audit_scripts
Scripts to help work with configuration audit files.
baseline/create_baseline_audit.py
The create_baseline_audit.py script is used to take the values from a provided .nessus file, and combine them as known_good values in a .audit file.
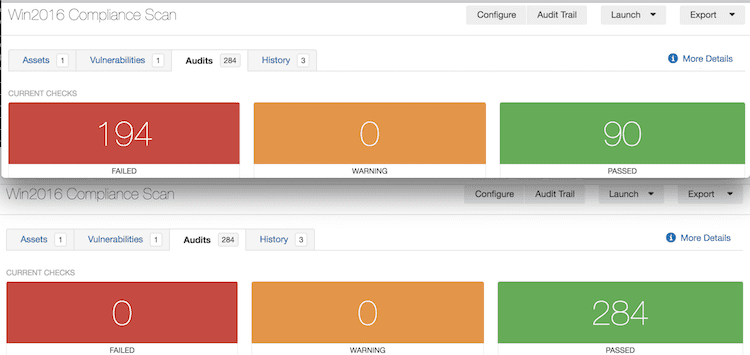
The example below shows a compliance scan using a CIS benchmark on a Windows 2016 target. The top results are from the original scan, and the bottom results are from a baseline scan with the audit created from the results of the first scan.

Some things to consider:
- Original audit file should not have known_good values existing in it.
- Best results when used with the same audit file that was used in the first scan, and only one audit file per scan.
- Actual values are not applied to checks that are within the conditional sections of audit if/then/else structures. This was done to maintain consistency with the conditional logic.
- Any checks that use custom commands, such as CMD_EXEC or SQL_POLICY, may have inconsistent or unsupported output. SQL statements may return values in different orders if not sorted or system commands may output Unicode characters in their output. If developing checks, consider sorting output where possible into a consistent order and sanitizing any non-ascii characters from the output.
- Values that have both single and double quotes in the value will be placed in known_good fields using double quotes and escaping the instances of double quotes in the value. This should support most plugins.
- Checks that use static report items to post a WARNING or FAILED will not be modified by known_good values.
The script was tested using .nessus files exported from Tenable.IO and Nessus Pro.
There are a number of use cases that this could be used for.
- Baseline Scanning: Create a system that represents your baseline against the company auditing policy, and scan this system with the audit file. Use the script to record the configuration of your Baseline Reference Audit and scan all other systems with the new audit file to compare the configuration against the baseline. This can identify any systems that may need remediation actions.
- Change Identification: On a single server, create an audit file to monitor the parts of the system that must be monitored for changes, and create your baseline reference audit file by scanning the server with your audit file. To capture the current state of the server, use the script to create your baseline audit file, and schedule a periodic scan of the server with the new audit file. In any instance that the scan identifies a failed check, there must have been an actor that made a change to the system.
variables/replace_variables.py
The view_audit_structure.py script is used to visualize the structure of the audit file, most notably the conditional logic of the audit file.
When looking at a downloaded audit file, there is a section in the comment header that defines variables. The use of these variables are for providing custom input when using Tenable products, and will have no impact when uploading the audit file as a custom audit.
This script is provided as-is to attempt to assist in the debugging of audit files.
structure/view_audit_structure.py
The replace_variables.py script is used to take the values from the out variable definition in the header and place the values in the audit file. This was a test using a custom audit file and an audit file that was downloaded from the Tenable download site.
When looking at a downloaded audit file, there is a section in the comment header that defines variables. The use of these variables are for providing custom input when using Tenable products and will have no impact when uploading the audit file as a custom audit.
This script is provided as-is to attempt to make the update of values in the audit file a bit more simple.
Download && Use
Copyright (c) 2018 Tenable Network Security, Inc.