Image: Forescout Research – Vedere Labs
A newly exposed attack campaign, dubbed “Connect:fun,” is raising alarms in the media sector. Researchers at Forescout Research – Vedere Labs warn that a sophisticated threat actor is exploiting a critical Fortinet vulnerability to gain deep access to targeted organizations. The campaign’s focus on media companies raises the possibility of motivations beyond traditional cybercrime.

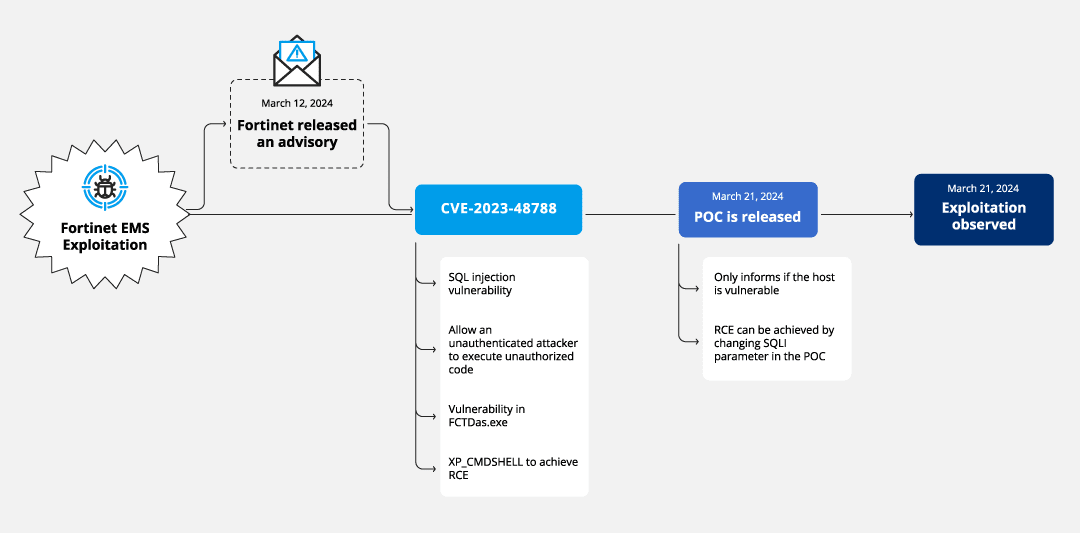
On March 12, 2024, Fortinet released an advisory about CVE-2023-48788, which is present in their FortiClient EMS security management solution. This vulnerability allows for SQL injection, a dangerous exploit where attackers can interfere with the queries that an application makes to its database. Just nine days later, the cybersecurity community saw the release of a Proof of Concept (PoC) exploit, which quickly translated into real-world attacks. By March 25, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) had added CVE-2023-48788 to its list of Known Exploited Vulnerabilities, underscoring the severity of the issue.
One notable incident occurred when a media company’s FortiClient EMS, exposed to the internet, became a target. Initial attempts to exploit the system on March 21 were unsuccessful due to syntax errors by the attackers. However, persistence paid off for the attackers who, two days later, attempted further SQL injections and successfully deployed the ScreenConnect remote management tool and a script based on the open-source Powerfun module, which includes capabilities for creating reverse and bind shells and executing arbitrary commands.
The domain name “ursketz[.]com” was used in the attacks, with multiple SQL statements attempting to download ScreenConnect, indicating a well-planned and orchestrated attack.
Similar activities targeting other organizations with FortiClient EMS and other VPN appliances have been observed. The same IP addresses and domains involved in the attack on the media company have been seen in other incidents dating back to 2022. The attackers appear to be using infrastructure spread across multiple countries and are proficient in both Vietnamese and German, suggesting a sophisticated, multilingual threat actor.
Furthermore, the continuous scanning activity from specific IP addresses and the deliberate targeting of organizations suggest a campaign that is more selective and manually driven, unlike the broad, automated sweeps seen in many other cyberattack campaigns.
To defend against such sophisticated threats, organizations using FortiClient EMS are advised to take several proactive steps:
- Apply Patches: Immediately apply any security patches released by Fortinet.
- Monitor Traffic: Use intrusion detection systems (IDS) to continuously monitor the traffic reaching FortiClient EMS for signs of exploitation.
- Implement WAF: Deploy a web application firewall (WAF) to block potentially malicious requests.
- Leverage IoCs: Utilize the indicators of compromise (IoCs) and tactics, techniques, and procedures (TTPs) provided by cybersecurity researchers to enhance threat detection and hunting within network environments.