Cloud Custodian v0.9.32 releases: Rules engine for cloud security
Cloud Custodian
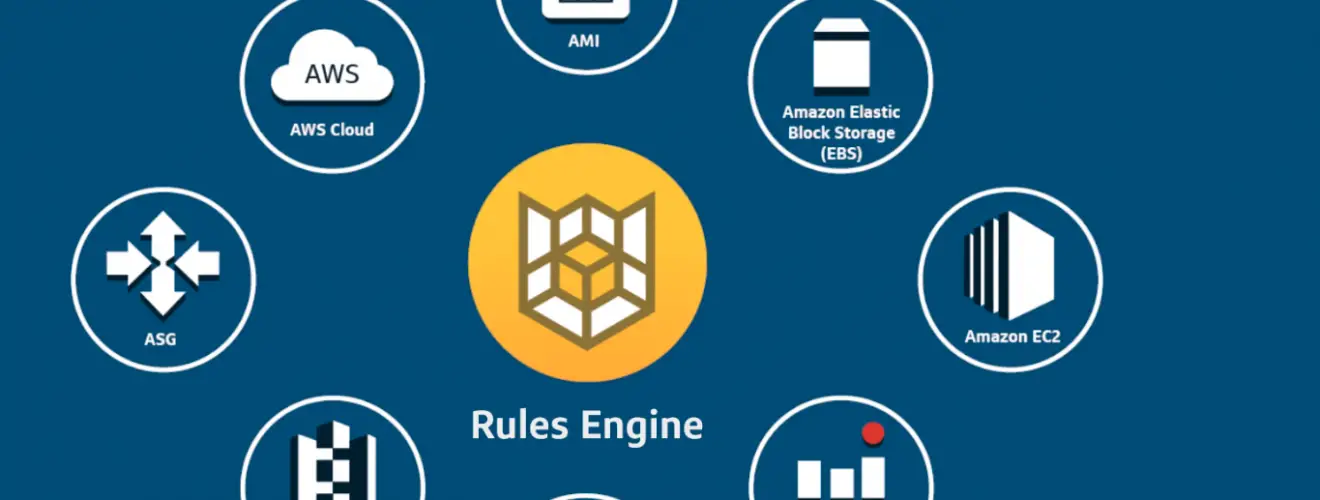
Cloud Custodian is a rules engine for managing public cloud accounts and resources. It allows users to define policies to enable a well-managed cloud infrastructure, that’s both secure and cost-optimized. It consolidates many of the adhoc scripts organizations have into a lightweight and flexible tool, with unified metrics and reporting.
Custodian can be used to manage AWS, Azure, and GCP environments by ensuring real-time compliance to security policies (like encryption and access requirements), tag policies, and cost management via garbage collection of unused resources and off-hours resource management.
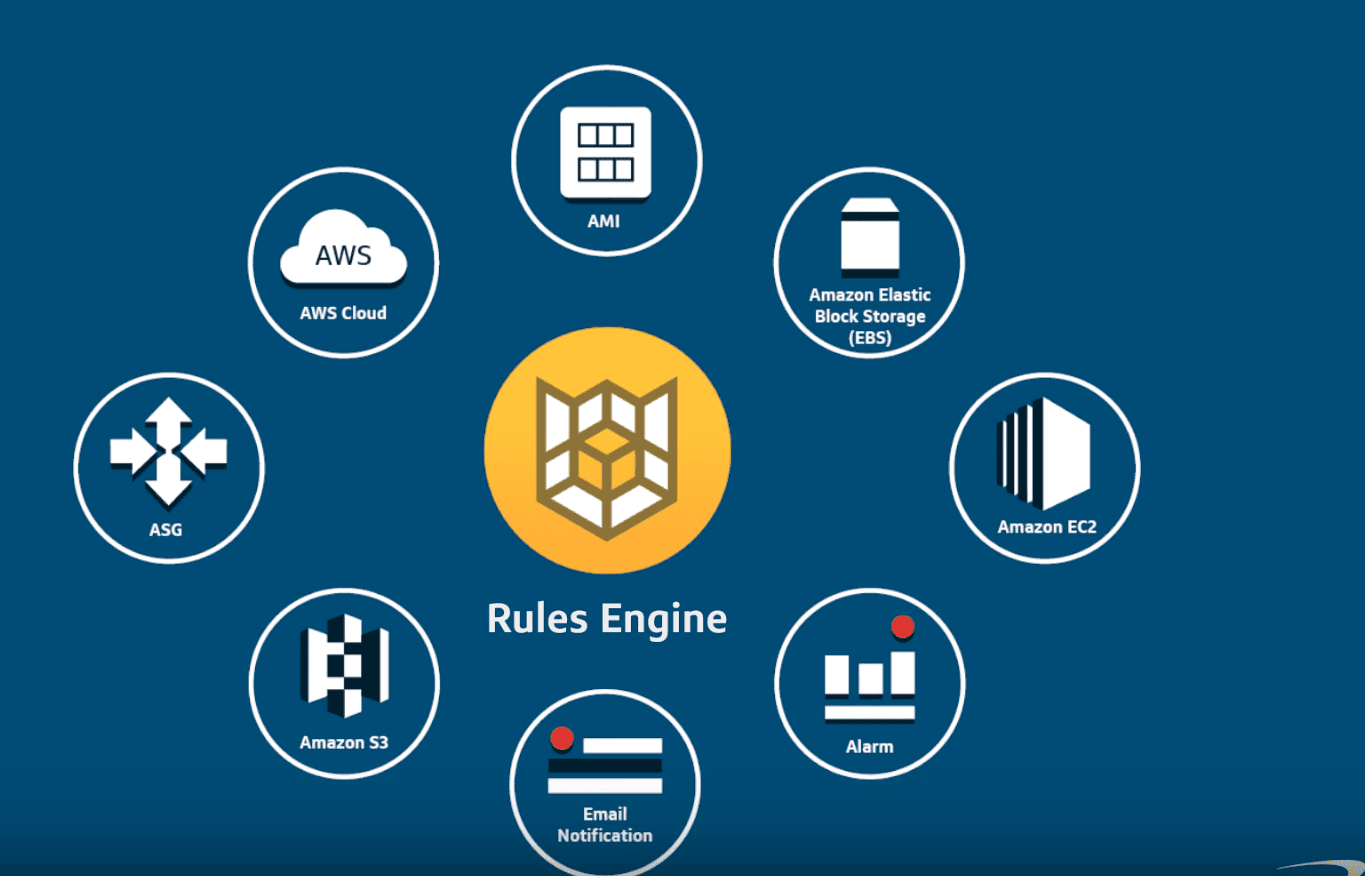
Custodian policies are written in simple YAML configuration files that enable users to specify policies on a resource type (EC2, ASG, Redshift, CosmosDB, PubSub Topic) and are constructed from a vocabulary of filters and actions.
