CORScanner v1.0.1 releases: Fast CORS misconfiguration vulnerabilities scanner
About CORScanner
CORScanner is a python tool designed to discover CORS misconfigurations vulnerabilities of websites. It helps website administrators and penetration testers to check whether the domains/urls they are targeting have insecure CORS policies.
The correct configuration of CORS policy is critical to website security, but CORS configurations have many error-prone corner cases. Web developers who are not aware of these corner cases are likely to make mistakes. Thus, we summarize different common types of CORS misconfigurations and integrate them into this tool, to help developers/security-practitioners quickly locate and detect such security issues.

Features
- Fast. It uses gevent instead of Python threads for concurrency, which is much faster for network scanning.
- Comprehensive. It covers all the common types of CORS misconfigurations we know.
- Flexible. It supports various self-define features (e.g. file output), which is helpful for large-scale scanning.
Misconfiguration types
This tool covers the following misconfiguration types:
| Misconfiguration type | Description |
|---|---|
| Reflect_any_origin | Blindly reflect the Origin header value in Access-Control-Allow-Origin headers in responses, which means any website can read its secrets by sending cross-origin requests. |
| Prefix_match | wwww.example.com trusts example.com.evil.com, which is an attacker’s domain. |
| Suffix_match | wwww.example.com trusts evilexample.com, which could be registered by an attacker. |
| Not_escape_dot | wwww.example.com trusts wwwaexample.com, which could be registered by an attacker. |
| Substring match | wwww.example.com trusts example.co, which could be registered by an attacker. |
| Trust_null | wwww.example.com trusts null, which can be forged by iframe sandbox scripts |
| HTTPS_trust_HTTP | Risky trust dependency, a MITM attacker may steal HTTPS site secrets |
| Trust_any_subdomain | Risky trust dependency, a subdomain XSS may steal its secrets |
| custom_third_parties | Custom unsafe third parties origins like github.io, see more in origins.json file. Thanks @phackt! |
Installation
git clone https://github.com/chenjj/CORScanner.git
sudo pip install -r requirements.txt
Usage
| Short Form | Long Form | Description |
|---|---|---|
| -u | –url | URL/domain to check it’s CORS policy |
| -i | –input | URL/domain list file to check their CORS policy |
| -t | –threads | Number of threads to use for CORS scan |
| -o | –output | Save the results to a text file |
| -v | –verbose | Enable the verbose mode and display results in real-time |
| -h | –help | show the help message and exit |
Examples
- To check CORS misconfigurations of a specific domain:
python cors_scan.py -u example.com
- To check CORS misconfigurations of specific URL:
python cors_scan.py -u http://example.com/restapi
- To check CORS misconfigurations of multiple domains/URLs:
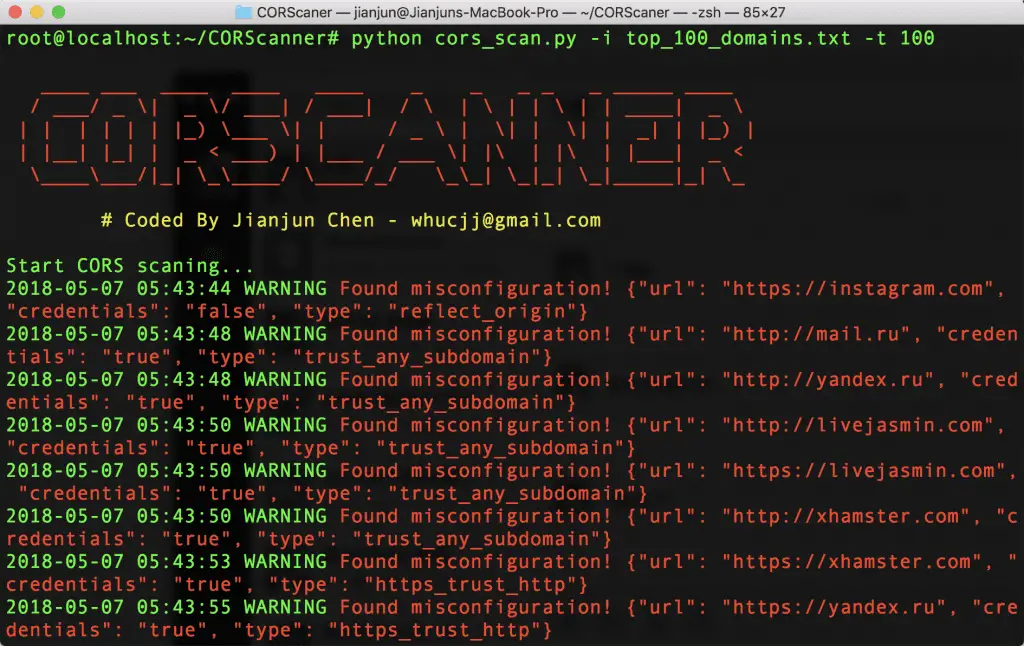
python cors_scan.py -i top_100_domains.txt -t 100
- To list all the basic options and switches use -h switch:
python cors_scan.py -h
Demo
Copyright (c) 2018 Jianjun Chen
Source: https://github.com/chenjj/





