Copybara fraud operation
Cleafy‘s recent analysis of the Copybara campaign highlights a troubling escalation in online banking fraud. Threat actors (TAs) are weaponizing a combination of social engineering, phishing infrastructure, and an advanced Android banking trojan to bypass traditional anti-fraud defenses.
Account Takeover (ATO) fraud has long been a thorn in the side of the digital banking industry, with a staggering 90% of fraud attempts attributed to this method. Despite the banking sector’s efforts to clamp down on these breaches, ATO attacks remain a preferred strategy for cybercriminals, driven by the lure of immediate financial gain.
On-Device Fraud (ODF) has emerged as a formidable challenge, bypassing traditional detection mechanisms with alarming ease. Unlike conventional fraud methods, ODF operates directly through the victim’s device, leveraging the functionalities of modern Android banking trojans like Vultur, TeaBot, and SpyNote. These malicious tools, equipped with remote control capabilities, enable cybercriminals to conduct their illicit activities stealthily, rendering standard anti-fraud measures ineffective.
Unraveling the Campaign
The Copybara campaign unfolds in a series of meticulously executed stages:

- Social Engineering Onslaught: TAs initiate contact through smishing or vishing, employing native-language operators to enhance the credibility of their lures.
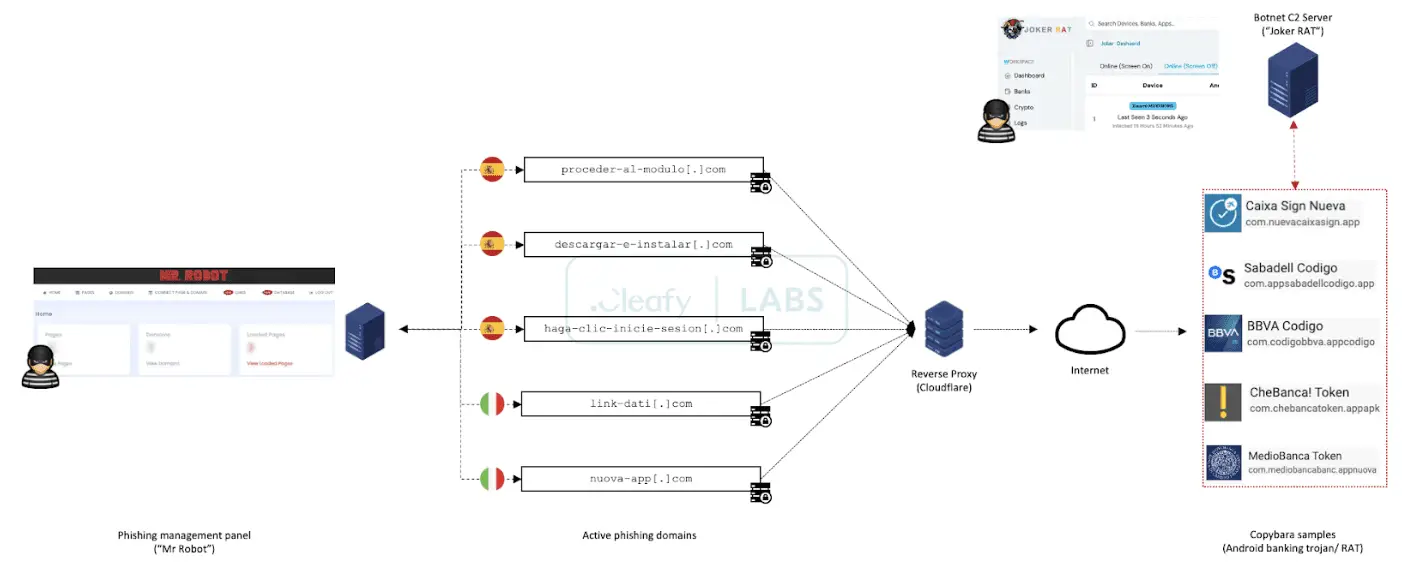
- “Mr. Robot” Phishing Orchestration: A tailored C2 panel manages multiple simultaneous phishing campaigns, each designed to mimic the targeted banks’ interfaces. This allows TAs to strike a wide range of financial institutions in Italy, Spain, and the UK.
- Android Assault: If a potential victim is detected to be using an Android device, the focus shifts to deploying the Copybara banking trojan. Social engineering scripts are used to convince the user to install the malicious app.
- ODF Execution: Once installed, Copybara provides attackers with remote control over the device (VNC). Fraudulent transactions are then initiated directly on the compromised device, bypassing the typical signals that fraud systems rely upon.
Technical Analysis: Mechanisms and Challenges
- “Mr. Robot” C2 Evasion: Geolocation checks, device fingerprinting, and abuse of CDNs/reverse proxies are deployed to hinder takedown attempts and obscure the location of the command and control infrastructure.
- Copybara Capabilities:
- Accessibility Permissions Abuse: Vital for keystroke recording, screen monitoring, and manipulating app interfaces.
- Remote Control (VNC): Enables direct interaction with the device – the key to effective ODF.
- Overlay Attacks: Simulates legitimate bank login forms to harvest credentials.
- SMS Interception: Defeats SMS-based 2FA for some financial institutions.
- Fake Notifications: Can mimic bank messages, increasing the effectiveness of social engineering lures.
- JOKER RAT Control Panel: Provides attackers with a centralized dashboard for botnet management and granular control over individual infected devices.
The Evolving Fight Against ODF
The Copybara operation is a stark reminder that on-device fraud is no longer a theoretical threat but a very real danger. Financial institutions and the security community must act decisively to address this challenge. This requires a multifaceted approach: user education, investment in advanced fraud detection technology, and a commitment to threat intelligence exchange across the industry.