Compromised Routers: Tool of Choice for Crime & Espionage

A new report by TrendMicro lifts the veil on the shadowy world of router exploitation. Those unassuming internet gateways, often overlooked in cybersecurity discussions, have become a prime battleground where criminals and nation-state hackers alike wage their clandestine campaigns. TrendMicro’s analysis uncovers a disturbing pattern: compromised routers are being weaponized across the threat landscape to mask nefarious activity and launch a wide range of attacks.
The report highlights an alarming trend where cybercriminals and Advanced Persistent Threat (APT) groups, such as Pawn Storm (also known as APT28 or Forest Blizzard), exploit the same infrastructure, namely compromised routers, for their nefarious purposes. This shared usage includes a range of malicious activities from espionage campaigns to financial fraud, all conducted through a common anonymization layer provided by proxy servers and VPN nodes.
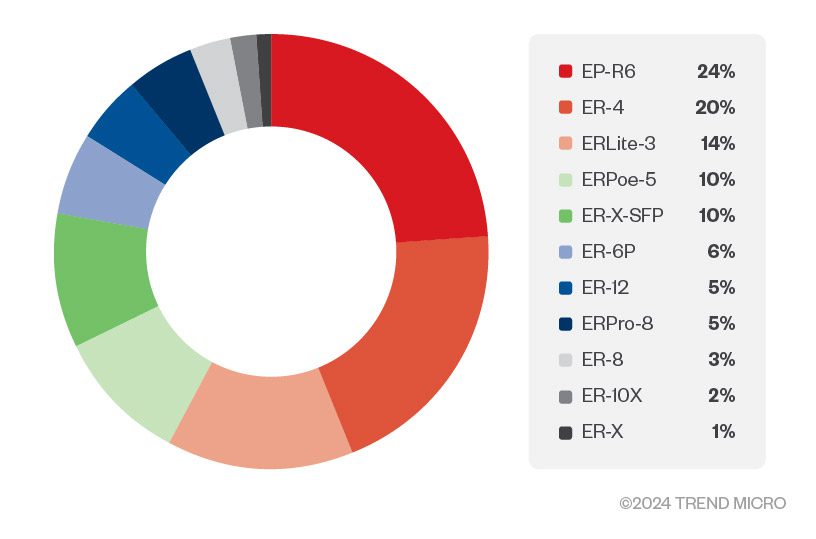
Compromised EdgeRouter devices distribution by model number
A striking example provided in the report involves compromised Ubiquiti EdgeRouter devices that have been operational since at least 2016. Initially commandeered by a cybercriminal botnet for activities such as SSH brute forcing, spamming, and cryptocurrency mining, these routers were later exploited by Pawn Storm for more sinister purposes. The report details how this APT group used the botnet for persistent espionage campaigns, leveraging the routers as a stealthy conduit for their operations.
The botnet’s significance came into full view when the FBI, in collaboration with international partners, disrupted its operations in January 2024. The law enforcement action involved modifying the code and settings on the compromised devices. However, the report notes that due to legal and technical limitations, not all routers were cleansed of the malicious software, and some were quickly repurposed into a new command and control infrastructure by the original operators.

Statistics on Monero mining by a pool of VPS servers
Despite the disruption, the resilience of these compromised networks is noted, with new C&C infrastructures popping up and additional types of devices, such as Raspberry Pi and datacenter VPS, being implicated. The report also unveils another malware, Ngioweb, found running on some of the same compromised routers. Ngioweb, operating entirely from memory and thus leaving minimal traces, is being used to power a commercial residential proxy botnet.
The TrendMicro report suggests several strategies for organizations to protect themselves. These include regular updates to router firmware, changing default credentials, and monitoring network traffic for anomalies. Additionally, understanding the indicators of compromise specific to these threats can help in the early detection and prevention of breaches.