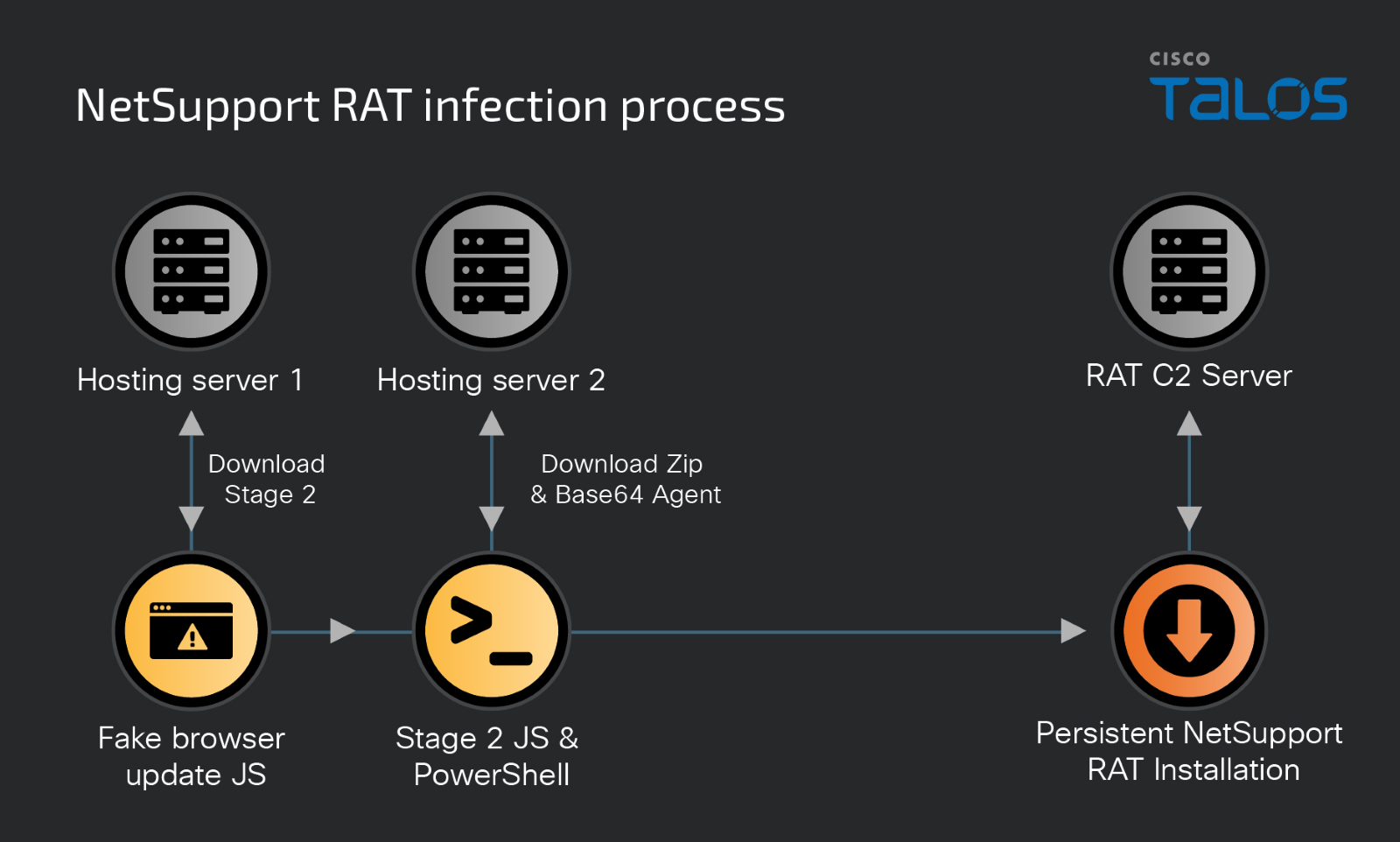
In November 2023, security vendors identified a new campaign using NetSupport RAT, which employed fake browser updates to deceive users and download malicious code. This code downloads and executes PowerShell commands, installing the NetSupport agent on the victim’s machine to maintain persistence.
In January 2024, eSentire researchers published another analysis of the same campaign, revealing changes in the original JavaScript code and the agent’s installation path. These changes demonstrate the attackers’ efforts to enhance obfuscation and evasion techniques.
Cisco Talos conducted its analysis and identified numerous obfuscation and evasion methods used in the campaign. With this knowledge, accurate detection tools were developed to help users protect themselves. Talos utilizes open-source tools such as Snort and ClamAV to develop detection and protection methods.
NetSupport Manager has existed since 1989 and is used for remote device management. However, since 2017, malicious actors have repurposed it for their ends. The shift to remote work in the 2020s led to increased use of NetSupport RAT in phishing and drive-by attacks. This campaign is one of the most significant in recent years, with hundreds of malicious loaders used in a widespread advertising campaign.
The first stage of the campaign involves a JavaScript file, downloaded from advertising sites or compromised resources. This file is obfuscated and contains the loader for the next stage. The second stage includes a PowerShell script, which downloads and launches the NetSupport agent, maintaining its persistence in the system registry.
Snort rules are used to detect the campaign, allowing the identification of malicious files and their transmission through various protocols. These rules also help track PowerShell activities and other indicators of NetSupport RAT presence.
The continuous evolution of malware and attack tactics requires cybersecurity specialists to maintain constant vigilance and adaptability. It is crucial to remember that even legitimate tools can be misused by malicious actors. Thus, critical thinking and caution when interacting with any online resources are essential skills for every user today.
Related Posts:
- Hackers are trying to install NetSupport Remote Access Tool on victim machine through Fake Software Update
- NetSupport RAT Wielded in Escalating Cyber Attacks: Educational Institutions, Government Agencies, and Service Businesses at Risk
- Unveiling the NetSupport Threat: McAfee Researchers Delve into the Malware’s Tactics
- Cisco’s Talos found a hacking campaign that targets iPhone users
- PhantomBlu Campaign Unleashes Stealthy Attack – Old RAT, Dangerous New Tricks