Cisco issued a security alert on Wednesday that hackers have used malware to infect at least 500,000 routers and storage devices in at least 54 countries. According to Cisco Researcher Craig Williams, Cisco Talos Security believes that the Russian government was behind the attack because the codes of the software used by the hackers and the Russian government launched a cyber attack. The software code is consistent.

“By this point, we were aware of the code overlap between BlackEnergy and VPNFilter, that Ukraine’s Constitution Day was approaching in June, and that the timing of previous attacks in Ukraine suggested that an attack could be imminent.”
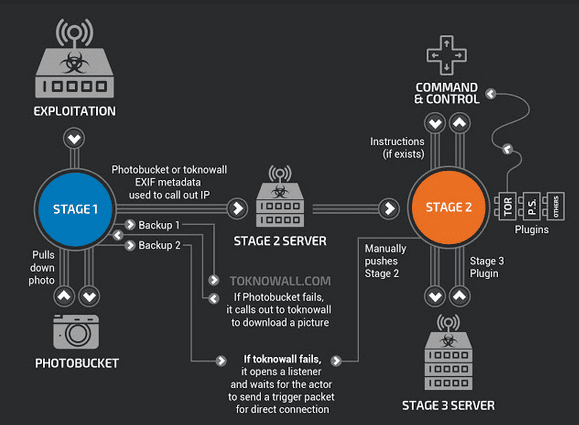
Currently, we’ve seen that this attack allows for deployment of a sniffer that is looking for information on regular networks and industrial control systems. These are computer systems that manage such entities as water and power plants. We’ve also seen the attacker has created a TOR network (an anonymous network of devices) that can share data and enable the attacker to carry out a coordinated mass attack.
Finally, this malware could be used to conduct a large-scale destructive attack by using the ‘kill’ command, which would render some or all of the physical devices unusable.“
From the current point of view, an attacker may use VPNFilter to perform the following actions:
- Monitor network traffic and intercept sensitive network credentials;
- Monitor the flow of traffic to SCADA equipment and deploy malicious software specifically targeted at industrial control system infrastructure;
- Use this botnet’s “broiler” to hide the source of other malicious attacks;
- Make the router paralyzed, resulting in the Ukrainian most of the Internet infrastructure is not available.
Cisco said it is currently working with public and private entities to identify devices infected by VPNFilter and eliminate it before launching the attack. The Ukrainian Secret Service has issued security warnings.
On May 23, 2018, the U.S. government stated that it will seek to rescue hundreds of thousands of infected routes and storage devices that were hacked and controlled.
The FBI agent holding a court order has taken control of an important server in the botnet, discovered the victim of the botnet, and severely thwarted the botnet’s ability to re-infect the target. According to TheDailyBeast, VPNFilter is related to the Russian hacking organization Fancy Bear (aka APT28).
Court records show that the FBI has been investigating the VPNFilter botnet since August 2017 when FBI agents learned about a victim in Pittsburgh, USA (home router was infected). The victim voluntarily gave the router to the FBI agent and also allowed the FBI to use the network tap on its home network to observe network traffic.
Source, Image: talosintelligence