
The notorious cyber-espionage group Cloud Atlas, active since 2014, has been observed leveraging a new arsenal in its ongoing campaigns against Eastern Europe and Central Asia, according to a detailed report from Kaspersky Labs.
At the main of the latest campaign is a newly identified backdoor, VBCloud. This module integrates capabilities previously handled by multiple components, streamlining data collection and exfiltration tasks while maintaining stealth. Kaspersky Labs notes: “This new campaign loads VBCloud via VBShower, which also downloads the PowerShower module. PowerShower probes the local network and facilitates further infiltration, while VBCloud collects information about the system and steals files.”
According to Kaspersky, the group continues to rely on phishing emails as the primary attack vector. These emails contain malicious documents exploiting CVE-2018-0802, a vulnerability in the Microsoft Equation Editor. Once opened, the document downloads a malicious template formatted as an RTF file from a remote server controlled by the attackers. This initiates a multi-stage infection chain that ultimately delivers the VBShower and VBCloud backdoors.
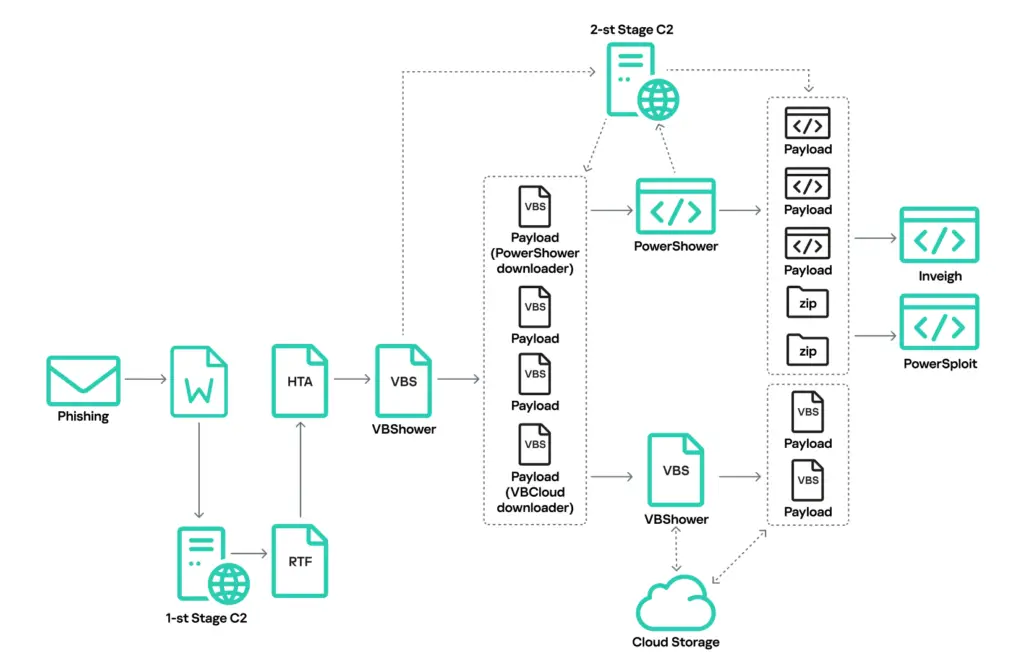
“The infection scheme was originally described back in 2019 and has changed only slightly from year to year,” the report states. This consistency, combined with incremental updates, reflects Cloud Atlas’s focus on refinement rather than reinvention.
VBShower acts as the initial loader, extracting and running the VBCloud backdoor. VBCloud, in turn, collects system information, exfiltrates files, and communicates with the C2 server. Its functionality mirrors that of VBShower, with key enhancements to avoid detection.
“VBCloud uses public cloud storage as its C2 server,” Kaspersky notes, making it more resilient and difficult to track. Once installed, VBCloud retrieves encrypted payloads from the C2 server, decrypts them, and executes the scripts in memory. These payloads include PowerShell-based utilities for system reconnaissance, data collection, and even brute-force attacks.
One notable script from VBCloud targets Telegram files, exfiltrating user IDs and encryption keys stored locally, thereby compromising sensitive communications.
Cloud Atlas remains highly targeted in its operations, with 82% of victims located in Russia. Other affected regions include Belarus, Canada, Moldova, and Kyrgyzstan. The group employs custom tools for each victim, further complicating detection and analysis.
“This underscores the still-pressing need for organizations to strengthen their infrastructure defenses and improve employee awareness to ward off these kinds of attacks,” the report concludes.
Related Posts:
- Data Breach Alert: MongoDB Customer Hit, Logs Accessed
- ATLAS LION Cybercriminal Group Persists in Targeting Gift Card Issuing Systems
- Cyber-Espionage Campaign Unveiled: Operation Cobalt Whisper Hits Sensitive Industries
- Kaspersky Report: Criminals earning millions through mining malware