Contagious Interview & WageMole: North Korea’s New Cyber Espionage Campaigns
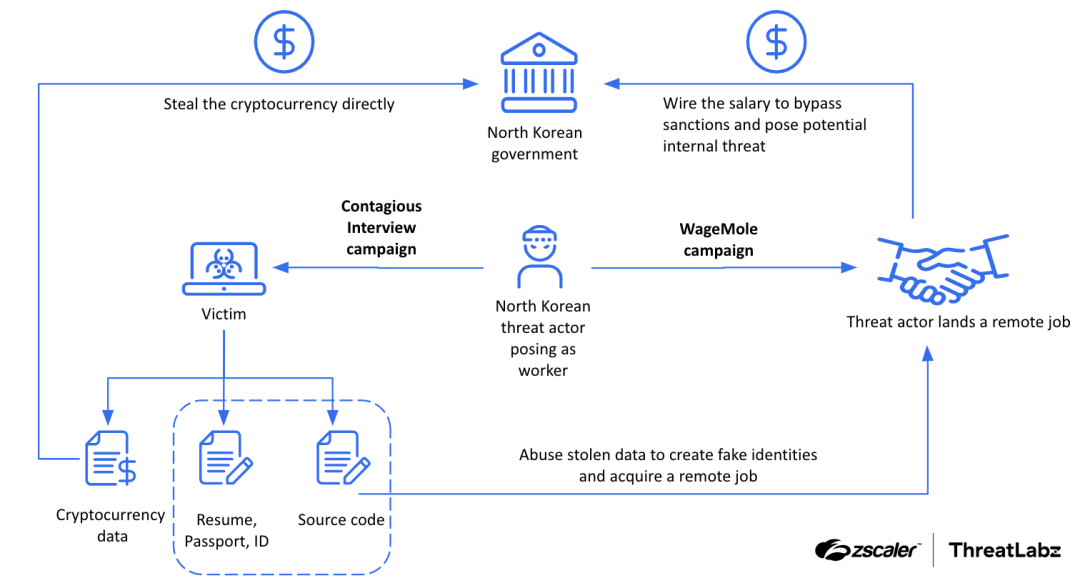
In a recent report, Zscaler ThreatLabz uncovers the creative yet deceptive strategies used by North Korean threat actors to infiltrate Western job markets. Through two interconnected campaigns—Contagious Interview and WageMole—these cyber operatives secure remote employment in industries like IT and cryptocurrency, bypassing economic sanctions while exfiltrating sensitive data.
The Contagious Interview campaign uses social engineering to target developers on platforms like GitHub, Freelancer, and LinkedIn. ThreatLabz explains, “The threat actors aggressively contact potential victims through social media platforms, focusing on web, cryptocurrency, and AI developers”. They set up fake job listings, often requiring candidates to complete coding assignments through GitHub repositories they control. Within these repositories lies BeaverTail, a JavaScript-based malware that initially infects the applicant’s system.
Once installed, BeaverTail deploys a secondary script called InvisibleFerret, a Python-based backdoor. InvisibleFerret allows the attackers to keylog, capture clipboard content, and even monitor browser data. Through these scripts, attackers can steal “source code, cryptocurrency data, and personal information from victims,” and can initiate further exfiltration depending on the victim’s potential value.
WageMole takes this deception further by enabling North Korean operatives to secure legitimate jobs in Western companies using fake credentials. According to Zscaler’s findings, these operatives often create “fake identities” by altering or purchasing stolen driver’s licenses, passports, and resumes. With the assistance of generative AI, they craft professional answers to interview questions and fine-tune their resumes to pass screening processes.
The report details that “These threat actors prefer LinkedIn for finding job opportunities,” creating profiles under assumed identities with technical titles like full-stack developer and AI engineer. They aggressively pursue remote roles and small to mid-sized companies, where background checks may be less stringent. Once hired, they can collect valuable data, from source code to internal processes, and funnel earnings back to North Korea.
Both campaigns show a keen understanding of modern security protocols and detection methods. For example, BeaverTail and InvisibleFerret use advanced obfuscation to evade monitoring. The report notes, “BeaverTail has adopted a new obfuscation technique… utilizing a JavaScript-obfuscator to mask its strings and functions,” making it harder for security teams to detect. Additionally, InvisibleFerret operates cross-platform, targeting both Windows and macOS, further expanding its reach.
The rise of North Korean cyber operatives in Western remote workforces underscores the evolving complexity of state-sponsored cyber operations. Zscaler’s report urges companies to strengthen their verification processes and conduct thorough background checks to mitigate these risks. As these campaigns show, cybersecurity isn’t only about protecting networks; it’s also about safeguarding personnel processes to prevent adversaries from securing a place within trusted teams.
Related Posts:
- North Korean Hackers Launch Job Interview Scam to Deploy BeaverTail and InvisibleFerret Malware
- Developers Targeted: North Korean Hackers Deploy “BeaverTail” Malware via NFTsNorth Korean Threat Actors Targeting Tech Job Seekers with Contagious Interview Campaign
- Zhao’s Bribes Unveiled: Selling US Navy’s Critical Secrets





