Cohab Processes: identify foreign processes on a host machine
Cohab_Processes
This Aggressor script is intended to help internal Red Teams identify suspicious or foreign processes (“Cohabitation”) running in their environments.
Red Teams may assemble a list of “known” processes (either independently or in collaboration with Blue force) and feed it to the aggressor script. This list of processes might include those seen “at least x times in our network” in order to establish a baseline. Once the script has been loaded into CobaltStrike, beacon output will be altered/color coded for the following commands:
- shell tasklist
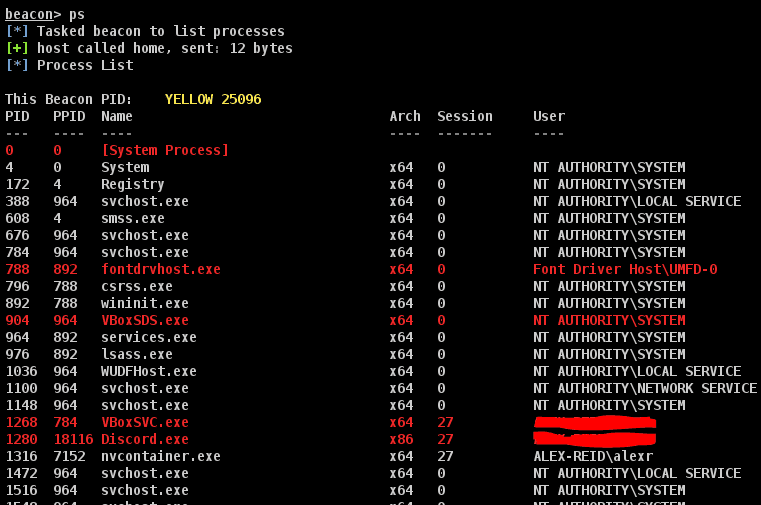
- ps
- TrustedSec’s tasklist BOF (You do not have to use this BOF, but it is highly recommended)
Any processes returned as output from the above commands that are NOT found on the “known” processes list will be highlighted in RED for further investigation/scrutiny.
shell tasklist:

ps:

TrustedSec tasklist BOF:

Limitations
This methodology for identifying potential cohabitation IS severely limited. It will not for example identify or catch things like:
- Process injection- where malware has been injected into and is running in a legitimate, “known” process.
- DLL sideloading or hijacking- where malware has been loaded by a legitimate, “known” process by residing in a DLL that the process loads/runs.
This script serves as a way to help catch the “low hanging fruit”.





