Security experts at the Cisco Talos team have recently discovered a “highly targeted” hacking campaign that uses a mobile malware that has been active for at least since August 2015. Security experts believe that the attackers located in the country of India, and only 13 iPhones are infected.
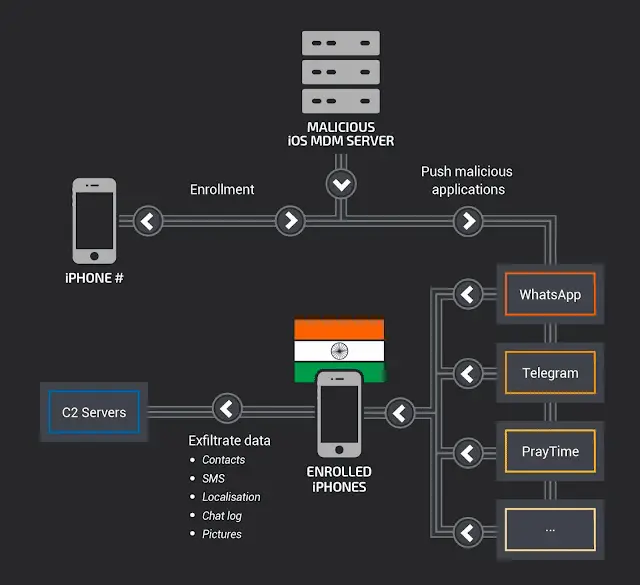
Also, the attack is considered to be performed using a Mobile Device Management (MDM) server. MDM servers are often used to provide employees with certain custom applications in an enterprise environment that are not available through the iOS official app store due to their sensitive nature.
According to the Talos team, they discovered the MDM server used by the attacker. A total of 13 models of the iPhone were registered, and the attacker’s goal was to install a malicious version of some popular legitimate software on these phones, including the aforementioned mobile malware with data collection.

The models of infected iPhones include iPhone 5.4, iPhone 7.2, iPhone 8.1, iPhone 8.2, iPhone 9.3, and iPhone 9.4. iOS versions include 10.2.1, 10.3.1, 10.3.2, 10.3.3, 11.0, 11.0.3, 11.2. .1, 11.2.5 and 11.2.6.
The Talos team said the attackers used a total of four malicious versions of the app: WhatsApp, Telegram, PrayTime, and MyApp. The attacker used BOptions sideloading technology to inject malicious code into the application’s dynamic library, and the malicious code not only does not interfere with the normal functioning of the phone, but the app itself also implements the functions it describes.
This is not to say that malicious code is meaningless, it is designed to collect specific data silently. Malicious code in the WhatsApp and Telegram applications can collect and reveal data from victims such as phone numbers, serial numbers, locations, contacts, photos, text messages, and WhatsApp and Telegram messages.
Malicious code in the PrayTime app only collects text messages and also includes the ability to display ads on infected devices. The Talos team said it’s unclear why an attacker would add such a feature because playing an ad on the phone might alert the victim to malware infection.
For MyApp, it does not contain any malicious code and does not carry out any malicious behavior. The Talos team believes that attackers only use it for testing.
Interestingly, the attacker tried to disguise as a Russian hacker during the attack, and the certificate used by the MDM server contained the email address (mail.ru) in Russia. However, the Talos team found that the test device registered on the MDM server had an Indian phone number and that this number was registered with the Indian network provider.
Currently, the Talos team has shared their findings with Apple, and Apple has also revoked the certificates used by the attackers. More details about this attack can be seen in the Talos team blog post, including IoC.
Source, Image: Cisco Talos