It integrates with the cloud-native serverless capabilities of each provider to provide for real-time enforcement of policies with built-in provisioning. Or it can be run as a simple cron job on a server to execute against large existing fleets.
“Engineering the Next Generation of Cloud Governance” by @drewfirment
Features
- Comprehensive support for public cloud services and resources with a rich library of actions and filters to build policies with.
- Supports arbitrary filtering on resources with nested boolean conditions.
- Dry run any policy to see what it would do.
- Automatically provisions serverless functions and event sources ( AWS CloudWatchEvents, AWS Config Rules, Azure EventGrid, GCP AuditLog & Pub/Sub, etc)
- Cloud provider native metrics outputs on resources that matched a policy
- Structured outputs into cloud-native object storage of which resources matched a policy.
- Intelligent cache usage to minimize api calls.
- Supports multi-account/subscription/project usage.
- Battle-tested – in production on some very large cloud environments.
Changelog v0.9.32
aws
- aws – airflow – update-environment and delete-environment (#8866)
- aws – app-elb-target-group – retry wrapper for describe_target_group_attributes (#8916)
- aws – ec2 – use a list instead of tuple for empty tag set (#8957)
- aws – eip – release – handle InvalidAddress.PtrSet and InvalidAddress.Locked exception (#8924)
- aws – elasticache and rg skip deletion when linked with global ds (#8876)
- aws – glue catalog – kms-key filter and set-encryption refactor (#8833)
- aws – inspector-v2 finding resource (#8934)
- aws – launch-template-version – include version number in synthetic arn (#8972)
- aws – metrics filter – support client side evaluation across multiple periods (#8930)
- aws – output – metrics – allow enabling specific metrics and ignore zero values via query params (#8929)
- aws – route53 – fix arn handling in query-logging-enabled filter (#8988)
- aws – s3 – only check account-local trails in data-events filter (#8960)
- aws – service-quotas – request-increase fix (#8939)
- aws – sns – fix metrics filter get_dimensions for topics (#8951)
- aws – vpc – delete-empty action (#8854)
- aws – waf and vpc – reduce noise from deprecated field validation (#8919)
awscc
- awscc – use build step to fetch data files (#8840)
azure
- azure – cdn – update package version (#8979)
- azure – key vault – filter to check rotation policy (#8905)
core
- core – offhours allow escaped
-via ordinal hex (#8808) - core – value – support float value_type (#8927)
docs
- docs – aws – fix event filter example to use op: contains (#8959)
- docs – clarify conditions behavior on serverless policies (#8933)
- docs – cover list-item under generic filters (#9005)
- docs – flesh out mailer config, plus various formatting/clarity fixes (#8944)
gcp
- gcp – bq-job – update enum_spec (#8994)
- gcp – cloud-run iam-policy filter (#8978)
- gcp – dns zone – records filter (#8829)
- gcp – kms keyring filter (#8903)
- gcp – node pool and cluster – server-config filter (#8880)
- gcp – org – policy filter (#8982)
- gcp – organization and folder iam policy filter (#9006)
- gcp – spanner-backup: iam filter (#8938)
- gcp – sql instance – set ha action for zonal/regional configuration (#8967)
- gcp – vpc-firewall-filter (#8901)
oci
- oci – implement resource caching (#8869)
releng
- releng – prep 0.9.32 (#9003)
- releng – update custodian version in dependent packages (#9025)
- releng – update data dictionaries (#8820)
- releng – update dependencies (#8985)
- releng – update dependencies (#9022)
shift-left
- c7n-left – cli entrypoint point reporter parameter (#9002)
- c7n-left – default provider tags augment, handle empty resource tags (#8954)
- c7n-left – dump cli command to show graph and input variables (#8974)
- c7n-left – fix handling of relative source dir (#8993)
- c7n-left – gitlab sast output (#8923)
- c7n-left – handle null provider tags when augmenting (#8984)
- c7n-left – initialize variables with default value if none provided (#8958)
- c7n-left – junit xml output (#8931)
- c7n-left – only consider root module variables when injecting uninitialized defaults (#8995)
Install && Use
Copyright 2015-2017 Capital One Services, LLC