Infection flow diagram
Researchers at Cisco Talos have uncovered a sophisticated cybercrime operation dubbed “CoralRaider,” pinpointing the threat actors as likely based in Vietnam. This group’s attacks are marked by uncommon techniques and a ruthless focus on stealing credentials, financial information, and social media account data from victims across Asia.
CoralRaider’s roots trace back to Vietnam, with Cisco Talos attributing high confidence to this geographical origin based on language preferences, IP addresses, and other digital breadcrumbs left behind in their cyber escapades. This financially motivated group has meticulously crafted a campaign that leverages the sophisticated malware strains RotBot and XClient stealer, targeting individuals and businesses across multiple countries, including India, China, South Korea, Bangladesh, Pakistan, Indonesia, and Vietnam.

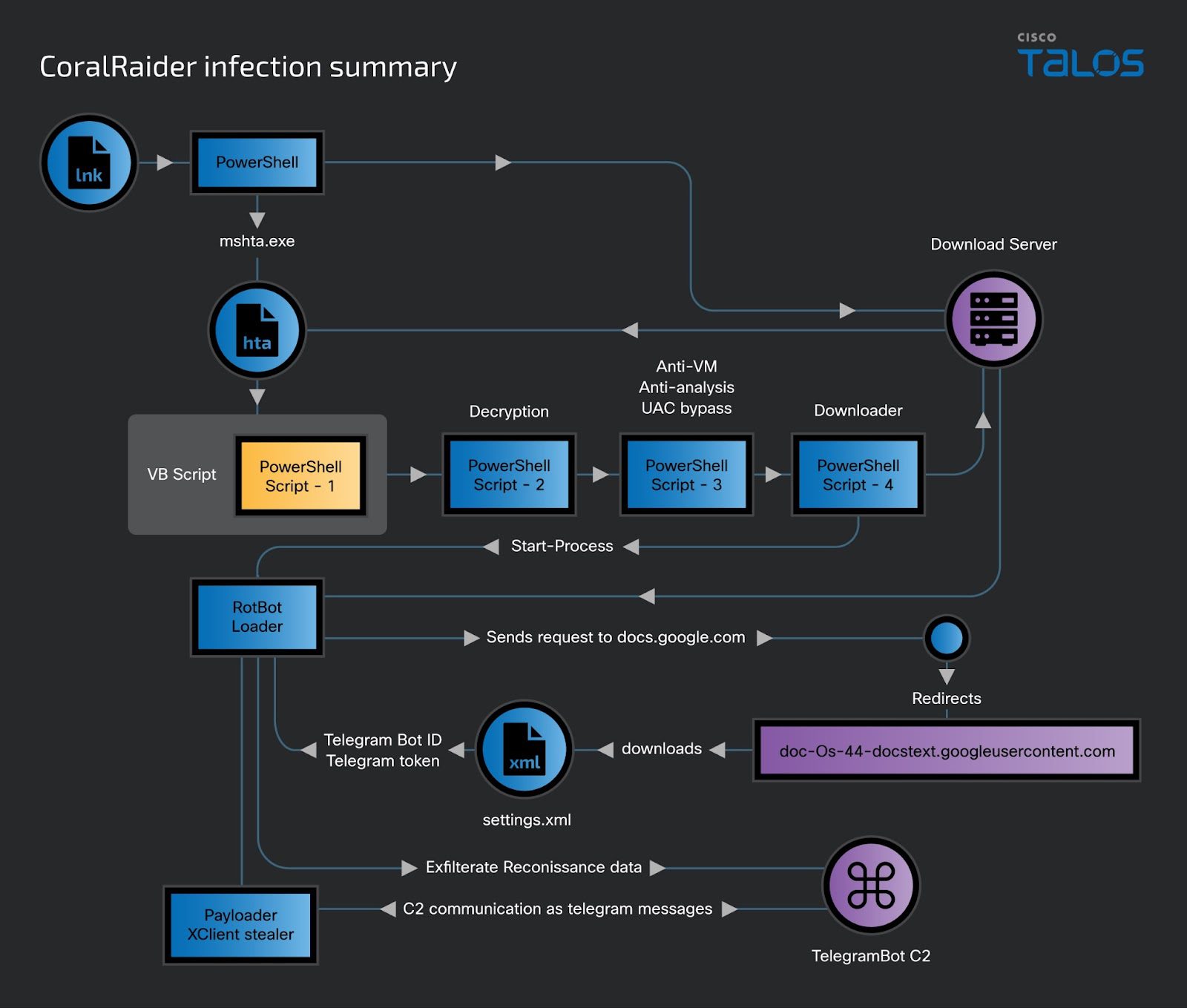
At the heart of CoralRaider’s strategy is the deployment of malicious Windows shortcut files (.LNK) as the initial attack vector. These files, once activated, set off a domino effect—downloading an HTML application file that executes a series of obfuscated scripts. This meticulous orchestration ensures the stealthy delivery of RotBot onto the victim’s machine. RotBot, a customized variant of QuasarRAT, serves as the trojan horse, opening the gates for the XClient stealer to infiltrate and plunder the victim’s digital treasure trove.
Abusing Telegram bots as command-and-control (C&C) servers is an unusual technique. Similarly, the group uses ‘dead drops’ – legitimate online services hijacked to discreetly store commands and stolen data. These tactics add a layer of obscurity for the attackers.
CoralRaider even employs common Windows tools like Forfiles.exe and FoDHelper.exe, making their operations blend in seamlessly with ordinary background system activity.
CoralRaider’s relentless targeting of social media accounts underscores the shifting attack landscape:
- Facebook Under Siege: XClient is specifically designed to raid Facebook user data, particularly from Business and Ads accounts. Access tokens, friend lists, advertising spend – nothing seems off-limits to the group.
- The Wider Web: Instagram, TikTok Business, and YouTube are also on their radar, with XClient capable of extracting account details and potentially sensitive content.
- Local Apps Targeted: Information stored by desktop clients of Telegram and Discord could prove valuable for social engineering attacks and identity theft, leading CoralRaider to target these applications.
Cisco Talos’ analysis reveals compelling clues that point to the group’s Vietnamese origin:
- Language Trails: Vietnamese terms appear both in the malware itself and within Telegram groups where stolen data is likely traded.
- Slip-ups Happen: Images within the attacker’s C&C bot provide a glimpse of their system, inadvertently revealing Vietnamese language file paths and a possible online alias connected to CoralRaider activities.
- Tracking the IP: A core IP address utilized in CoralRaider’s infrastructure was traced directly to Hanoi, Vietnam, further solidifying the connection.
For individuals and organizations in the targeted regions, the rise of CoralRaider signifies an urgent need to fortify defenses, educate about the dangers of phishing attacks, and implement advanced security measures to detect and neutralize such threats.