Cluster Scanner: Discover vulnerabilities and container image misconfiguration
Cluster Scanner
The Cluster Scanner detects images in a Kubernetes cluster and provides fast feedback based on various security tests. It is recommended to run the Cluster Scanner in production environments in order to get up-to-date feedback on security issues where they have a real impact.
Since the Cluster Scanner itself is a service running within your Kubernetes cluster you can re-use your existing deployment procedures.
Overview
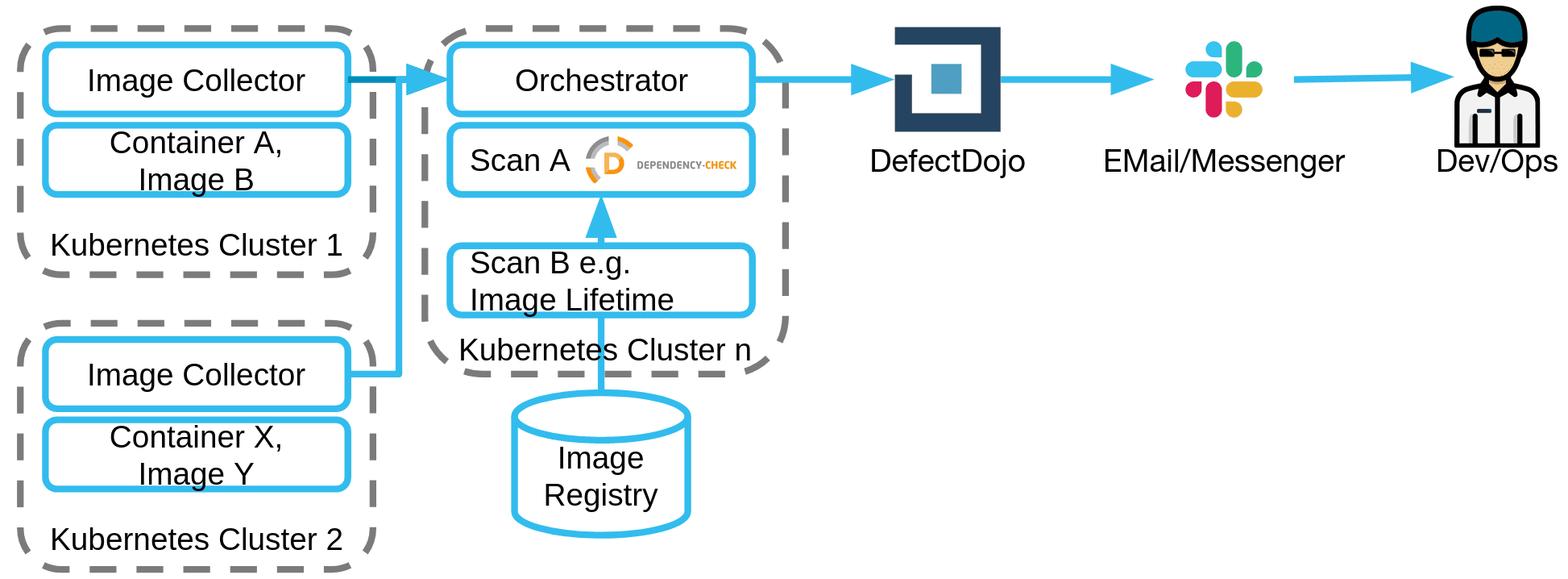
The following figure provides an overview:
The following steps are conducted.
- The Image Collector, as the name suggests, collects the different images from a container environment like a kubernetes cluster. The Collector creates a JSON file and including information like the cluster, the responsible team, and image.
- The Orchestrator (implemented via ArgoWorkflows) starts the workflow periodically (e.g. nightly)
- The images from the Collector can be pulled by the Image Fetcher
- These files are kept in a separate directory and from there they are passed to the scanner
- This scanner – which then receives the libraries to be ignored via the suppressions file – then executes the scans described in the definitions of Dependency-Check, Lifetime, Virus, and furthermore.
- The vulnerability management system (in our case OWASP DefectDojo) then collects the results
- Non-responded to findings are made available to the developers via a communication channel (Slack/Email).
Install & Use
Copyright (c) 2021 SDA SE





